Contents:
Even if we can consider the pretense ironic, the situation can be very risky as it can actually end up deploying infostealer malware on the victim machine.
An infostealer is a type of malware focused on gathering sensitive and conditional information from a compromised system.
It is often related to user’s credentials but has also been known to look for financial and personal information.
Most infostealer malware is sold as Malware-As-A-Service (MaaS) thus allowing cybercriminals to provide a fully working package to their “customers” that also includes access to a technical support team.
MaaS is a type of malware developed by cybercriminals to require little or no expertise in hacking, to be flexible, polymorphic, offer a broader reach, and often comes packed with ready-coded targets. Malware-as-a-service can be bought or rented on the deep web and in cybercriminal communities, and sometimes can even include technical support from its makers and their team, which they run as a business. The main purpose behind it is to make as much money as possible.
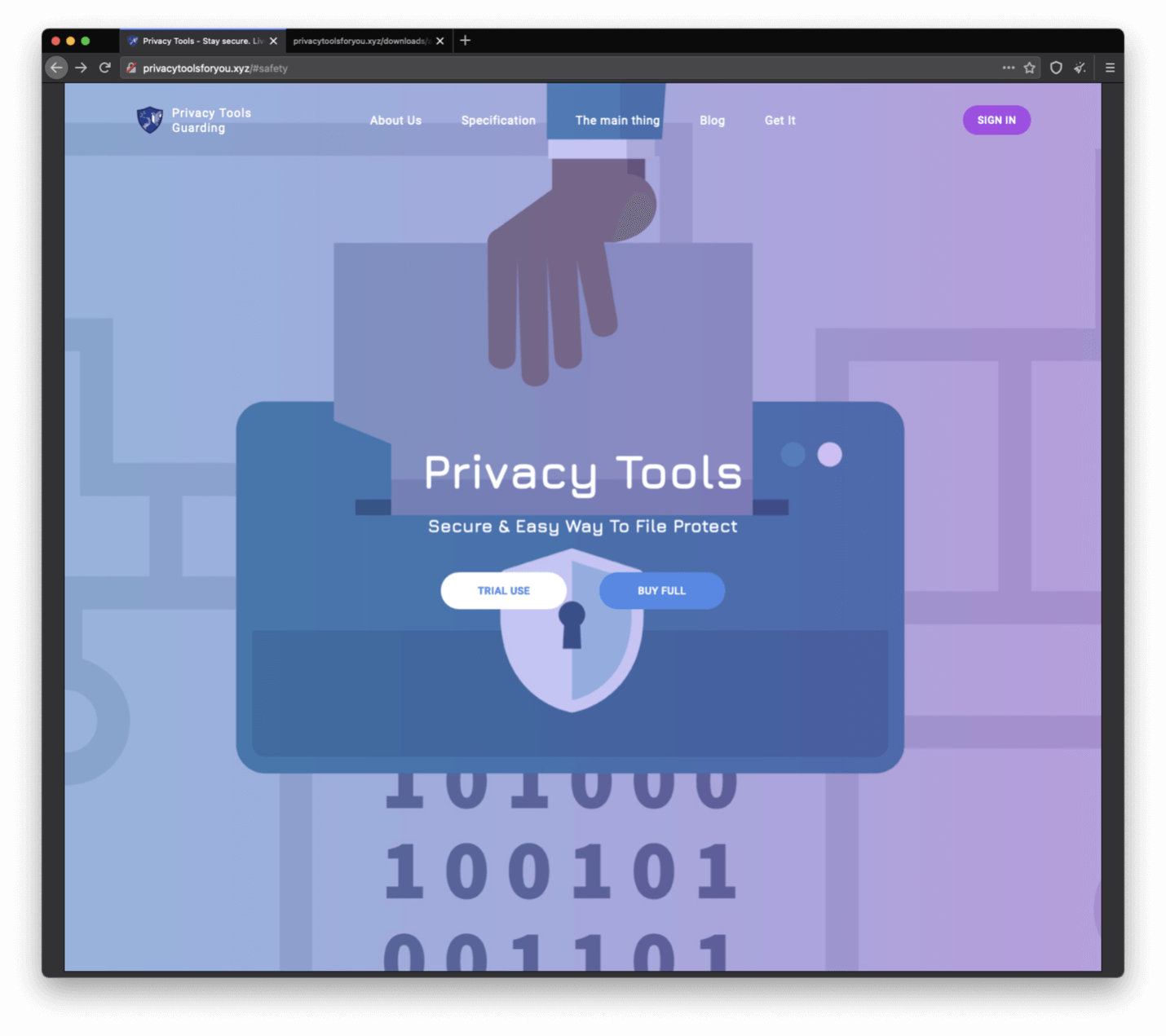
The cybersecurity specialists from Proofpoint have discovered that the threat actors have developed a legitimate-looking website masquerading as a Privacy Tools service claiming to provide utility tools to secure personal and business data.
- This so-called Privacy Tools service is being promoted as a zip-like utility that can encrypt user data ensuring security.
- The website provides detailed information about the alleged services, including step-by-step instructions that guide the users to download and use the privacy tools.
- By following the instructions, the victim eventually ends up installing the Smoke Loader malware, which is a modular downloader with multiple capabilities.
- The Smoke Loader tool further downloads two data-stealing malware, Redline and Raccoon Stealer.
The researchers have identified the initial payload as Smoke Loader. This is a popular downloader available on easily accessible forums for buying and selling malware and used by multiple threat actors.
 Source: Proofpoint
Source: Proofpoint
Smoke Loader installs follow-on data-stealing malware including Raccoon Stealer and RedLine.
Most Recent Infostealer Malware Attacks
Lately, several attackers have been observed spreading infostealer malware by using fake pretenses or other ways to lure their victims.
Some attackers were abusing some Pay-Per-Click (PPC) ads in Google’s search results in order to end up downloading the malicious AnyDesk, Dropbox, and Telegram packages, fake apps that eventually would infect the victims with Redline, Taurus, Tesla, and Amadey infostealer malware.
Also, it’s worth mentioning that some threat actors were found abusing the Microsoft Build (MSBuild) Engine in an attempt to infect their victims with Remcos RAT and Quasar RAT, along with RedLine Stealer.
Takeaways
This campaign had shed some light on the fact that the attackers are increasing the amount of effort are putting into making professional-looking privacy-themed lures that are realistic and effective.
We’re seeing an increase in the infostealers activity that raises concerns about the ever-growing demand for private information in the underground markets.
Users should use reliable anti-malware solutions to stay protected.
When using proper security solutions on your devices you’ll remain safe as Threat Prevention Softwares will stop you in the process of entering the malicious website.
HEIMDAL™ Threat Prevention is the world’s most advanced DNS product, used to identify infected users and processes.

Heimdal® Network DNS Security
- No need to deploy it on your endpoints;
- Protects any entry point into the organization, including BYODs;
- Stops even hidden threats using AI and your network traffic log;
- Complete DNS, HTTP and HTTPs protection, HIPS and HIDS;
Our cutting-edge Network & Endpoint Prevention, Detection, and Response solutions block attacks before they reach your network, servers, or endpoints. Thanks to their unique combination of local and cloud filtering, we guarantee a minimal system footprint.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










