Contents:
A new Emotet campaign started infecting devices all over the world on Tuesday, 7 March 2023. After a three-month break, the botnet sends malicious spam emails again.
Emotet malware reaches targets through emails with malicious attachments. When the user opens the Microsoft Word or Excel document, macros are enabled. This way, Emotet DLL loads into the device’s memory. Then, the malware awaits instructions from the C2 server for further actions.
The New Emotet Campaign
Researchers at Cofense and Cryptolaemus signaled that the Emotet botnet resumed activity.
The first email we saw was around 7 am EST. Volume remains low at this time as they continue to rebuild and gather new credentials to leverage and address books to target.
Cofense, for BleepingComputer
This time, cybercriminals use invoices instead of reply-chain emails like in other spam email campaigns. These emails have an attachment with a ZIP file of 500 MB. The file is an inflated Word document with unused data to make it harder to detect. The text of the email is asking users to enable the document’s content to view it properly.
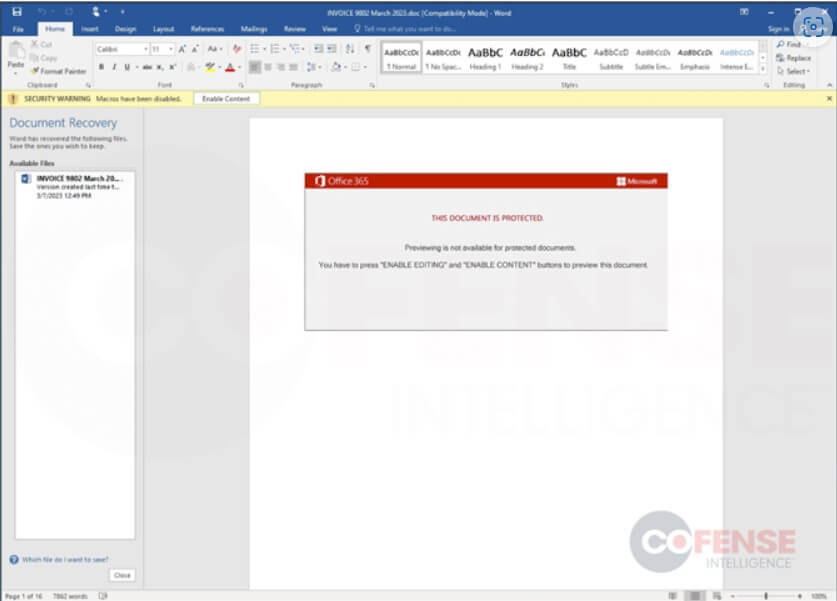
But the document will download the Emotet loader as a DLL from compromised WordPress blogs. The malware will then await commands from the threat actors.
When downloaded, Emotet will be saved to a random-named folder under %LocalAppData% and lauLike the Word document, the Emotet DLL has been also padded to be 526MB to hinder the ability to detect it as malicious by antivirus software.
Once in, hackers can access the device remotely, spread the infection further in the network, steal data, and start a ransomware attack.
Although the evasion technique used in this Emotet campaign is successful, recent changes might be an obstacle. Microsoft disabled macros by default in downloaded Microsoft Office documents in July 2022. In consequence, users that open an Emotet spam email will not enable macros by chance.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and YouTube for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security









