Contents:
Cybersecurity specialists discovered a massive phishing campaign that used Facebook Messenger to trick millions of individuals into entering their login details and watching advertisements on phishing pages.
These stolen accounts were used by the threat actors to deliver more phishing messages to their friends, resulting in impressive earnings from online advertising commissions.
American AI-focused cybersecurity company PIXM said that the operation reached its peak in April-May 2022 but has been functional since at least September 2021.
Because one of the phishing pages that was identified by the security firm contained a link to a traffic monitoring tool (whos.amung.us) that was publicly accessible without authentication, the researchers were able to track down the malicious actors and map the campaign.
More on the Operation
While no one knows how the phishing operation began, PIXM claims that targets were sent to phishing landing pages via a series of Facebook Messenger redirects.
Because more Facebook accounts were hacked, the cybercriminals utilized automated software to send additional phishing links to the affected account’s friends, resulting in a huge increase in the number of stolen accounts.
A user’s account would be compromised and, in a likely automated fashion, the threat actor would log in to that account and send out the link to the user’s friends via Facebook Messenger.
Even if Facebook has security measures in place to prevent the spread of phishing URLs, the attackers used a trick and managed to avoid these protections. Authentic URL generation services like litch.me, famous.co, amaze.co, and funnel-preview.com were used in the phishing campaign, so blocking them wouldn’t be an option since legitimate apps use them.
As per BleepingComputer, after discovering that they could obtain unauthenticated access to the phishing campaign stats pages, the experts noted that 2.7 million people had visited one of the phishing portals in 2021.
The situation changed in 2022, when the number increased to 8.5 million, indicating the operation’s tremendous growth.
A deeper investigation revealed 405 different usernames used as campaign identifiers, each with its own Facebook phishing page. The number of page views on these phishing pages ranged from 4,000 to millions, with one reaching 6 million.
After the user enters their login details on the phishing webpage, they are redirected to advertising pages, survey forms, and other sites.
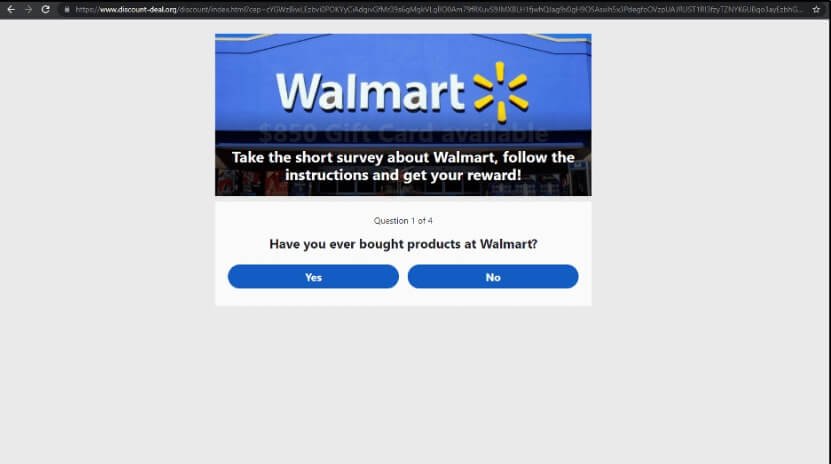
These redirects generate referral revenue for the cybercriminals, which is estimated to be millions of dollars at this scale.
Who’s Behind the Phishing Campaign?
The AI-focused cybersecurity firm discovered a common code snippet on all landing pages that included a mention of a website that has been taken down and is part of an investigation against a Colombian individual named Rafael Dorado.
It is unknown who seized the domain and posted the message below on the site.
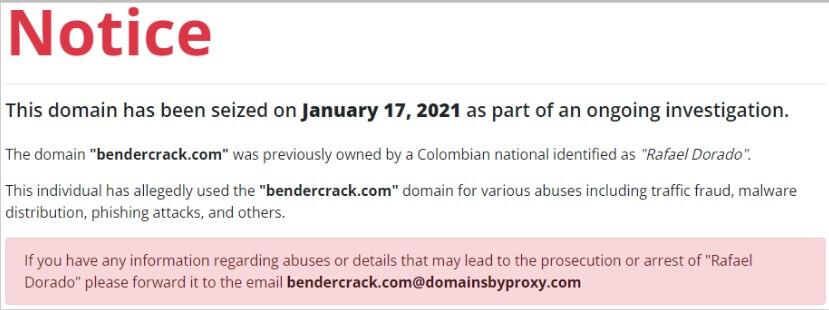
The results of PIXM’s investigation were communicated with the Colombian Police and Interpol, but the operation is currently underway, despite the fact that most of the identified URLs have gone offline.
According to BleepingComputer, a reverse whois search revealed links to a genuine Colombian web development organization and old websites providing Facebook “like bots” and hacking solutions.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










