Contents:
Github, the well-known code hosting platform, has recently released new analysis features that have the role to automate the identification of new security flaws before they reach production. These features are designed on machine learning-based code scanning.
New Scanning Analysis Features Implemented by GitHub: More Details
The new features implemented by GitHub are currently accessible for JavaScript and TypeScript GitHub repositories.
Tiferet Gazit together with Alona Hlobina from Github said in a blog post that
With the new analysis capabilities, code scanning can surface even more alerts for four common vulnerability patterns: cross-site scripting (XSS), path injection, NoSQL injection, and SQL injection. (…) Together, these four vulnerability types account for many of the recent vulnerabilities (CVEs) in the JavaScript/TypeScript ecosystem, and improving code scanning’s ability to detect such vulnerabilities early in the development process is key in helping developers write more secure code.
The security flaws that this new experimental code analysis will identify will appear as alerts in the tab called ‘Security’ in the enrolled repositories section, alerts that will be labeled as “Experimental”. You can see a display of this below:
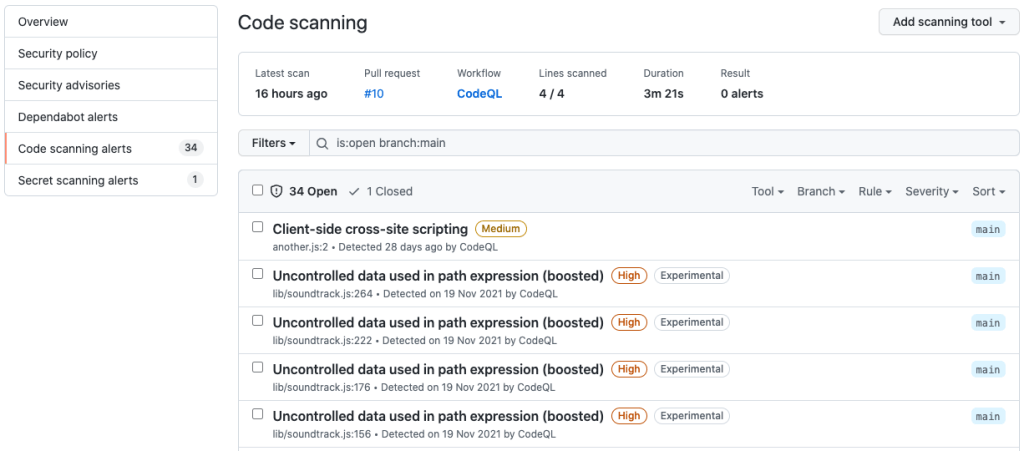
After GitHub bought code-analysis platform Semmle in September 2019, the CodeQL code analysis engine, which drives GitHub’s code scanning, was added to the platform’s capabilities.
In May 2020, GitHub launched the first code scanning beta at GitHub Satellite, and four months later, in September 2020, it became generally available.
During the beta testing phase, the code scanning function scanned over 12,000 repositories 1.4 million times and discovered over 20,000 security weaknesses, including RCE, SQL injection, and cross-site scripting (XSS) flaws.
For public repositories, GitHub Code scanning is free of charge, and for GitHub Enterprise private repositories, it comes in the form of a GitHub Advanced Security feature.
GitHub code scanning is powered by the CodeQL analysis engine. To identify potential security vulnerabilities, you can enable CodeQL to run queries against your codebase. These open source queries are written by members of the community and GitHub security experts, and each query is carefully crafted to recognize as many variants of a particular vulnerability type as possible and provide broad Common Weakness Enumeration (CWE) coverage.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










