Contents:
A yesterday Microsoft’s advisory has been brought to the public’s attention: a new Print Spooler zero-day vulnerability was discovered that is dubbed CVE-2021-36958. The consequences might be that local threat actors could achieve system privileges. This flaw is part of the well-known PrintNightmare bugs class we have written a lot about.
How Does the New Print Spooler Zero-Day Work?
Benjamin Delpy, the creator of Mimikatz and the one who has investigated PrintNightmare in the course of time shared a POC (Proof of Concept) on Twitter on this new Print Spooler zero-day.
It works like this:
- If hackers connect to a remote print server, they can achieve system privileges.
- The CopyFile registry directive is used with the goal to copy a DLL file.
- The latter will open a command prompt and also a print driver.
- These happen when connecting to a printer.
- The difference here is that if the driver is already installed, admin rights are not required to get access to the printer, as one should do when installing a driver as per Microsoft security update KB5005652— that made changes to printer driver installation procedure in order to ask for administrator privileges.
- Besides, the driver might already exist on a client, therefore there will be no need for an installation, if this is the case, the Copy File registry can still be executed for users that do not have admin rights when they connect to a remote printer.
- This way the researcher showed how his DLL can be copied to the client and then it leads to system-level command prompt opening by being executed.
The video below shows Benjamin Delpy’s POC:
Will Dormann, a CERT/CC analyst, shared with BleepingComputer publication his opinion on the matter. He declared that Microsoft confirmed that the security advisory they released for the new bug talks about the same vulnerability Benjamin Delpy describes through his POC. Dormann also added since the vulnerability has CVSS:3.0 7.3 / 6.8 score, it obviously indicates that this is local abuse of privileges, though Microsoft described it as a remote code execution bug.
The new Print Spooler zero-day was firstly discovered by FusionX analyst Victor Mata in December 2020. He says in a Twitter Post that he reported the issue back then, but has not shared further details as per MSRC’S request.
Mitigation Measures for New Print Spooler Zero-Day
There are no security updates released by Microsoft at the moment for this recent bug, however, the software company provided some general mitigation measures in their security advisory:
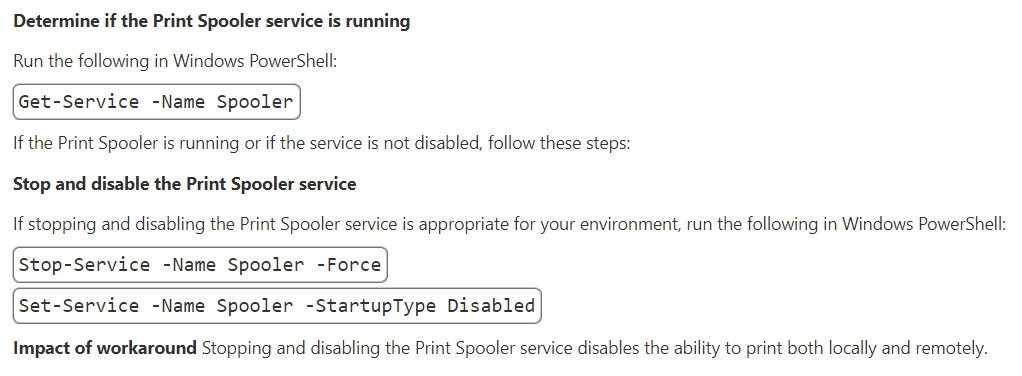
But if users disable the Print Spooler, this means that printing is not possible anymore. BleepingComputer comes with another method. They say that the installation of printers should be done only from authorized servers. How can one do this? Go to ‘Package Point and print – Approved servers’ group policy. The policy can be enabled by launching the Group Policy Editor (gpedit.msc). Then use User Configuration > Administrative Templates > Control Panel > Printers > Package Point and Print – Approved Servers. At this point, you should provide the list of authorized servers that will permit print server usage as per your wish and then click on “OK”.
What Is PrintNightmare?
PrintNightmare was classified as a zero-day bug, leaked online by mistake. It takes advantage of Windows Point and Print capability and print drivers. It is also known as a vulnerability in Windows Print Spooler that allows both remote code execution and abusing of the local privilege escalation feature. PrintNightmare bugs were addressed by Microsoft in July and August with security updates, but it seems that a new Print Spooler zero-day has emerged.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










