Contents:
Security firm FireEye recently revealed that alleged Chinese spies posed as Iranian hackers in a two-year campaign to break into the Israeli government and telecommunication networks.
The imposters used a hacking tool that was formerly associated with Iranian agents and embedded their malicious code with Farsi, Iran’s predominant language. According to FireEye researchers, the operation was part of a broader campaign to gather intelligence at organizations in other Middle East and Central Asian countries.
The discovery shows how the spies planted digital evidence in an effort to throw off investigators in the high-stakes world of espionage. These findings come in the context of the July 19, 2021, announcements by governments in North America, Europe, and Asia and intragovernmental organizations, such as the North Atlantic Treaty Organization (NATO), and the European Union, condemning widespread cyber-espionage conducted on behalf of the Chinese Government.
After gaining initial access, the operators conduct credential harvesting and extensive internal network reconnaissance. This includes running native Windows commands on compromised servers, executing ADFind on the Active Directory, and scanning the internal network with numerous publicly available tools and a non-public scanner we named WHEATSCAN. The operators made a consistent effort to delete these tools and remove any residual forensic artifacts from compromised systems.
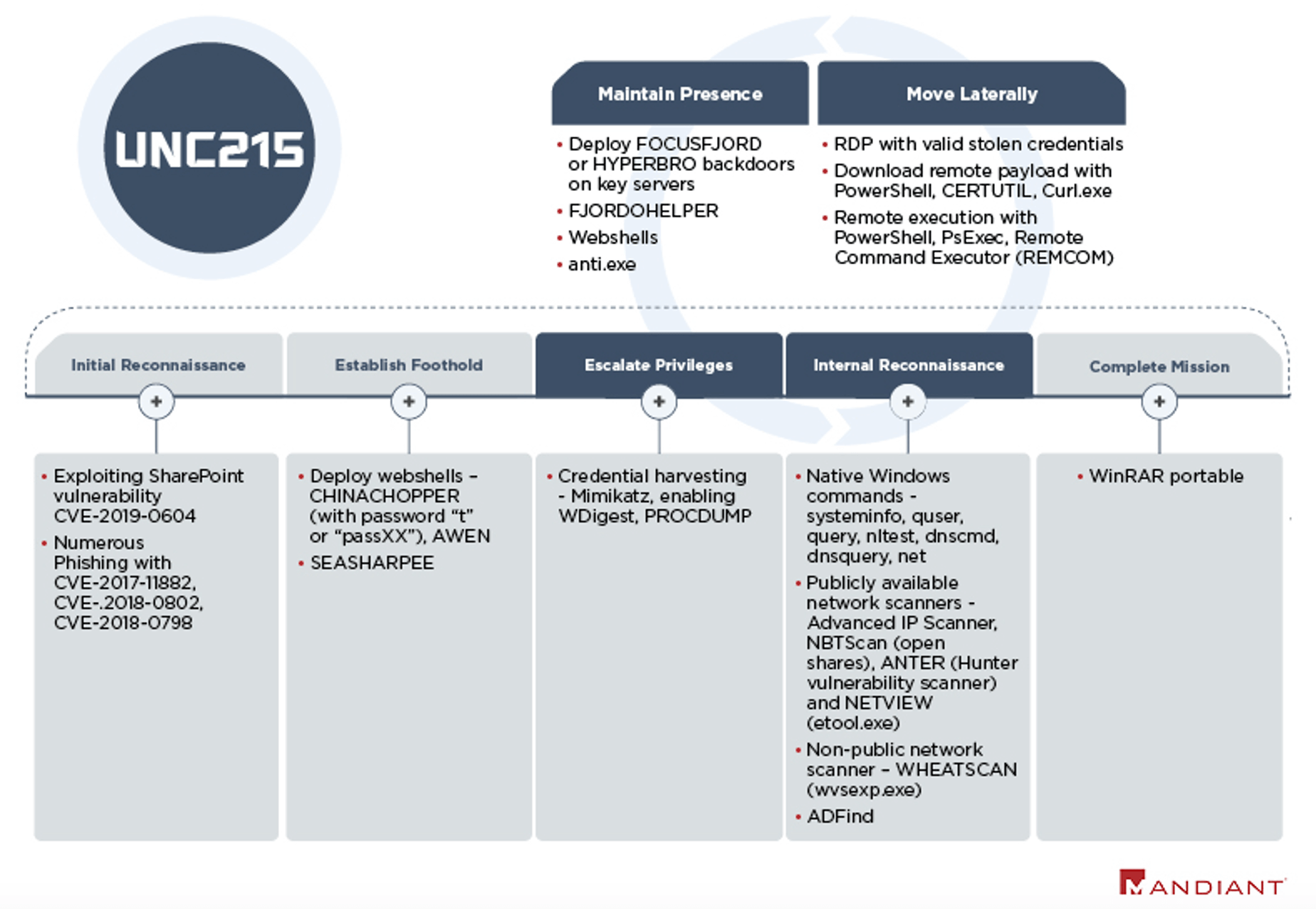
VP of threat intelligence at Mandiant FireEye, John Hultquist, declared for Cyberscoop that the targeting at Israeli organizations and elsewhere has been “consistent with previous Chinese government activity.” The security firm has not revealed which Chinese government entity may have sponsored the espionage and didn’t identify the victims of the attack, only adding that there were “multiple, concurrent operations against Israeli government institutions, IT providers and telecommunications entities beginning in January 2019.”
During the 2018 Olympics in South Korea, Russia’s GRU military intelligence agency masqueraded as North Korean hackers to play havoc with some IT services. Similar to this situation, the suspected Chinese threat actors managed to frame a likely suspect for their activity. As previously stated, Israel and Iran have constantly blamed each other for critical infrastructure cyberattacks.
The use of Farsi strings, filepaths containing /Iran/, and web shells publicly associated with Iranian APT groups may have been intended to mislead analysts and suggest an attribution to Iran. Notably, in 2019 the government of Iran accused APT27 of attacking its government networks and released a detection and removal tool for HYPERBRO malware.
FireEye researchers collaborated with Israeli defense agencies to review data from additional compromises of Israeli entities.
In the meantime, Chinese Embassy spokesperson Liu Pengyu said China “firmly opposes and cracks down on all forms of cyberattacks,” describing FireEye’s allegations as “irresponsible and ill-intentioned.”


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










