Contents:
A bug bounty reward worth $2 Million went to researcher Gerhard Wagner based on his discovery of a critical flaw located in Polygon’s Plasma Bridge. If successfully exploited, this Polygon vulnerability would have let a hacker perform repetitive withdrawal transactions by means of various exit IDs. The number of submissions could have raised to 224.
The Polygon Vulnerability: How Could It Have Been Abused
As SecurityWeek explains, the Polygon Plasma Bridge could be used for the deposit of a certain amount of money, then the whole sum can be withdrawn. The same transaction could have been performed not less than 223 times additionally, every withdrawal transaction bringing with it the full amount of money. More specifically, what that means is that a threat actor could have deposited $1 million and through this method ending having $224 million by exploiting the Polygon vulnerability.
The real threat could have been the fact that a cybercriminal could have emptied the Plasma Bridge’s Deposit Manager where approx. $850 million can be found.
Where The Issue Lied
Gerhard Wagner published a report on this topic where he detailed the issue with the Polygon vulnerability. It seemed that the problem was related to Polygon’s WithdrawManager, as the way this makes inclusion checks and the burn transactions’ uniqueness did not work properly. More exactly, there is a function that handles the check on the branchMask of Merkle proof for the burn transaction receipt and there was the place where the flaw was discovered.
The Polygon vulnerability was possible because while the decoding operation happened, certain values and differences were disregarded. The decoding differences made the same proof replaying possible.
Then the attack is launched, and 223 alternative exit payloads are generated with the technique described above, and exits are initiated for each one of them. All exits get a unique id and are added to the exit queue. Their age is already older than the challenge period since the burn transaction has been aggregated into a Plasma block, so the funds can be released on L1. After all exits have been started and processed, the malicious user gains 223 times the amount on top of the initial deposit or tokens valued at 44.6 million USD. A malicious user can increase the reward by either increasing the deposit amount or depositing and exiting funds multiple times.
The Polygon vulnerability was reported on the 5th of October, as it was registered in Polygon’s bug bounty program. Since the report met the necessary criteria for receiving the award, the researcher who found the flaw received no less than $2 million.
A Little Bit Insight Into the Polygon Plasma Bridge
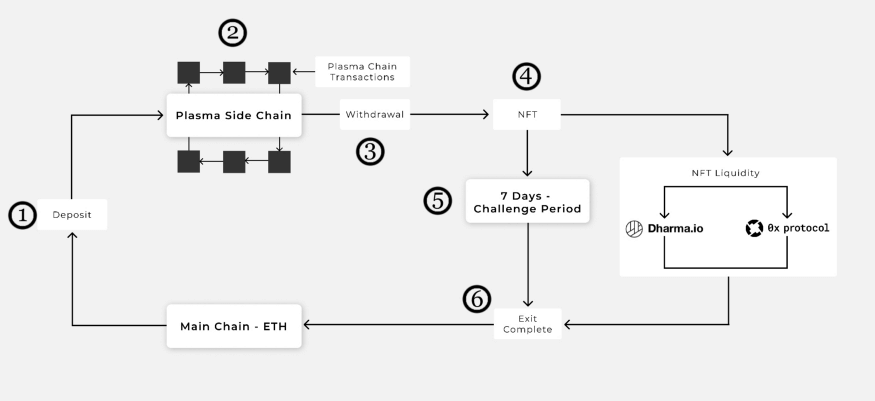
Plasma Bridge is basically a solution from Polygon and it’s characterized by the blockchain bridge it supports. This blockchain bridge is slightly a way through which two different blockchains are connected. This facilitates the creation of transaction channels that work in two ways. Simply put, users can transfer assets from the root chain to the child chain (e.g. from Ethereum to Polygon).
The withdrawal transaction will be initiated on the network, then a set of checks follows, the transaction is approved, and then there is a waiting time of 7 days before funds can be withdrawn to Etherum’s accounts.
And the last steps of the process are these:
- Tokens are burned on the child chain when the withdrawal is initiated;
- Then there’s the burn confirmation;
- What happens next is a 30 minutes checkpoint running;
- The Polygon Plasma withdraw function receives the exit payload.
There are 2 conditions under which the withdrawal transaction can be finalized: the success and validity of the burn transaction and the root chain has to include the proof.
Here is a diagram of how Polygon Plasma Bridge works:
If you enjoyed this article, you’ll surely enjoy other pieces of content too. To make sure you do not miss a thing follow us on LinkedIn, Twitter, YouTube, Facebook, and Instagram to keep up to date with everything we post!


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










