Contents:
On Sunday, a cryptocurrency flash loan attack on the lending platform Euler Finance resulted in the theft of $197 million in various digital assets by threat actors. The theft involved multiple tokens including $135.8 million in stETH, $33.85 million in USDC, $18.5 million in WBTC, and $8.75 million in DAI.
The ETH wallet used to store the stolen cryptocurrency is being tracked, making it difficult for the threat actor to move the funds around and convert them into a usable form.
Euler Finance Addresses the Attack
The start-up behind Euler Finance shared a brief statement via Twitter to explain the situation, saying that they have informed and are working with law enforcement agencies and security professionals. According to reports from Elliptic, the threat actors have already begun to launder the stolen cryptocurrency through the decentralized cryptocurrency mixer Tornado Crash.
We are aware and our team is currently working with security professionals and law enforcement. We will release further information as soon as we have it. https://t.co/bjm6xyYcxf
— Euler Labs (@eulerfinance) March 13, 2023
As a result of the attack, the value of the Euler (EUL) toked already dropped by 48.9%, going from being worth $6.56 to $3.07 at the moment of writing.
Flash Loan Attacks Explained
Flash loan attacks take advantage of a flaw in a lending protocol to take out a sizable loan without having to pay it back to the service. In order to make a significant profit when the deal is finished, the attackers employ an exploit that enables them to control the price of a token or asset on the platform during the brief seconds that they retain the lent amount.
As reported by BleepingComputer, the hack of Euler was made possible due to a flawed logic in its donation and liquidation system. The liquidation system incorrectly verified the conversion rate from the loaned to the collateral asset, and the function “donateToReserves” failed to check that the attacker was donating an amount that was excessively collateralized.
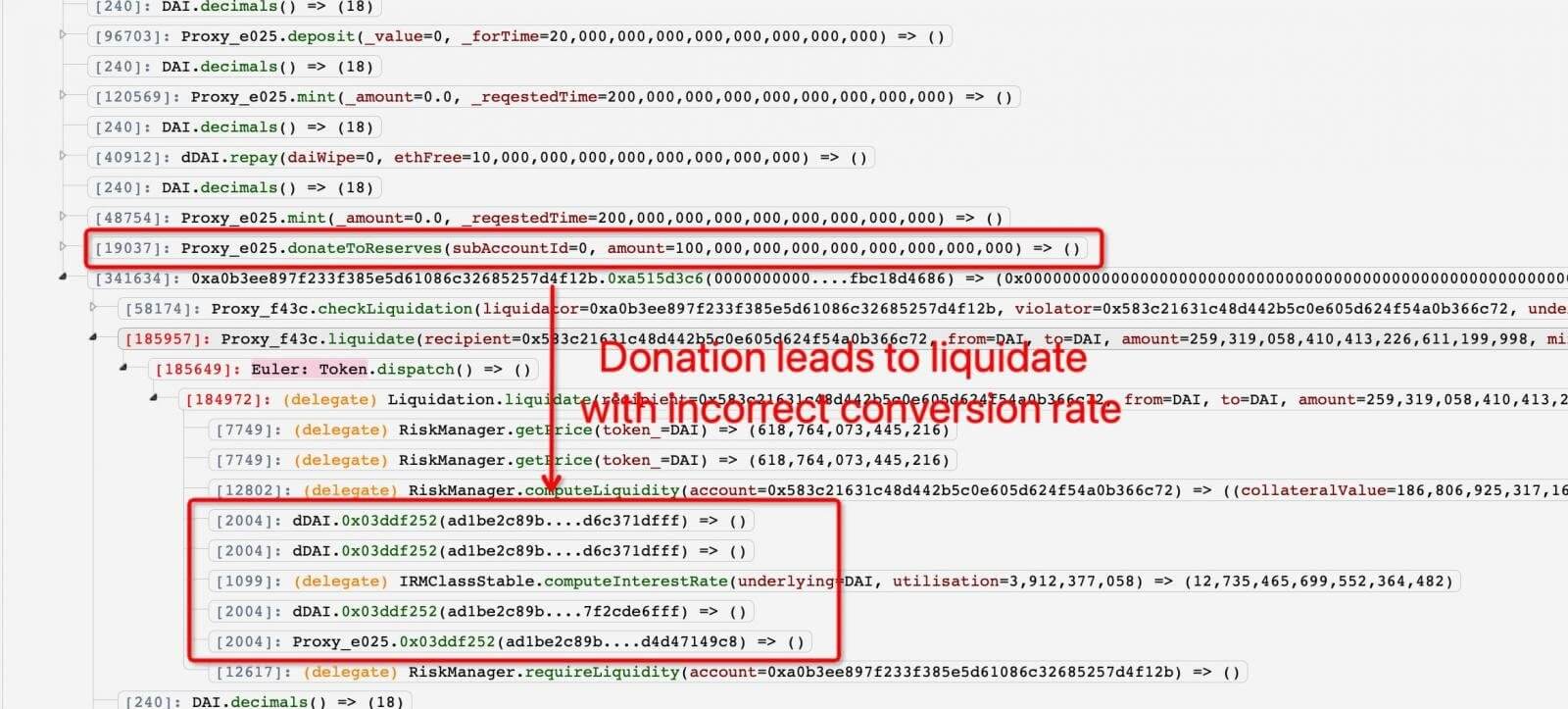
Euler Finance Flaw (Source: PeckShield)
The flaws allowed the attackers to manipulate the conversion rate and thus, profit from the liquidation process. According to PeckShield, the attack involved two threat actors, a borrower and a liquidator.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and Youtube, for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








