Contents:
Large-scale attacks on WordPress websites are being carried out by hackers to insert scripts that compel users’ browsers to try different websites’ passwords repeatedly.
Cybersecurity researchers have been tracking a threat actor known for breaching sites to inject crypto wallet drainer scripts which steal all cryptocurrency and assets of victims when they connect to their wallet.
The scripts on these hijacked websites present false information to users in an attempt to persuade them to link their wallets to the website. The scripts then take all of the contained assets, but, after they have done so.
Reportedly, the threat actors were breaching compromised WordPress sites to inject the AngelDrainer wallet drainer in multiple waves from multiple URLs.
Brute-Force Attacks: A Look at the Threat Actor’s Execution
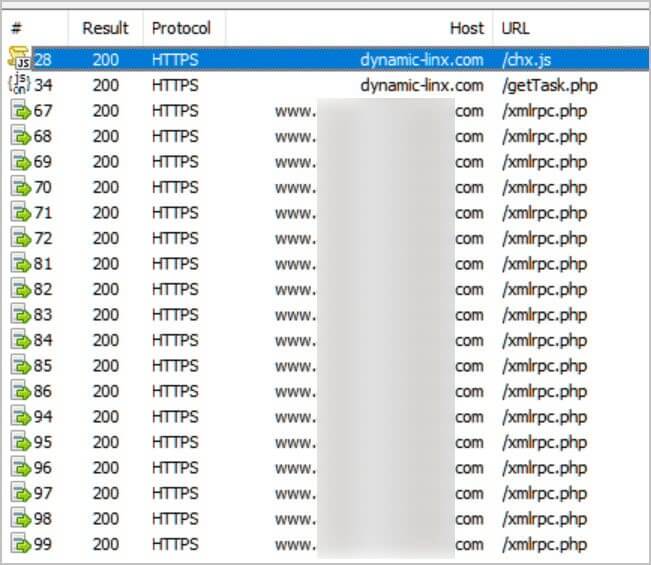
The threat actor moved from draining victims’ wallets to using their browser hijacks to brute-force other WordPress websites in late February, employing a malicious script that was obtained from the recently registered website “dynamic-linx[.]com/chx.js.”
Now, it’s using compromised WordPress sites to load scripts that force the visitors’ browsers to conduct brute-force attacks for account credentials on other websites. Using the credentials, the threat actor is aiming at stealing data, injecting malicious scripts, or encrypting files on the breached site.
Threat actors breach a WordPress website as part of this hacking campaign to insert harmful code into the HTML templates, which are then loaded in browsers from https://dynamic-linx[.]com/chx.js when users visit the website.
By using these scripts, the browser will silently make contact with the threat actors’ server at ‘https://dynamic-linx[.]com/getTask.php’ to obtain a task that involves brute-forcing passwords.
This task is a JSON file with one hundred passwords to try, an ID, the website URL, the account name, a number indicating the current batch of passwords to go through, and other parameters for the brute-force attack.
The script will alert the threat actor’s server that a password has been discovered for the website if the password is correct. After that, the hacker can access the uploaded file that contains the base64-encoded username and password combination by connecting to the website.
Script Used to Brute-Force’s Website Credentials (Source)
The malicious script will force the web browser to continually reconnect to the attacker’s server and download a fresh task to complete as long as the page is open.
As per the HTML source code engine PublicHTML, there are over 1,700 WordPress sites hacked with these scripts or their loaders, making up a massive pool of users who unwillingly will conscript into the attack.
It is yet unclear why the threat actors switched to brute-force attacks, but researchers believe that they might have realized that at their scale of infection of around 1,000 websites, the drainers were not yet profitable. They might also have done it to build a more extensive portfolio of sites from which to launch attacks at a larger scale.
If you liked this piece, follow us on LinkedIn, Twitter, Facebook, and YouTube for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








