Contents:
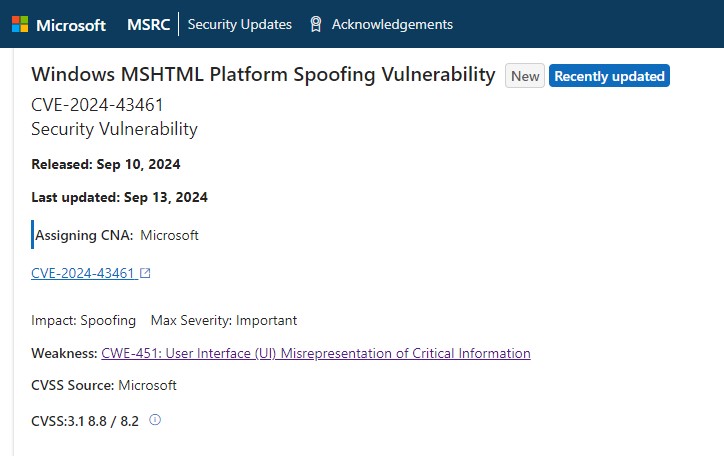
Microsoft revealed that hackers have exploited as zero-day a Windows MSHTML platform spoofing vulnerability for more than two months.
The company released a patch for CVE-2024-43461, during the September Patch Tuesday. They didn’t know that hackers were exploiting this flaw at that time. The vulnerability lets unauthorized attackers execute code remotely. Hackers used it as a zero-day to spread info-stealing malware.
CISA included this Microsoft flaw in its Known Exploited Vulnerabilities Catalog and urged all US federal agencies to apply patches.
How did hackers exploit the Windows MSHTML platform spoofing vulnerability
Researchers say that before July 2024, CVE-2024-43461 was part of an exploit chain, along with another MSHTML spoofing flaw, CVE-2024-38112. Microsoft released a patch for CVE-2024-38112 at that moment and broke the attack chain.
In addition, security specialists have observed the Void Banshee threat group using CVE-2024-43461 to install infostealers.
the threat actor lured victims using malicious files spoofed as book PDFs that they distributed via Discord servers, file-sharing websites, and other vectors. Void Banshee is a financially motivated threat actor that researchers have observed targeting organizations in North America, Southeast Asia, and Europe.
Source – DarkReading.com
How to patch Microsoft vulnerabilities effectively
To keep safe from attacks like those conducted by Void Banshee, Microsoft advised System Administrators to apply patches from both July and September.
Patch Tuesday for September alone brought 79 flaws to patch, out of which 5 turned out to be zero-days.
Keeping software up to date is one of the most time-consuming task of a sysadmin. The need to test every patch before deployment adds up to an already challenging job.
Due to the constantly increasing number of disclosed and/ or exploited vulnerabilities, applying patches timely almost become mission impossible.
However, there is a way out. Automated patch management software helps IT teams solve patching issues with only a few clicks.
Book a demo to see how using Heimdal’s Patch and Asset Management solution would support your team through the whole patch management process.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and Youtube, for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security