Contents:
To obtain Microsoft Office 365 and Outlook credentials, a new phishing operation has been targeting U.S. firms in the military, security software, manufacturing supply chain, healthcare, and pharmaceutical sectors. The operation is still active, and the attacker responsible is luring victims into opening a malicious HTML file with fake voicemail notifications.
The newly-uncovered operation, according to experts at cloud security firm ZScaler, shares Tactics, Techniques, and Procedures (TTPs) with yet another campaign evaluated back in 2020.
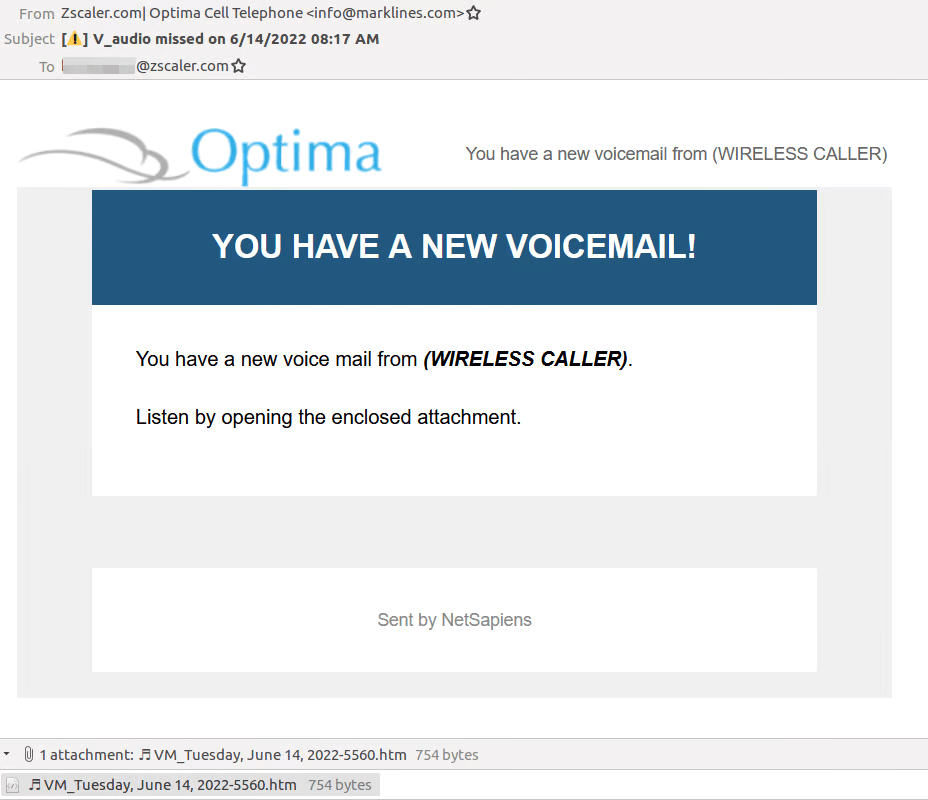
Voicemail-themed email sent to a user at Zscaler
Threat actors employ email services in Japan to route their communications and spoof the sender’s address, trying to make the emails appear to come from an address associated with the targeted company.
The email contains an HTML file with a music note character to create the impression that the file is an audio clip. The file, in fact, includes obfuscated JavaScript code that redirects the user to a phishing website.
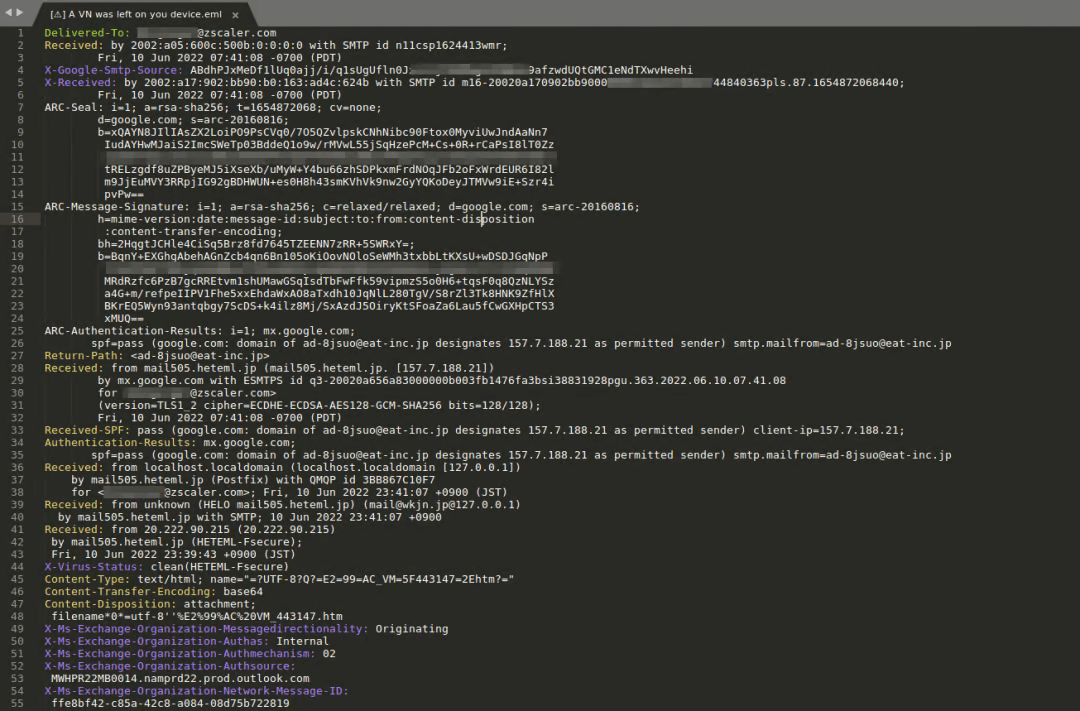
Email header
The URL format is based on an assembly mechanism that takes into account the domain of the targeted organization to make the site appear to be a valid subdomain. The victim is first redirected to a CAPTCHA check, which is meant to bypass anti-phishing software and give the victims the appearance of validity.
As mentioned by BleepingComputer, the check was also employed in a 2020 campaign that ZScaler’s ThreatLabZ experts investigated, and it remains a successful intermediary stage in phishing success rates.
Users are routed to a genuine-looking phishing page that steals Microsoft Office 365 accounts once they pass this phase.
Indicators of compromise (IOCs)
Normally, users are signed into their accounts, so a request to check in again to listen to voicemail should be suspect. Although voicemail-themed phishing with HTML files has been around since at least 2019, it remains effective, particularly with irresponsible employees.
Users paying close attention will note that the login page’s domain isn’t owned by Microsoft or their business. That’s why you should always double-check that you are on a legitimate login portal:
- briccorp[.]com
- bajafulfillrnent[.]com
- bpirninerals[.]com
- lovitafood-tw[.]com
- dorrngroup[.]com
- lacotechs[.]com
- brenthavenhg[.]com
- spasfetech[.]com
- mordematx[.]com
- antarnex[.]com










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








