Contents:
Cybersecurity firm Sophos recently released a report saying that one malware strain borrowed name recognition from The Pirate Bay, a well-known digital content portal of entertainment media and software that allows visitors to search, download, and contribute magnet links and torrent files, which facilitate peer-to-peer file sharing among users of the BitTorrent protocol. Unfortunately, the portal also serves up malicious software and corrupt ads.
Dubbed “Vigilante”, the malware is hidden in pirated copies of various software, including security products, and distributed on game chat service Discord and through BitTorrent. Once accessed, Vigilante works by flashing up a fake error message on the victim’s screen while executing the infection.
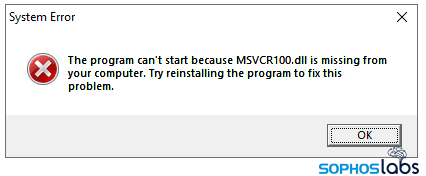
At first glance, Vigilante apparently blocks infected users from accessing a large number of piracy sites by interfering with the HOSTS file on their systems.
According to security researcher Andrew Brandt,
Modifying the HOSTS file is a crude but effective method to prevent a computer from being able to reach a web address. It’s crude because, while it works, the malware has no persistence mechanism. Anyone can remove the entries after they’ve been added to the HOSTS file, and they stay removed (unless you run the program a second time).
Vigilante tries to change the victims’ computer systems to allow them to not entry thepiratebay.com, as well as other 1,000 different pirate websites. The malware also downloads and executes a second payload, an executable named “ProcessHacker.jpg.”
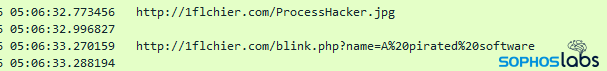
The real purpose of the malware developer is still unknown, says Brandt.
Piracy has been around before the World Wide Web was a thing. Defined as the illegal copying of copyrighted materials, people have been doing this for almost as long as audiovisual media was invested. But while back in the day it consisted of bootleg cassette tapes, VHS tapes, or CDs, nowadays the Internet has helped it spread like wildfire.
Since Vigilante doesn’t have a persistence technique, it means it has no solution to stay put in. Users who have been infected only want to edit their Hosts file to be disinfected. You can check the indicators of compromise here.
Users are urged to install a strong security solution to detect such threats and avoid downloading pirated or “too good to be true” software. Having the appropriate cybersecurity tools under your belt should always be your number one priority. Heimdal™ Security can help you in this regard, so don’t hesitate to reach out at sales.inquiries@heimdalsecurity.com for more info.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








