Contents:
Verizon published Tuesday, June 6th, the 2023 Data Breach Investigations Report (DBIR), one of the most highly regarded reports in cybersecurity. The report reveals details about the actors, actions, and patterns and is an important starting point for any organization`s cybersecurity defense and education strategy.
DBIR 2023 displays conclusions that Verizon’s security team drew after analyzing 16,312 incidents and 5,199 confirmed data breaches.
The top five most targeted sectors revealed Public Administration was in the first place, with 3,270 incidents, followed by Information, with 2,105 incidents, Finance (1,829), Manufacturing (1,814), and Professional, Scientific and Technical Services (1,398).
The analysis was carried out between November 1st, 2021, and October 31st, 2022. Incidents that took place in the Asia-Pacific regions, EMEA, North America, and Latin America were all included in the global study.
Verizon 2023 DBIR in numbers
24% of all breaches involved ransomware.
Ransomware is still a major threat, regardless of the industry or company size. It is present in 24% of the analyzed incidents. According to the Verizon 2023 DBIR, the top vectors for ransomware deployment are email, desktop-sharing software, and web applications.
Additionally, the data provided by the FBI Internet Crime Complaint Center (IC3) about breaches` impact showed the median amount lost due to such an incident grew from $11,500 to $26,000, in the past two years.
83% of breaches involved external actors.
Obviously enough, external threats come from outside the company and its partners. Threat groups, independent hackers, government entities, and disgruntled former employees are the four main categories of external actors.
74% of all breaches include a human element.
According to the report, 74% of the breaches were a result of social engineering, stolen credentials, and human error. Privilege misuse is also on the list and is strongly related to the 19% of incidents caused by internal actors. However, the percentage trended down from 82% in 2021. As it seems, poor password management continues to be a leading cause of data breaches.
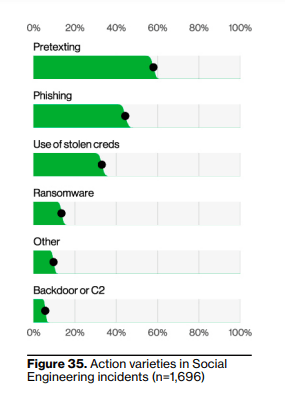
BEC attacks have risen to 50% of social engineering incidents.
Although phishing remains a common social engineering tool for data breaching, pretexting incidents were on an upward trend last year. Usually, this kind of attack involves impersonation and business email compromise. BEC attacks have reportedly doubled during the past year and they now account for over 50% of social engineering incidents.
Source: Verizon 2023 Data Breach Investigations Report
95% of breaches are financially driven.
The war in Ukraine also happens at a cybersecurity level. In the past two years we`ve witnessed a surge in government-paid attacks on public institutions. Although cyberespionage and state-funded attacks are widely reported, the DBIR 2023 revealed that a huge majority of 95% of data breaches were still financially driven.
Read the full report here, to find out more data and insights about the cyberattack landscape.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and Youtube for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security