Contents:
As Elon Musk took charge of Twitter`s management, there have been some controversial changes implemented, one of them being the $8 a month fee for Twitter Blue and account verification. Other than receiving the famous blue tick, paid users will get priority in replies, mentions & search, fewer ads, and the ability to post longer content. However, it wasn`t long before phishing emails targeting verified users began surfacing, which means threat actors are just as active as always.
Jumping on the Opportunity
Twitter verified accounts have been targeted by phishing campaigns before, back in 2021, while this year the British Army’s Twitter account was breached and used to promote cryptocurrency scams.
This time around, not long after Musk’s tweets, BleepingComputer observed a surge in phishing campaigns insisting that users sign-in to their Twitter account or risk suspension. Upon a closer inspection, it was revealed that these emails were originating from servers of hacked websites and blogs running unpatched, vulnerable plugins.
Once the user clicks the link, they are taken to the phishing webpage where threat actors actively exploit the $8 monthly fee announcement. The user’s Twitter username and password are collected first, then a two-factor authentication code is sent via SMS.
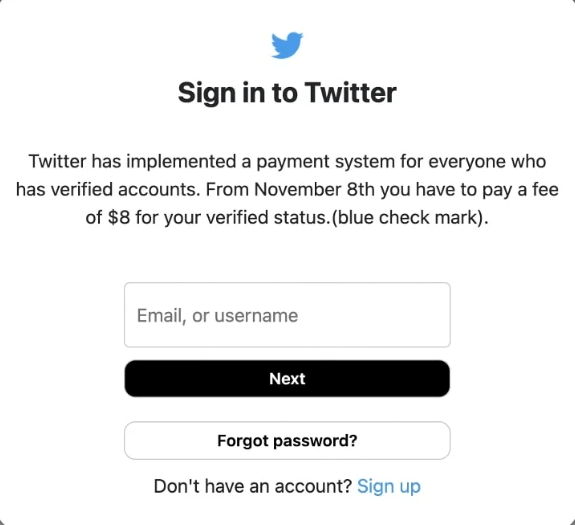
The Blue Badge of Twitter
The blue badge had the initial purpose of separating real, authentic accounts of publicly known people from copycat and parody accounts. Seeing the verification mark thus guaranteed users they were reading the information directly from the source, be it political figures, celebrities or institutions.
However, if the blue badge becomes available to just about anyone willing to pay $8 a month, the authenticity of the information flow on Twitter will become questionable to say the least, while the blue badge becomes a simply aesthetic feature.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security







