Contents:
The Tor Project released the Tor Browser 10.0.18 in an attempt to fix multiple bugs. In this update, they are fixing a Tor Browser vulnerability that allows sites to track users by fingerprinting the applications installed on their devices.
Tor is a free and open-source software meant to enable anonymous communication. It works by directing the internet traffic through a free, worldwide, volunteer overlay network, consisting of more than seven thousand relays, and therefore manages to conceal a user’s location and usage from anyone conducting network surveillance or traffic analysis.
The Tracking Flaw Able to Avoid Privacy Tools
In May, the company FingerprintJS disclosed a ‘scheme flooding’ vulnerability allowing for the users to be tracked across different browsers based on using the applications that were installed on their devices.
Cross-browser anonymity is something that even a privacy conscious internet user may take for granted. Tor Browser is known to offer the ultimate in privacy protection, though due to its slow connection speed and performance issues on some websites, users may rely on less anonymous browsers for their everyday surfing.
They may use Safari, Firefox or Chrome for some sites, and Tor for sites where they want to stay anonymous. A website exploiting the scheme flooding vulnerability could create a stable and unique identifier that can link those browsing identities together.
To perform the cross-browser tracking using scheme flooding, a website builds a profile of applications installed on a device by attempting to open their known URL handlers and checking if the browser launches a prompt.
In order to track users, a profile is created by attempting to open various application URL handlers, such as zoommtg://, and checking if the browser launches the requested prompt.
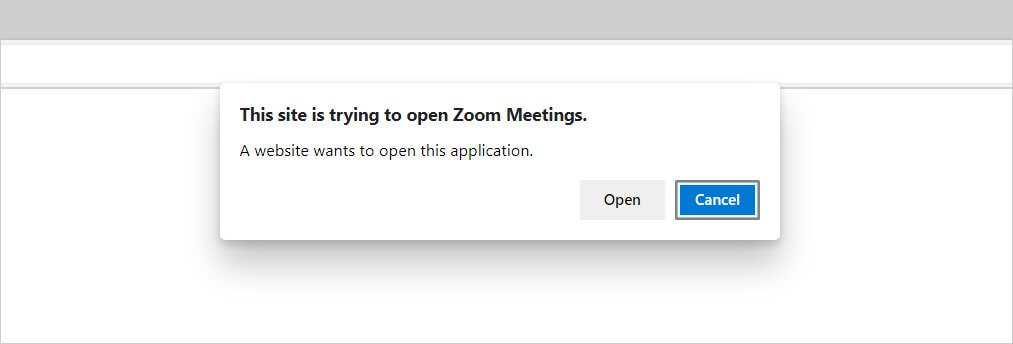
If the application’s prompt is displayed, it is safe to assume that the application is installed on the device, and by checking for numerous URL handlers, this specific vulnerability can create an ID based on the unique configuration of the apps that are installed on the user’s device.
This ID can afterward be tracked across different browsers, like Google Chrome, Edge, Tor Browser, Firefox, and Safari, but the vulnerability is especially concerning for Tor users who are using the browser to protect their identity and IP address from being logged with the sites they are accessing.
As this specific vulnerability is managing to track the users across browsers, it can allow websites, and even law enforcement, to track a user’s real IP address when they switch to a non-anonymizing browser, such as Google Chrome.
Tor Released a Fix for This Vulnerability
By releasing the Tor Browser 10.0.18 update, the Tor Project is introducing a fix for this vulnerability by setting the ‘network.protocol-handler.external’ setting to false, as this default setting is able to prevent the browser from passing the handling of a particular URL to an external application and in this way no longer trigger the application prompts.
It’s quite easy to upgrade your Tor Browser to the 10.0.18 version as you just need to open the menu, go to Help, and select About Tor Browser, which will automatically check for and install any new updates.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










