Contents:
Researchers observed a rise in daily infection attempts leveraging old TP-Link Archer Command Injection Vulnerability.
Since March 2024, six botnet malware operations showed interest in scanning TP-Link Archer AX21 (AX1800) routers for CVE-2023-1389. The daily number of attempts ranged between 40,000 – 50,000 during the month.
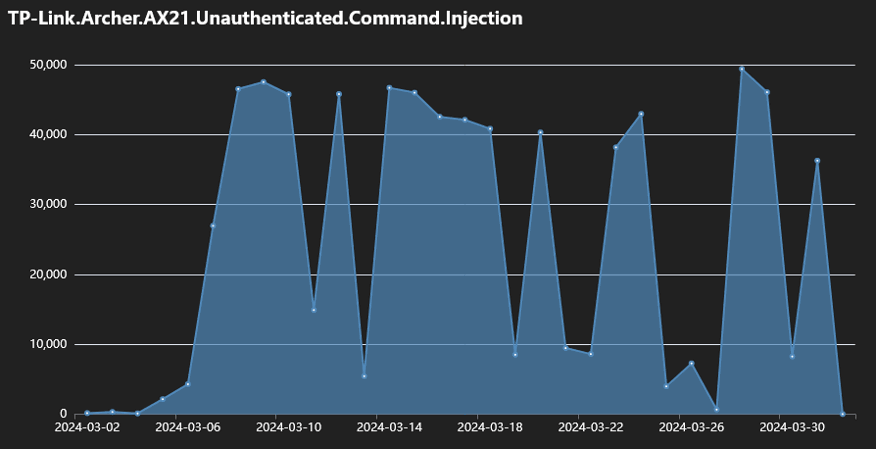
Source – Bleeping Computer
The vendor released a patch for CVE-2023-1389 in March 2023. Last year it was one of the most exploited vulnerabilities, yet there are still unpatched devices out there.
Why is the TP-Link Archer command injection vulnerability dangerous?
Postponing or overlooking patching tasks turns TP-Link Archer routers vulnerable. The TP-Link Archer Command Injection Vulnerability got an 8.8 CVSS score, which means high severity.
By exploiting CVE-2023-1389 hackers can execute code remotely on the compromised devices.
Researchers say the six botnets they`ve observed use different techniques and scripts to exploit the CVE and compromise the routers. Most of the times, the attackers use victim devices for
- distributed denial of service (DDoS)
- brute force attacks
The six botnets that tried lately to exploit the TP-Link Archer Command Injection Vulnerability are:
- AGoent
- Gafgyt
- Moobot
- Miori
- Mirai
- Condi
How to protect TP-Link Archer routers against botnets
If you didn`t apply the patch for CVE-2023-1389, do it now. The patch management process is redundant and time-consuming. Also, prioritizing vulnerabilities can be complicated.
But the risks are too high to ignore, says Mikkel Pedersen, Cybersecurity Speaker & Community Leader:
not patching, leaving software vulnerable, is the same as leaving your front door unlocked. It’s an open invitation for everyone to get in and take what they want.
You can pay and buy all the tools you want. An antivirus, endpoint detection, firewalls, and everything else out there, but if you don’t patch, you’re just throwing money into a big hole and still leaving the front door unlocked.
To keep up with the variety of software that needs updating, use an automated patch management solution. Top patch management software will help close vulnerabilities faster and take the pressure off the IT team.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and Youtube, for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security







