Contents:
Even if nowadays everybody uses cloud-based services when it comes to all sorts of attachments, there are lots of people who are still fond of exchanging documents, pictures, or information via email. As sending large files via email services can be a bit challenging sometimes, WeTransfer became very popular among its users.
WeTransfer is an internet-based computer file transfer service that was created to make it easier to share large files.
A new social engineering attack recently discovered by a cybersecurity organization imitates a file-sharing notification that seems to be sent from the well-known WeTransfer service, a platform used by both businesses and individuals.
The phishing email appears to be authentic as it comes from WeTransfer and has the title View Files Sent Via WeTransfer.
How It Works
The victims receive an email that has two files supposedly from WeTransfer and there is also a link to view them.
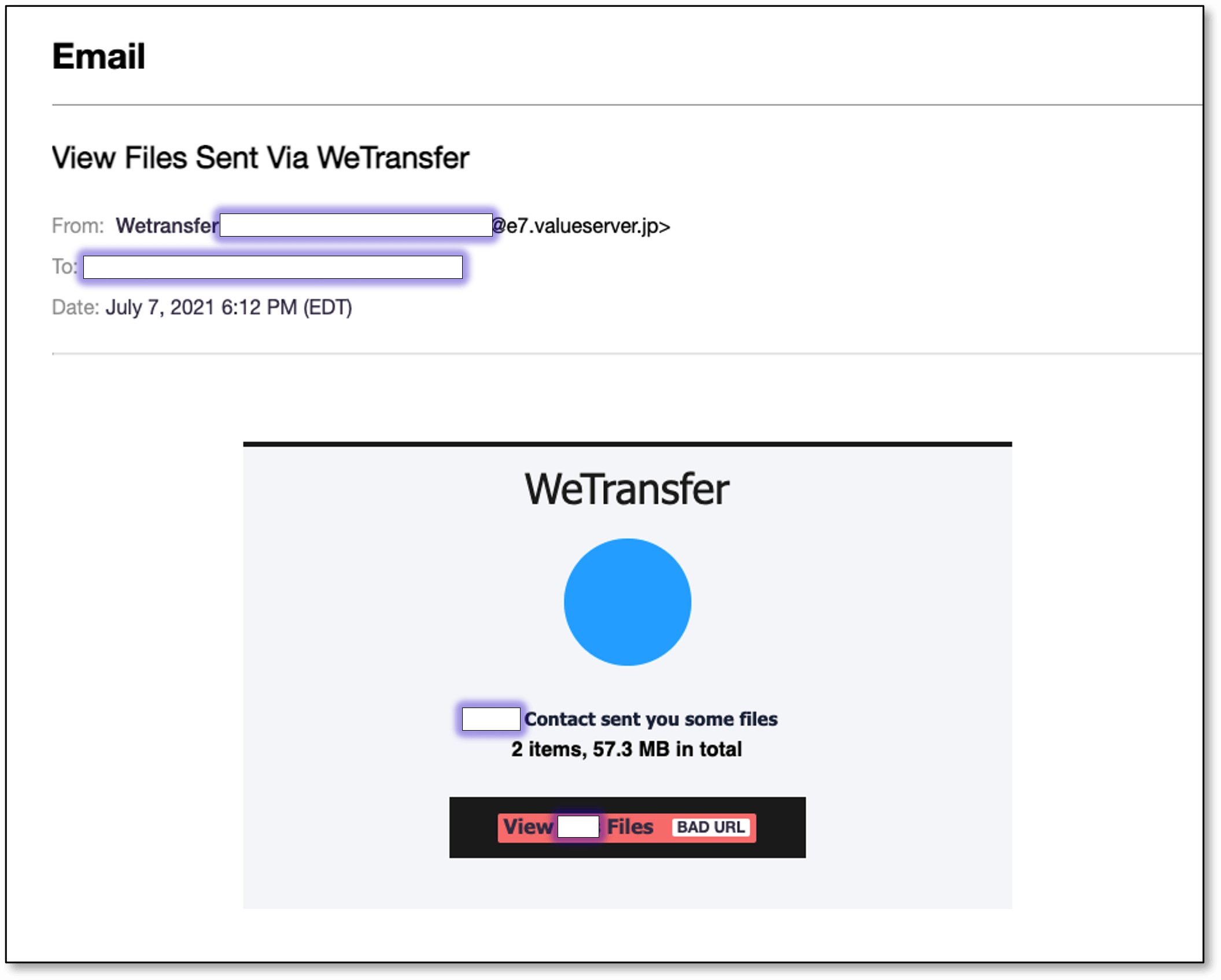
As per cybersecurity firm Armorblox report, the email link leads to a phishing website filled with Microsoft Excel branding. The main objective of the phishing operation is to collect the victim’s Office 365 email credentials.
The resemblance is enough to look like an authentic WeTransfer email and can easily trick unwary potential victims. The message is also mentioning the target company several times in order to seem legit.
Mark Royall, senior solutions engineer at Armorblox stated:
The email title, sender name, and content aimed to induce a sense of trust and urgency in the victims — a sense of trust because the email claimed to come from a legitimate company (WeTransfer), and a sense of urgency because it claimed the victim was sent some files — files they would be eager to view.
The context of this attack also leverages the curiosity effect, which is a cognitive bias that refers to our innate desire to resolve uncertainty and know more about something.
The report shows the fake Microsoft Excel page has a blurred-out spreadsheet as the background, and a form is displayed in the foreground asking the target to fill out login information. The victim’s email address is already pre-filled in the form in order to make the whole process look authentic.
Techniques Used in The WeTransfer Phishing Attack
- Social engineering – as the email title, content, and sender name has been created to make the victims believe the process is legitimate
- Brand impersonation – the phishing page has been designed to impersonate Microsoft Excel’s authentic login page
- Replicating existing workflows – sending files online
It is essential to be aware of minor changes in the sender’s name, email address, and domain name. Look carefully at the language hackers use within the email.
Also, implementing multi-factor authentication (MFA) on all personal and business accounts should be a top priority nowadays. And remember! Never use the same password for accessing different accounts.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








