Contents:
As you might remember, back in July a massive ransomware attack took place. Managed service providers worldwide took a huge hit when the REvil gang launched an attack against them by exploiting a zero-day vulnerability in Kaseya VSA remote management application.
In the attack almost sixty managed service providers got encrypted, and with them around 1,500 businesses suffered.
Soon after the attack, the malicious actors asked for a $70 million ransom in order to provide the victims with a universal decryptor that could be used in order to decrypt the victims of the ransomware attack.
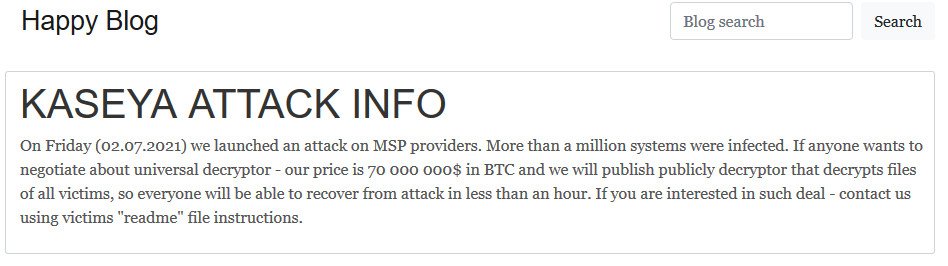
Just a few days after, something unexpected happened and the REvil ransomware gang mysteriously disappeared.
The ransomware gang’s Tor payment sites and infrastructure were shut down also, thus making it impossible for the companies who may have needed to purchase a decryptor to do so.
Kaseya managed to get a universal decryption key for the ransomware attack from what was described at that time as a mysterious “trusted third party” and began distributing it to affected customers.
Decryption Key Leaked
Recently, the security researcher Pancak3 disclosed to the journalists at BleepingComputer that someone posted a screenshot of what they claimed to be a universal REvil decryptor on a hacking forum.
#kaseya master key?
OgTD7co7NcYCoNj8NoYdPoR8nVFJBO5vs/kVkhelp2s=https://t.co/yq820cMkAg pic.twitter.com/4OBJ4i3UAh
— pancak3 (@pancak3lullz) August 10, 2021
The post about the Kaseya decryptor was linked to a screenshot found on GitHub that showed a REvil decryptor running while displaying a base64 hashed ‘master_sk’ key, having the key ‘OgTD7co7NcYCoNj8NoYdPoR8nVFJBO5vs/kVkhelp2s=’.
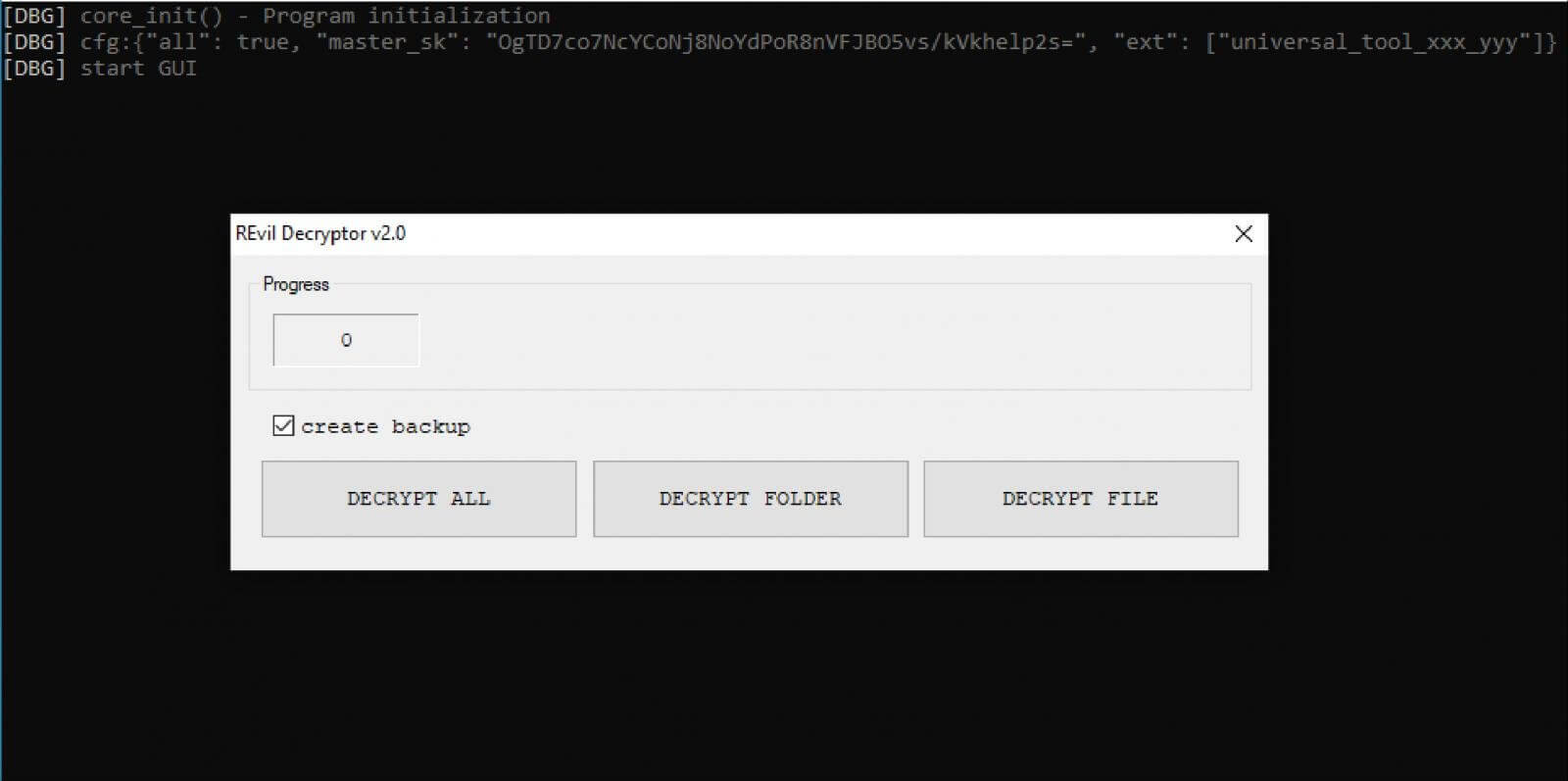
If the ransomware victims paid the requested ransom, they would qualify to receive a decryptor that works for a single encrypted file extension or a universal decryptor that works for all encrypted file extensions used in a particular campaign or attack.
At first glance, the key that was leaked looked like a universal REvil decryptor that can decrypt all extensions associated with the attacks conducted by REvil but later proved to be more specific and not able to decrypt all REvil encrypted files as it has been hoped.
The leaked key was tested by BleepingComputer. They started by patching a REvil universal decryptor with the decryption key leaked in the screenshot, and after applying a patch to the decryptor, they encrypted a virtual machine with some of the REvil ransomware samples used in the Kaseya attack.
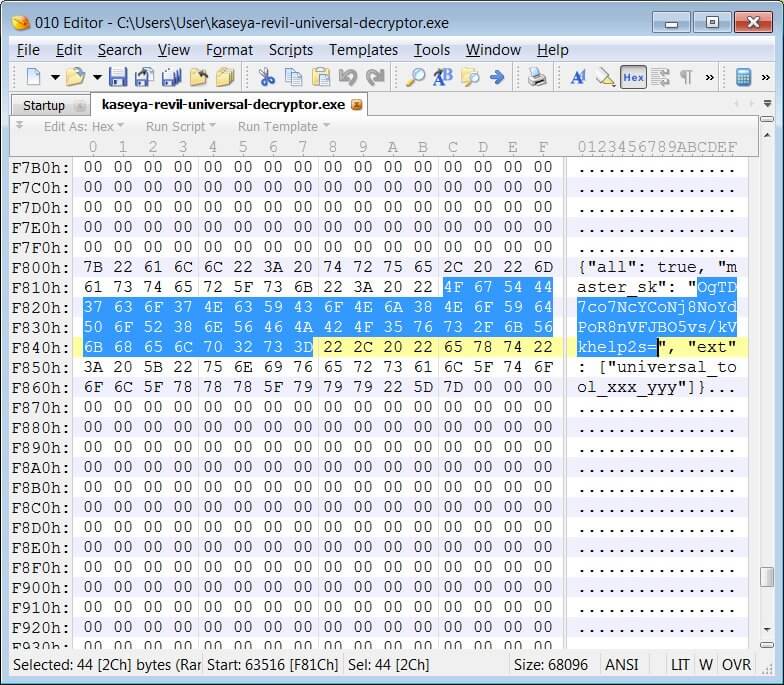
The patched REvil universal decryptor was then used to decrypt the encrypted files successfully.
At this time it is unclear why the Kaseya decryptor was posted on a hacking forum, as this would be an unlikely place for a victim to post.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security