Contents:
Nimbuspwn is a name given to two Linux privilege escalation problems identified by the Microsoft 365 Defender Research Team. These vulnerabilities (recorded as CVE-2022-29799 and CVE-2022-29800) may be exploited by attackers to carry out a variety of harmful operations, including the distribution of malware.
The Nimbuspwn Security Flaw
A directory traversal vulnerability, a symlink race vulnerability, and a time-of-check-time-of-use (TOCTOU) race condition vulnerability are all described as Nimbuspwn.
Microsoft has discovered several vulnerabilities, collectively referred to as Nimbuspwn, that could allow an attacker to elevate privileges to root on many Linux desktop endpoints. The vulnerabilities can be chained together to gain root privileges on Linux systems, allowing attackers to deploy payloads, like a root backdoor, and perform other malicious actions via arbitrary root code execution. Moreover, the Nimbuspwn vulnerabilities could potentially be leveraged as a vector for root access by more sophisticated threats, such as malware or ransomware, to achieve greater impact on vulnerable devices.
We discovered the vulnerabilities by listening to messages on the System Bus while performing code reviews and dynamic analysis on services that run as root, noticing an odd pattern in a systemd unit called networkd-dispatcher. Reviewing the code flow for networkd-dispatcher revealed multiple security concerns, including directory traversal, symlink race, and time-of-check-time-of-use race condition issues, which could be leveraged to elevate privileges and deploy malware or carry out other malicious activities. We shared these vulnerabilities with the relevant maintainers through Coordinated Vulnerability Disclosure (CVD) via Microsoft Security Vulnerability Research (MSVR). Fixes for these vulnerabilities, now identified as CVE-2022-29799 and CVE-2022-29800, have been successfully deployed by the maintainer of the networkd-dispatcher, Clayton Craft. We wish to thank Clayton for his professionalism and collaboration in resolving those issues. Users of networkd-dispatcher are encouraged to update their instances.
An attacker with low privileges on the system might exploit the vulnerabilities in order to escalate to root-level rights by delivering an arbitrary signal to the target system.
The procedures required for effective exploitation are shown in the diagram below, which includes three phases of the attack: reconnaissance, reconnaissance, and exploitation.
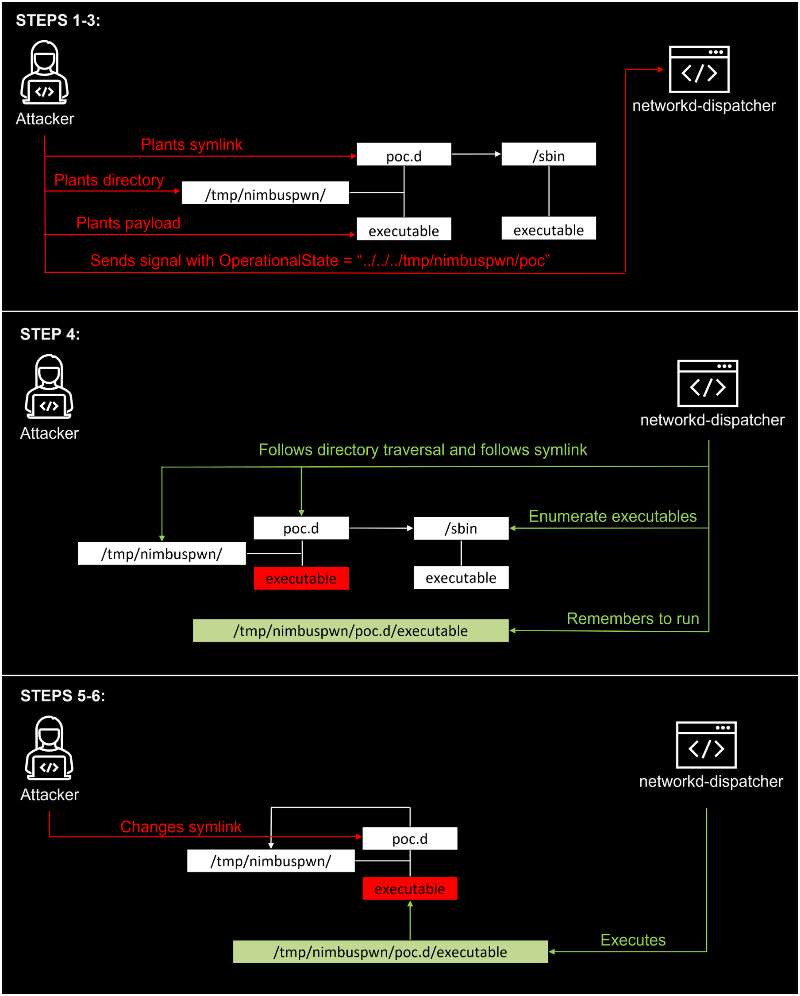
As BleepingComputer reports, it is feasible to use Nimbuspwn successfully if the exploit code can get ownership of a bus name under the control of a privileged service or process.
Affected systems are vulnerable to attacks that allow attackers to get root access and then distribute more sophisticated threats such as ransomware on the systems they target.
The weaknesses are located in a systemd component named networked-dispatcher, which serves as a dispatcher daemon for changes in the state of systemd-networked connections.
Following an examination of the code flow for networkd-dispatcher, it was discovered that there were a number of security problems, including directory traversal, symlink race, and time of check vs time of usage race condition issues.
Beginning with services that run as root and listen for messages on the System Bus, the researchers performed both code reviews and dynamic analysis on the services they discovered.
An attacker in charge of a rogue D-Bus service that has the ability to emit an arbitrary signal might use the flaws to his advantage by deploying a backdoor on the compromised final touches.
Several settings, including Linux Mint, are susceptible to this, including “the service systemd-networkd, which ordinarily owns the “org.freedesktop.Network1”.
It is suggested that Linux users patch their systems as soon as the necessary updates are made available for their operating system of choice.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










