Contents:
This vulnerability results from the way in which “net” treats IP addresses as a decimal.
Therefore, even when the IPs are provided in a mixed (octal-decimal) format, any applications relying on ”net” could become vulnerable to Server-Side Request Forgery (SSRF) and Remote File Inclusion (RFI) vulnerabilities.
At the latest edition of DEF CON the security researchers Cheng Xu, Victor Viale, Sick Codes, Nick Sahler, Kelly Kaoudis, opennota, and John Jackson disclosed a flaw found in the ”net” module of the Go and Rust languages.
The vulnerability tracked as CVE-2021-29922 (for Rust) and CVE-2021-29923 (for Golang) raises concerns related to the way in which “net” can handle mixed-format IP addresses, or more specifically when a decimal IPv4 address contains a leading zero.
This is a concerning fact as by simply searching for “import “net” on GitHub over 4 million files that can be potentially attacked are found for the Go language alone.
As you might already know an IP address can be represented in a variety of formats, with one of them being hexadecimal and integer, but most commonly seen IPv4 addresses are expressed in the decimal format.
As explained by the journalists at BleepingComputer, if we take an IP address found in its decimal format, 127.0.0.1 and as prefix a 0 to it and type it in Chrome’s address bar, we’ll see that the browser is treating it as an IP in octal format.
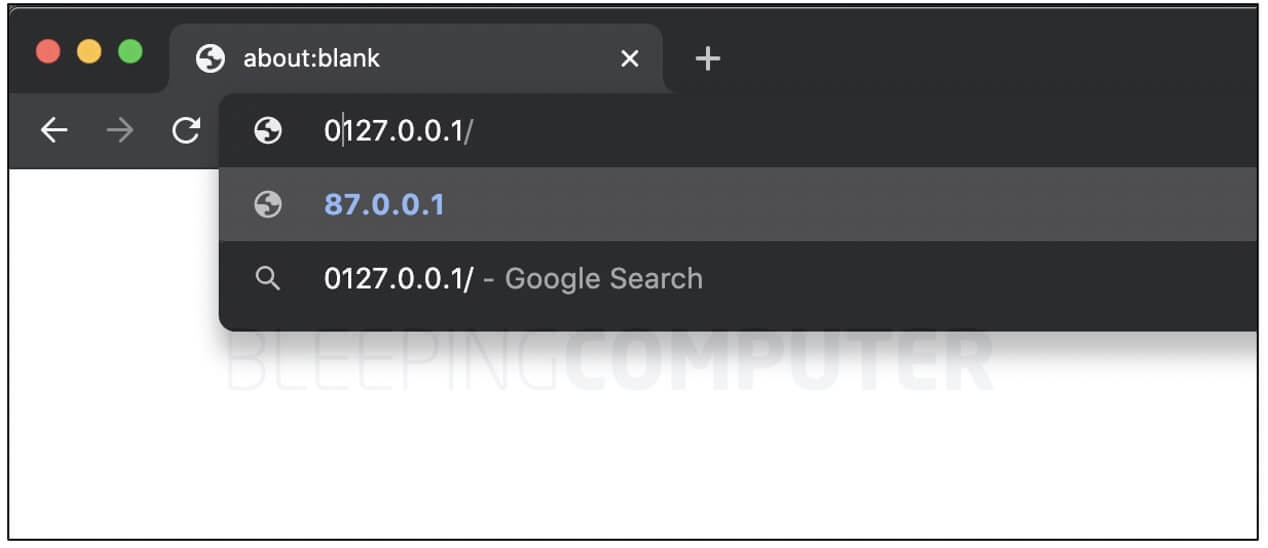
When pressing enter or return, the IP changes to its decimal equivalent of 87.0.0.1, which is how most applications are supposed to handle such ambiguous IP addresses.
It seems that parts of an IPv4 address can be interpreted as octal if prefixed with a “0”, as explained in an IETF draft, therefore the rules around how a mixed-format IPv4 address should be parsed vary between applications.
The “net” module in both Go and Rust considers all octets of an IPv4 address as a decimal.
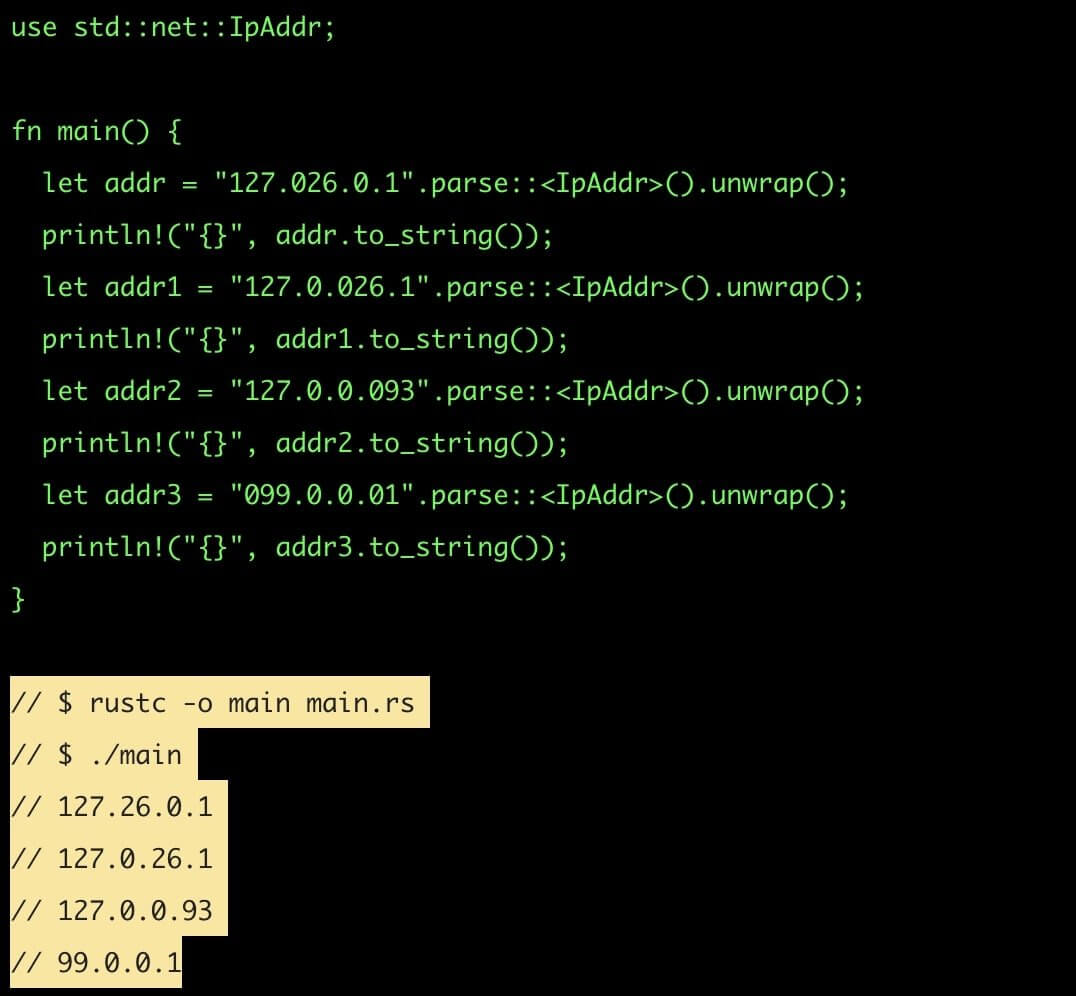
This means that if a developer was using ”net” in order to validate the fact that an IP address belongs to a certain range the result may be wrong for octal-based representations of IPv4 addresses, and this can actually cause indeterminate Server-Side Request Forgery (SSRF) and Remote File Inclusion (RFI) vulnerabilities in applications.
Other Applications Aside From Go and Rust Also Impacted
It looks like this mixed-format IP address validation bug had previously impacted Python’s IP address library (CVE-2021-29921), “net” mask implementations (CVE-2021-28918, CVE-2021-29418), and similar libraries, and in most cases was rated as being of a High or Critical severity.
Fortunately, a fix has already been merged in the ”net” library for Rust, meaning that the users should be using version 1.53.0 or above that contains the mitigations for this vulnerability.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security