Contents:
Heimdal’s Incident Investigation and Response Department has recently unearthed a new type of phishing campaign that randomly targets TDC customers. The forensic analysis performed on malicious samples retrieved from an anonymous client revealed that the perpetrator(s) lured in TDC clients, by offering various, high-value prizes. Coined the TDC Phishing Campaign, it has, so far, been successful at avoiding detection nets, by disguising itself in a seemingly legitimate Google Ad.
Overview
The investigation (ongoing) has identified that the perpetrator is using a ‘rogue’ domain to send illegitimate ‘sponsored’ ads to TDC customers. No discernable pattern has been identified so far.
However, based on the available information, we have inferred that the malicious actor(s), could have gained access, through fraudulent means, to a TDC database, and begun sending fake ads to clients that have signed up with the Danish ISP in a one-year timeframe.
In regards to the dissemination vector, Heimdal has discovered that the fraudulent ads originate from a Hong Kong-registered domain (in accordance with intel retrieved from Whois):
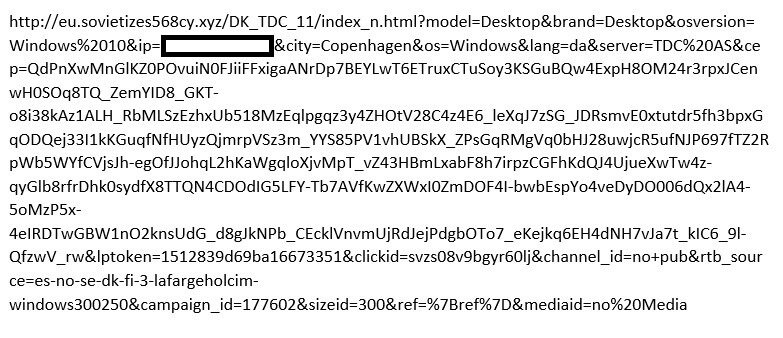
The malignant, Hong Kong-based domain, which is registered under a fictitious company, appears to have been created three days prior to the discovery of the first fraudulent pushed ad. From the intelligence we have gathered, there’s no evidence to suggest financial losses for TDC customers.
In analyzing the TDC Phishing Campaign, we have discovered that the potential victims were lured in with fake prizes consisting of high-end electronics: iPhone XS, Apple Watch or iPhone 11 Pro.
Allegedly, these prizes were offered either on a fidelity basis or as part of a fake TDC anniversary which, according to the ‘official’ version, should last for the next seven days (from March 8th until the 15th). Only 10 winners are selected from a list of thousands. The winners’ IPs are drawn from what we believe to be a TDC database, extracted through fraudulent means.
TDC Phishing Campaign: An In-depth analysis.
Outlined here are the findings in the case of the emergent phishing campaign.
The ad doesn’t have a pre-established point of origin: it can activate itself while using social media, doing online shopping or surfing the Internet. Upon click or tap action, the user is redirected to a domain that is allegedly owned or associated with TDC. Once the page loads, the user is greeted with the following message:
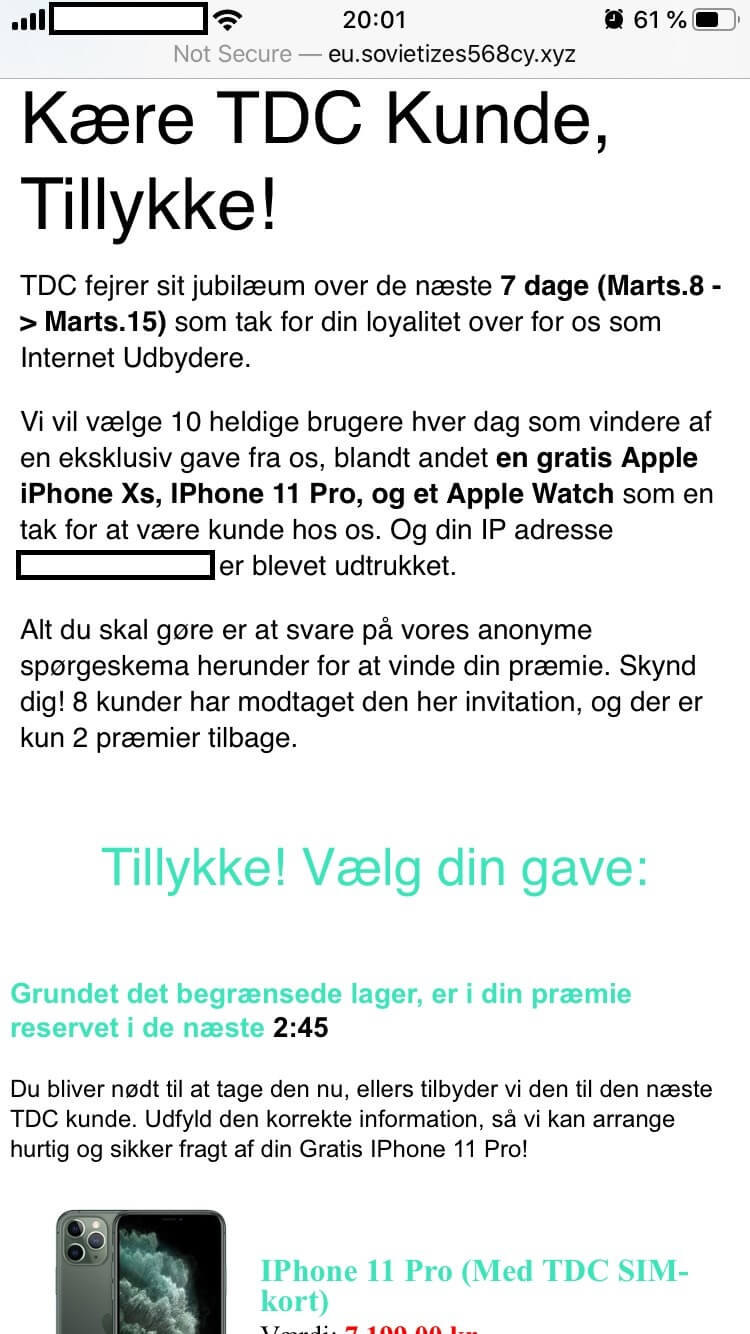
Dear TDC Customer, congratulations!
TDC celebrates its anniversary over the next 7 days (March 8 -> March 15) as a thank you for your loyalty to us as Internet Providers. We will select 10 lucky users each day as winners of an exclusive gift from us, including a free Apple iPhone Xs, iPhone 11 Pro, or an Apple Watch as a teen thank you for being our customer.
And your IP address xx.xxx.xxx.xxxx has been extracted. All you have to do is answer our anonymous questionnaire below to win your prize. Hurry up! 8 customers have received this invitation and there are only 2 prizes left.
Congratulations! Choose your gift.
Due to the limited stock, your premium is reserved for the next 2:45. You will need to take it now, otherwise, we will offer it to the nearest TDC customer. Fill in the correct information so we can arrange fast and secure shipping of your Free iPhone 11 Pro!
(Translated from Danish)
The message body is crafted as to imitate TDC or a partner: the user’s IP, the overall design, and even a dedicated (and fake) customer review section that reinforces the illusion.
At this point, the victim, having some measure of certainty that he/she is the winner of TDC’s unannounced sweepstakes, will proceed to select the desired prize. As you can see from the attached images, not all of the devices are ‘in stock’. Should the victim choose a prize that is not available, the following message will appear on the screen:
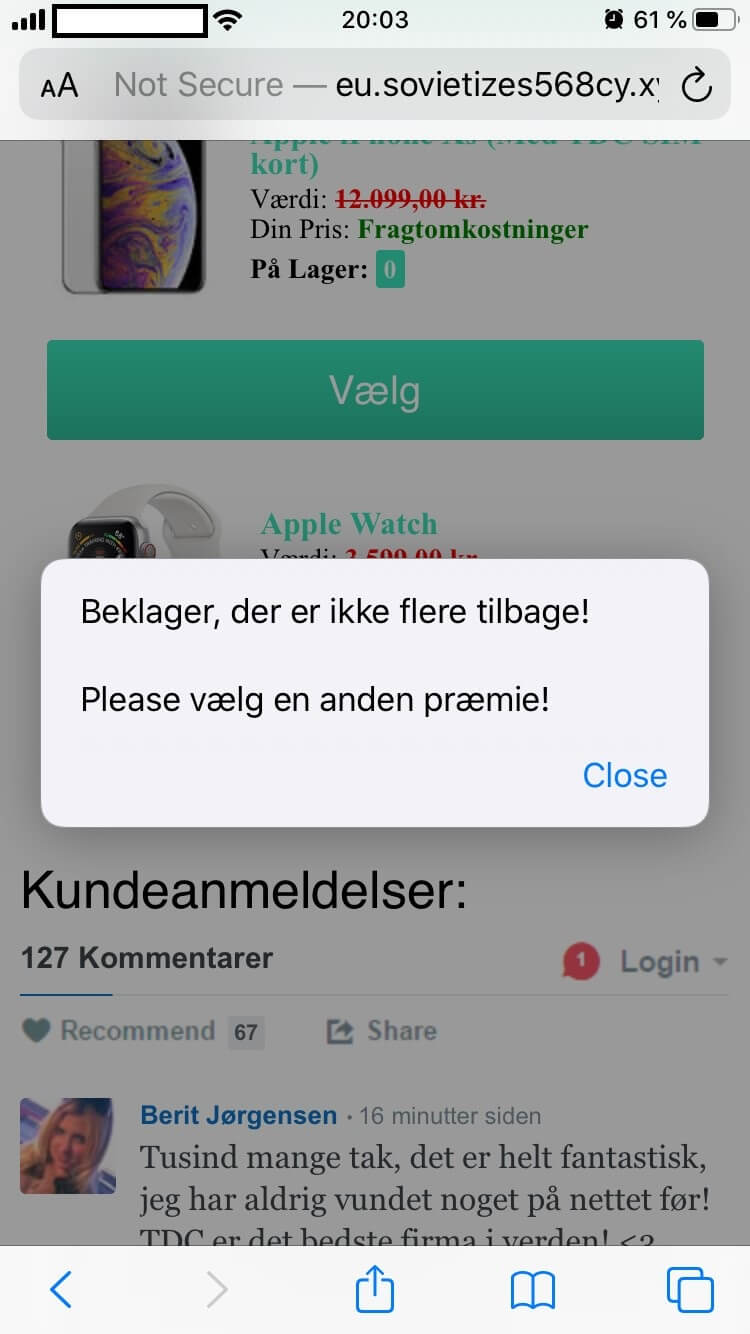
“Sorry, there are no more left! Please choose another prize!”
(Translated from Danish)
To proceed, the victim will have to select an available item. Clicking or tapping on the “Select” action button located underneath each item, will take the victim to a brief, experience-assessment survey. Upon completing the fake questionnaire, the user will be informed that some personal information such as email, address, and name are required to complete the transaction.
Furthermore, the victim is also informed that despite the selected device is free of charge, he/she must post shipping and handling fees to take possession of the prize. Should you choose to proceed, you will be redirected to a secondary domain (and spoofed domain) where you are required to enter debit/credit information
Upon completing the transaction, the amount corresponding with the shipping and handling fees will be deducted from the victim’s account. Unfortunately, the malicious actor would have also gained access to sensitive information which will, undoubtedly, be transacted on the dark web.
Fake customer reviews are appended at the end of the text body to preserve homogeneity.
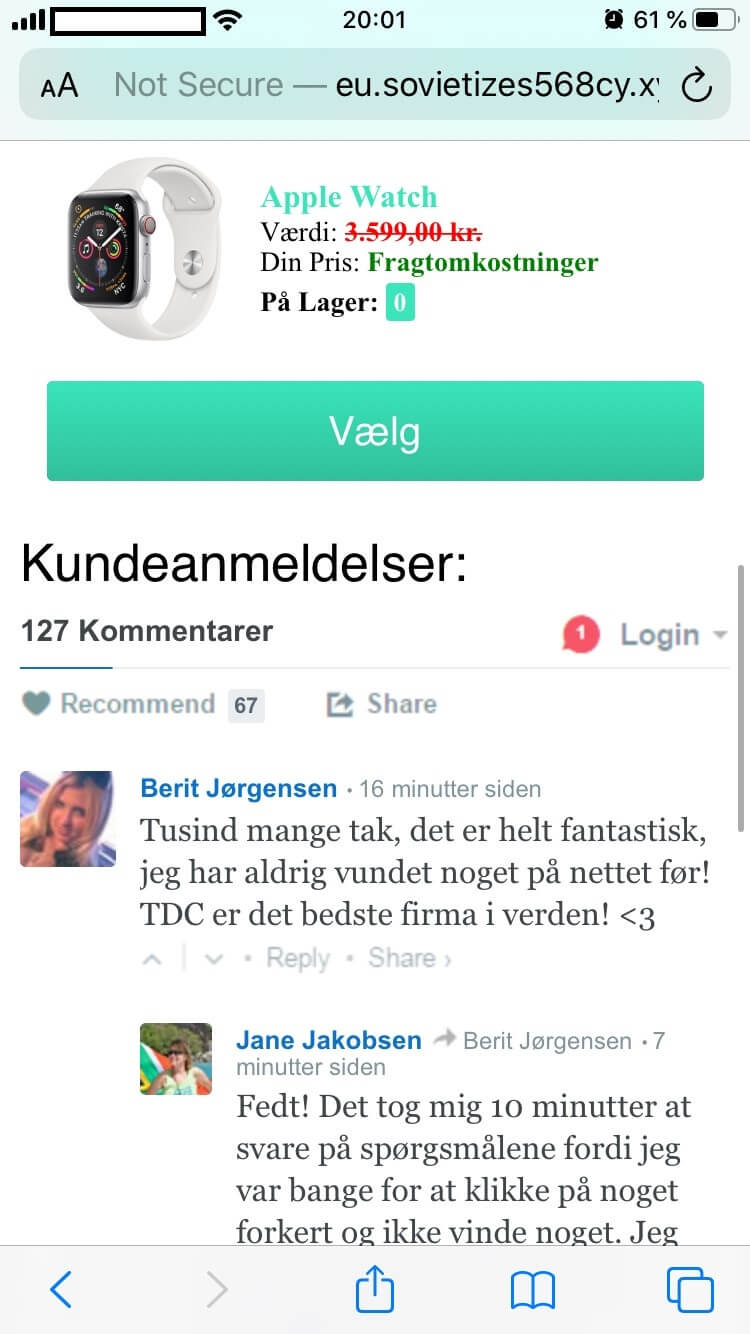
Berit Jorgensen: ‘Thank you very much, it is absolutely amazing, I have never won anything on the net! TDC is the best company in the world!’
Jane Jacobsen (In reply to Berit Jorgensen): ‘Cool! It took me 10 minutes to answer the questions because I was afraid of clicking something wrong you didn’t win anything.’
The malicious campaign also appears to have an anti-detection mechanism: if too many attempts are made, the website in question will return a “400 Bad Request” error message.
(Translated from Danish)
Anti-phishing cybersecurity tips
Below, you will find a short, but comprehensive list of tips on how to guard yourself or your organization against phishing attempts.
Avoid opening suspicious-looking ads
Bear in mind that some Google ads you may come across are not malicious. However, this doesn’t mean that you should open everyone, just because the item looks interesting or was on your Wishlist (those can be tracked across apps and platforms). If you do open an ad, make sure it has the HTTPS certificate – check for the padlock icon next to the link.
Deploy and employ next-gen anti-phishing protection
Some phishing attempts, such as the one we’ve discussed, employ a sophisticated anti-detection mechanism, allowing them to get past your antivirus. To counter these threats, you use an anti-malware solution that looks beyond the ‘file’ and ‘code’ level.
Heimdal™ Threat Prevention, Heimdal™ Security’s award-winning DNS-filtering solution, can prevent threats from reaching your machine by blocking traffic to and from any malicious C&C server.

Heimdal® DNS Security Solution
- Machine learning powered scans for all incoming online traffic;
- Stops data breaches before sensitive info can be exposed to the outside;
- Advanced DNS, HTTP and HTTPS filtering for all your endpoints;
- Protection against data leakage, APTs, ransomware and exploits;
Too good to be true!
It’s the golden rule of the Internet: if something looks too good to be true, then it’s, most likely a scam. So, if some website requests very personal info to take possession of some fabulous prize, then it’s a scam. Also, keep in mind that anniversary sweepstakes, such as the one mentioned in the fake ad, are usually announced on the company’s website.
Wrap-up
The TDC phishing campaign is what in vernacular is called ‘the oldest trick in the book.’ Fake prizes offered through bogus sweepstakes go back to the beginning of the Internet era. As always, the best defense against such threats is vigilance.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security









