Contents:
A security notice related to a SonicWall critical vulnerability in SMA 100 series devices has been issued by the enterprise. The flaw we are talking about was classified in the CVE range under CVE-2021-20034. If successfully exploited, this could allow a cybercriminal to delete random files from the before mentioned devices and achieve admin rights. That is why the company urges users to patch it as soon as possible.
About the SonicWall Critical Vulnerability
An inaccurate file path to a restricted directory limitation is the cause of the SonicWall critical vulnerability. This means that cybercriminals can perform their malicious actions, more specifically deleting arbitrary files from the SMA series appliances without even authenticating. They could do it by bypassing path traversal checks. Then a reset to factory default settings could be performed. This eventually will only lead to hackers having admin access over the targeted host, access that could be achieved via default credentials accessible after the reboot.
The score that the Common Vulnerabilities and Exposures (CVE) database attributed to this SonicWall critical vulnerability is 9.1 out of 10. However, there is no confirmation at the present moment that the bug is being exploited.
What Devices Are Affected?
The same security advisory offered details on the affected devices. See the list below:
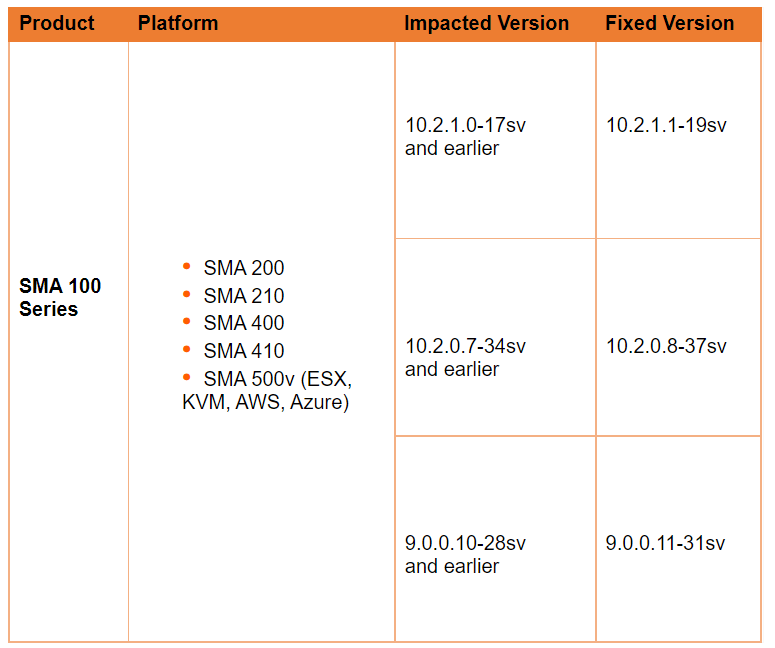
What Can Be Done Against the SonicWall Critical Vulnerability?
As recommended by the company, enterprises that make use of SMA 100 series devices should go to MySonicWall.com. This way, they can upgrade the devices and implement the patched versions mentioned in the table above. If there is upgrade support needed, the company also provided a list of instructions in KB “How to Upgrade Firmware on SMA 100 Series Appliances” and has also a support team available to help customers.
The patches outlined in the table also fix the flaws in SNWLID-2021-0020 and SNWLID-2021-0022.
The company, therefore, urges its impacted customers to start the implementation of the existing patches ASAP.
SonicWall is basically a securing networking specialized enterprise with its headquarters in Silicon Valley. Services for unified threat management (UTM) or network firewalls are what their devices provide.
It’s interesting to mention that it’s not the first time SonicWall 100 series appliances are targeted. We also wrote in July about how HelloKitty ransomware was targeting an old vulnerability in these devices in a massive campaign focused on stolen credentials.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










