Contents:
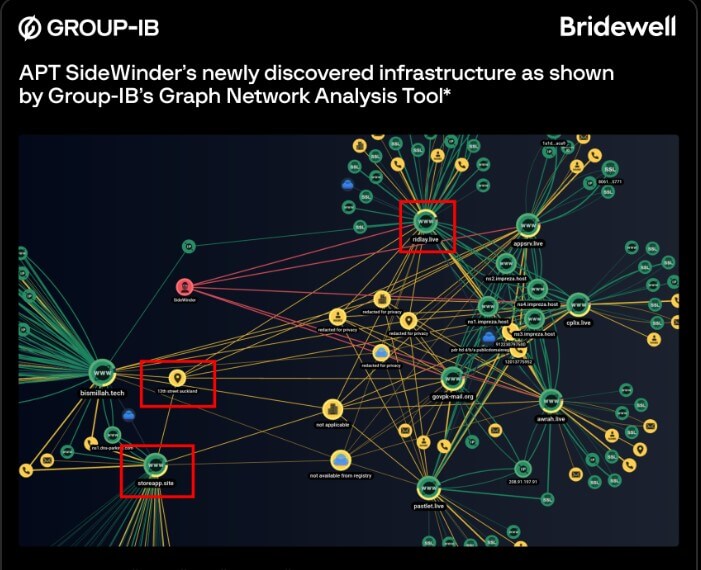
Researchers have uncovered previously unknown attack infrastructure used by Pakistani and Chinese entities operated by the state-sponsored group SideWinder. In a joint report, cybersecurity companies Group-IB and Bridewell say the threat actor uses 55 domains and IP addresses.
At least since 2012, SideWinder has been active, using spear-phishing attacks to gain access to targeted environments. Among the nations most frequently attacked by this group are Pakistan, China, Sri Lanka, Afghanistan, Bangladesh, Myanmar, the Philippines, Qatar, and Singapore.
Key Findings
According to the report, between June and November 2021, SideWinder may have targeted 61 government, military, law enforcement, and other organizations across Asia.
Recently, the nation-state group was observed utilizing server-based polymorphism in evasive attacks against Pakistani government organizations. The newly discovered domains mimic government organizations in Pakistan, China, and India. Various government-themed lure documents are hosted on some of these domains in order to download unknown next-stage payloads.
Most of these documents were uploaded in March 2023 from Pakistan. All in all, the domains indicate that SideWinder targets financial, government, and law enforcement organizations, as well as Chinese and Pakistani companies dealing with e-commerce and mass media.
According to THN, a Windows shortcut file (LNK) uploaded to VirusTotal in late November 2022 was also uncovered. It is designed to run an HTML application (HTA) retrieved from a remote server that spoofs the email system of Tsinghua University (mailtsinghua.sinacn[.]co). A similar LNK file uploaded around the same time from Kathmandu fetches an HTA file from a domain that masquerades as a Nepalese government website (mailv.mofs-gov[.]org).
Furthermore, the investigation into SideWinder’s infrastructure has led to the discovery of a malicious Android APK file (226617), a rogue Android game, the app asks users to grant it access to their contacts, location, phone logs, SMS messages, and calendar, effectively acting as spyware capable of harvesting sensitive information.
Like many other APT groups, SideWinder relies on targeted spear-phishing as the initial vector. […] It is therefore important for organizations to deploy business email protection solutions that detonate malicious content.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and YouTube for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security







