Contents:
Recently four new security vulnerabilities were found in Sage X3 enterprise resource planning (ERP) product.
Out of the 4 vulnerabilities, two seem to be chained together as part of what could be an attack sequence able to allow adversaries to execute malicious commands in order to take control of vulnerable systems.
Rapid 7 Researchers notified the vulnerabilities they found on the 3rd of February this year.
Sage X3 Version 9 (Syracuse 9.22.7.2), Sage X3 HR & Payroll Version 9 (Syracuse 9.24.1.3), Sage X3 Version 11 (Syracuse 11.25.2.6), and Sage X3 Version 12 (Syracuse 12.10.2.8) had these flaws patched in the updates shipped in March.
- CVE-2020-7388 (CVSS score: 10.0) – Sage X3 Unauthenticated Remote Command Execution (RCE) as SYSTEM in AdxDSrv.exe component
- CVE-2020-7389 (CVSS score” 5.5) – System “CHAINE” Variable Script Command Injection (No fix planned)
- CVE-2020-7387 (CVSS score: 5.3) – Sage X3 Installation Pathname Disclosure
- CVE-2020-7390 (CVSS score: 4.6) – Stored XSS Vulnerability on ‘Edit’ Page of User Profile
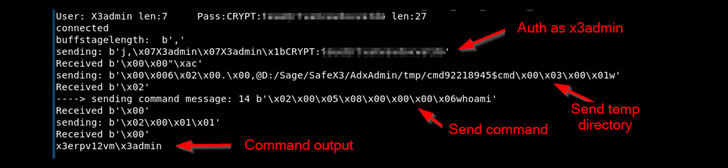
When combining CVE-2020-7387 and CVE-2020-7388, an attacker can first learn the installation path of the affected software, then use that information to pass commands to the host system to be run in the SYSTEM context.
This can allow an attacker to run arbitrary operating system commands to create Administrator-level users, install malicious software, and otherwise take complete control of the system for any purpose.
The most severe of all issues is the CVE-2020-7388, as this vulnerability takes advantage of an administrative service that’s accessible over the internet to craft malicious requests with the goal of running arbitrary commands on the server as the “NT AUTHORITY/SYSTEM” user, service that is being used for the remote management of the Sage ERP solution through the Sage X3 Console.
A separate vulnerability seems to exist on the ‘Edit page that is associated with user profiles in the Sage X3 Syracuse web server component making it vulnerable to a stored XSS attack (CVE-2020-7390). This vulnerability could be enabling the execution of arbitrary JavaScript code during ‘mouseOver’ events in the ‘First name’, ‘Last name’, and ‘Email’ fields.
If successful, however, this vulnerability could allow a regular user of Sage X3 to execute privileged functions as a currently logged-in administrator or capture administrator session cookies for later impersonation as a currently logged-in administrator.
The successful exploitation of the CVE-2020-7387 can result in the exposure of Sage X3 installation paths to unauthorized users, while the CVE-2020-7389 is concerning because it’s missing authentication in Syracuse development environments, and that could be used to gain code execution via command injection.
Generally speaking, Sage X3 installations should not be exposed directly to the internet, and should instead be made available via a secure VPN connection where required.
Following this operational advice effectively mitigates all four vulnerabilities, though customers are still urged to update according to their usual patch cycle schedules.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security