Contents:
There is no shortage of phishing attacks on the Internet, of that we can be certain. The more trusted a brand is, the higher the chances cybercriminals will exploit that trust to trick users.
Unfortunately, phishing is still a very effective technique. The 2015 Verizon Data Breach Investigation Report revealed that 23% of email recipients open phishing messages and 11% click on attachments. It may not sound like much, but these numbers are actually 3 times higher than average open and click rates for legitimate email marketing campaigns.
That being said, we wanted to share this recent LinkedIn scam we spotted, which aims to collect confidential information from unsuspecting users.
LinkedIn phishing campaign details
The attack is delivered by email and many users could fall for it, as they try to get through their inbox.
The email includes the following content:
Subject line: LinkedIn is requesting files from you
From: “LinkedIn Messages” < postmaster@fnotify.com >
Date: 4 November 2016
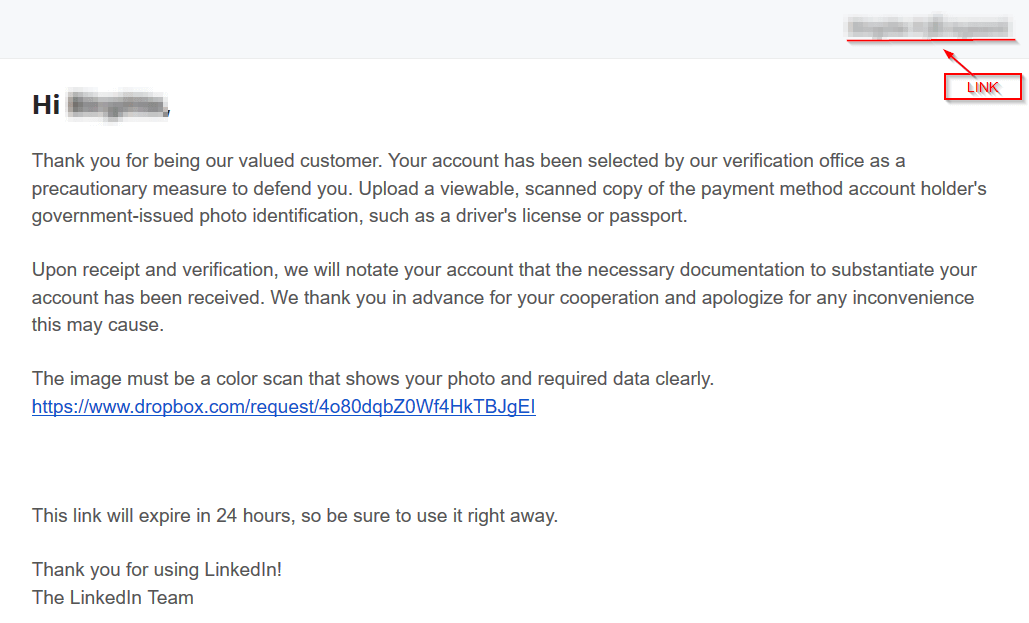
Hi [name],
Thank you for being our valued customer. Your account has been selected by our verification office as a precautionary measure to defend you. Upload a viewable, scanned copy of the payment method account holder’s government-issued photo identification, such as a driver’s license or passport.
Upon receipt and verification, we will notate your account that the necessary documentation to substantiate your account has been received. We thank you in advance for your cooperation and apologize for any inconvenience this may cause.
The image must be a color scan that shows your photo and required data clearly.
https: //www.dropbox[.]com/request[/]4o80dqbZ0Wf4[sanitized]This link will expire in 24 hours, so be sure to use it right away.
Thank you for using LinkedIn!
The LinkedIn Team
While security-savvy users may be tipped off by the “LinkedIn is requesting files from you” subject line, many who would open the email without giving it much thought.
You may be familiar with account verification procedures that ask for personal ID to confirm your identity, but they would never request you to send documents via email. Some platforms like Twitter or PayPal do have such verification procedures in place, but everything takes place on their secure website, not via email.
Aside from the ID, the email also asks for a payment receipt, so premium LinkedIn users could fall into the trick of sending their payment information. Please be aware and never send such information via email!
Another phishy aspect is the sender’s email address – postmaster [@] fnotify.com – which is no way connected to Linkedin. Upon verification, we found that http : [//]fnotify.com/ is an empty WordPress website that belongs to a Finnish citizen, which was most likely compromised to be used in this phishing campaign.
The third warning sign is that the email justifies its request by pretending they’re necessary “as a precautionary measure to defend you”. It doesn’t say what the user would be defended against, though.
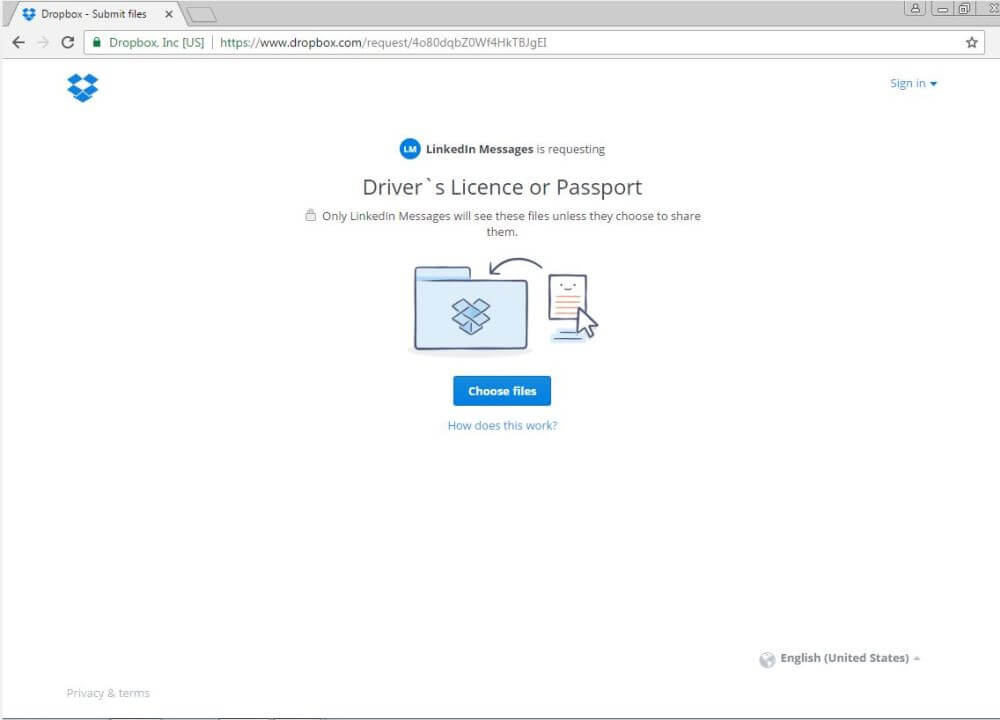
Next, the email goes on to ask that the document be uploaded to a Dropbox file, just as you can see in the screenshot below. This is the fourth trigger that should alarm you not to perform the indicated actions and compromise yourself.
The Dropbox link is clean when scanned through VirusTotal, which shows that this recent campaign has not yet been picked up by antivirus solutions.
The fifth sign that can help you identify this as a phishing attack is that the email mentions a time limit along with the other requests. This is included to pressure recipients into clicking the link and uploading the specified documents. The more time a potential phishing victim has to think, the less likely that she/he will actually comply with cybercriminals’ requests.
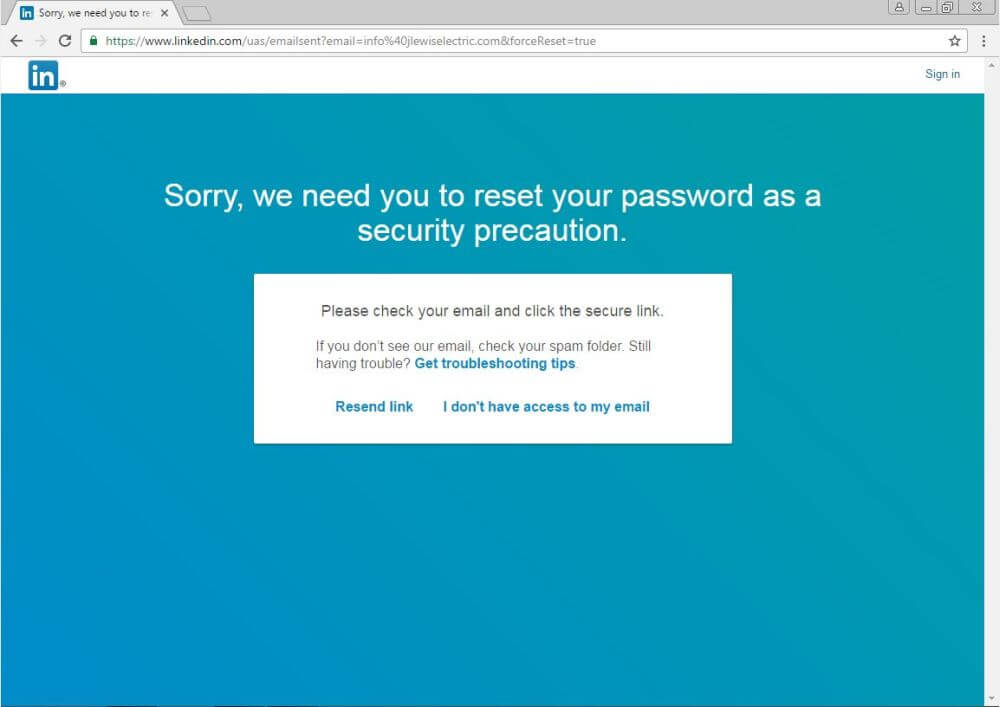
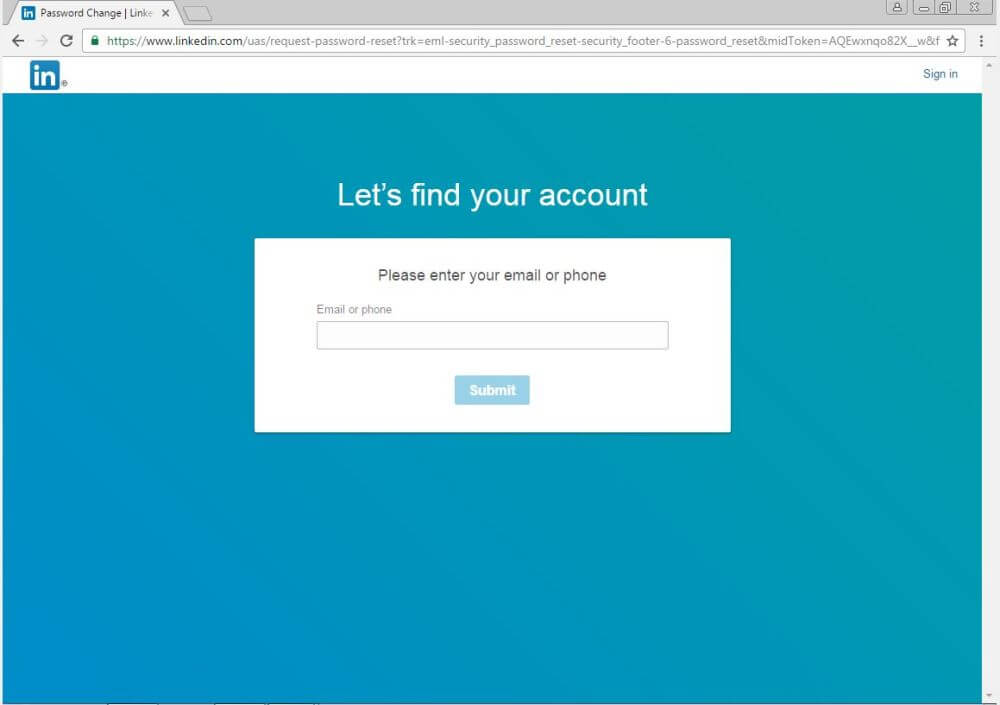
Now let’s talk about the link in the top right corner, which you can see in the screenshot below:
The link is placed on the recipient’s name and leads to a password reset page, secured by HTTPS. Strangely enough, this is actually a safe page, which could prompt the email recipients to believe that the rest of the email is valid and legitimate as well.
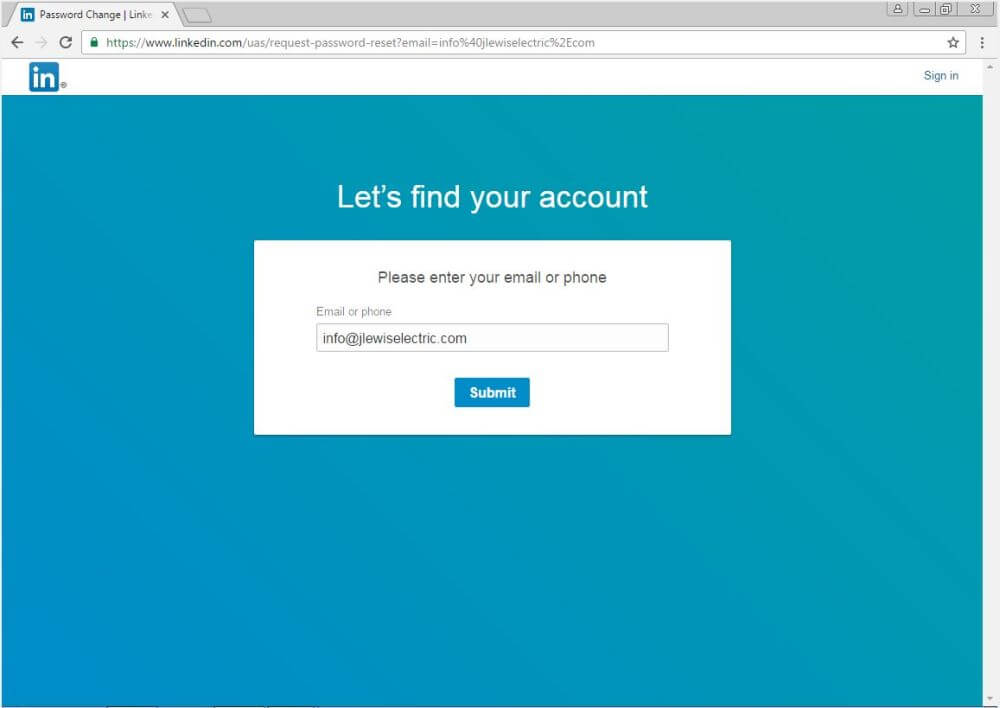
Another link on the email is placed on “I don’t have access to my email”. It leads to a password reset page, similar to the one above. The page is actually the one LinkedIn uses if you have trouble accessing your account. You can see more details in their “No Access to Email Address” FAQ.
The notable difference here is that the form on the page is prefilled with an email address belonging to a full-service electric company. Maybe the attackers forgot it there or maybe not. The reasons behind this are still unclear.
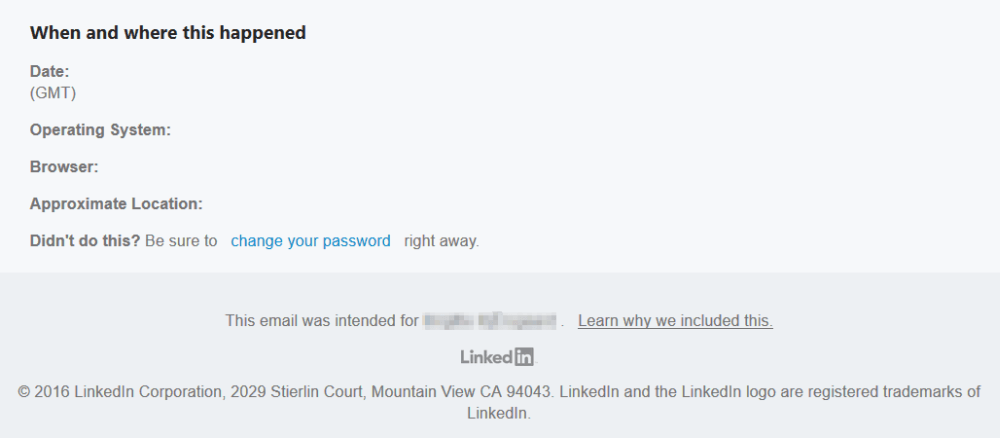
Going forward, we noticed that the footer also includes some strange information:
Maybe the attackers forgot to hide some fields, or maybe they left it like this intentionally. The fact of the matter is that the “change your password” link leads to the actual, legitimate password reset page on Linkedin.
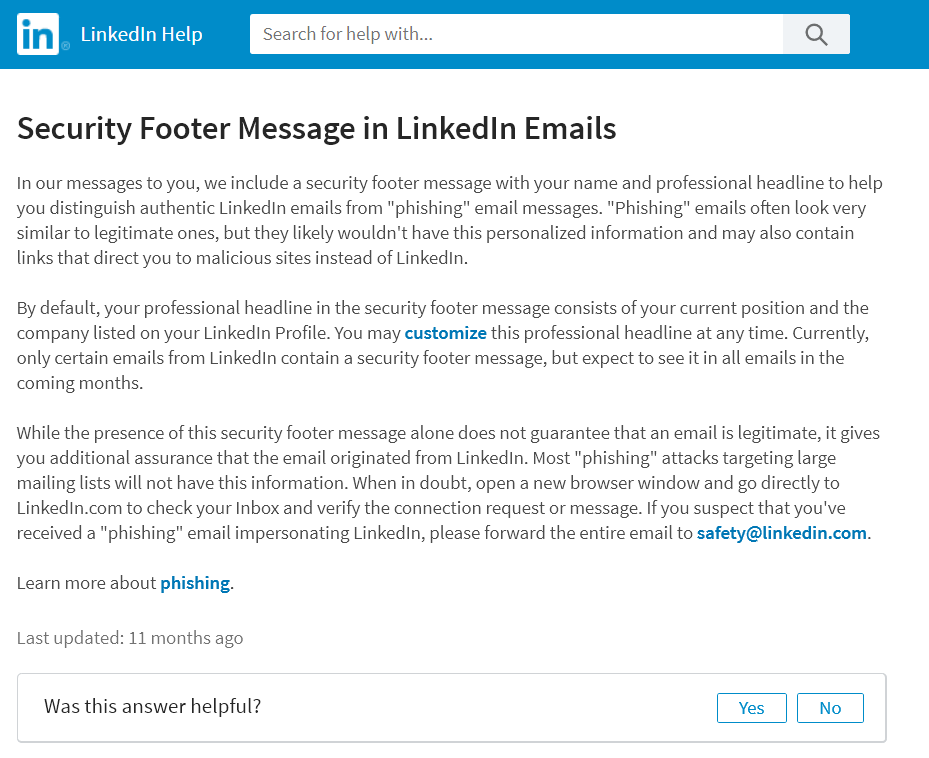
To add to the irony, the cybercriminals behind the campaign tried to replicate the footer in legitimate emails from LinkedIn, so they also kept the original link placed on “Learn why we included this.”. This leads to the page where LinkedIn explains the details behind their Security Footer Message in LinkedIn Emails.
Again, this could be intentional, to make email recipients trust the sender.
For comparison, this is what a legitimate footer from LinkedIn emails looks like:
A subtle difference is that the phishing email only includes the name of the targeted LinkedIn user in the footer, but not the recipient’s current position, as secure emails from LinkedIn do:
In our messages to you, we include a security footer message with your name and professional headline to help you distinguish authentic LinkedIn emails from “phishing” email messages. “Phishing” emails often look very similar to legitimate ones, but they likely wouldn’t have this personalized information and may also contain links that direct you to malicious sites instead of LinkedIn.
By default, your professional headline in the security footer message consists of your current position and the company listed on your LinkedIn Profile. You may customize this professional headline at any time. Currently, only certain emails from LinkedIn contain a security footer message but expect to see it in all emails in the coming months.
What’s more, the footer includes the US address, while emails sent to European LinkedIn users include the Dublin HQ address, where the legal European entity of the company works. In this case, the phishing email was targeted at European users, which is why the difference matters.
How to report a LinkedIn phishing email scam
The social media network itself offers two options:
To report phishing messages you’ve received, please email phishing@linkedin.com.
If you suspect that you’ve received a “phishing” email impersonating LinkedIn, please forward the entire email to safety@linkedin.com.
They also have a page dedicated to Advice on recognizing and reporting scams.
And if you want to report phishing scams that you come across from other sources, we included some tips in our dedicated guide for phishing protection.
At this point, we hope you’ll be better equipped to deal with this common cyber threat. This type of trap can be added to the list of common LinkedIn scams that have been endangering user data for a while now.
The reason we analyzed this particular email step by step is because Internet users are still too inclined to trust and click on phishing and scam emails. That’s why email malware distribution still works.
The right thing to do is learn about the most frequent online scams that you could come across on the Internet, and be cautious about variations and new tactics that lure you into divulging private data or installing malware on your devices.
And be sure to go through this LinkedIn security guide we put together, to keep your account safe from prying eyes.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security