Contents:
On Wednesday, at around 11:00 AM, Heimdal® representatives received a suggestive email regarding an urgent money transfer. Ensuing an internal investigation, it was discovered that the email which, purportedly, was sent by Morten Kjaersgaard, the company’s CEO, was in fact a fraud attempt. Forensics were inconclusive in this regard; the email itself appeared to be legitimate, right down to the LinkedIn address used for invoicing.
Detailing the Incident
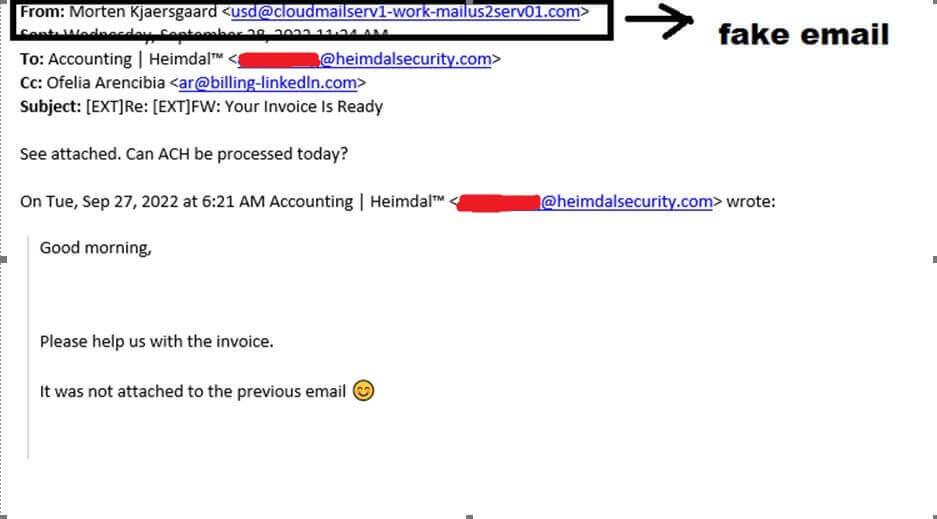
On early Wednesday, a representative of the Billing & Accounting department received an email from the company’s CEO requesting aid in processing two received LinkedIn invoices. The party posing as Morten Kjaersgaard solicited the accounting department to process these payments as soon as possible. At first glance, the email communication chain between the party posing as the CEO and accounting don’t raise any suspicions because it does not present any of the indicators associated with email fraud attempts (i.e., typos, grammatical and/or logical inconsistencies, out-of-place graphical elements, enclosed payment links, etc.). To the naked eye, this would have passed as legitimate interdepartmental communication. See picture below.
However, a closer inspection of the sender’s address revealed an inconsistency, indicating a Business Email Compromise (BEC) attempt. The address did not match the Outlook entry associated with Morten Kjaersgaard’s identity. Furthermore, the address pointed to an unknown cloud mailing service. Acting on the suspicion, the Heimdal® employee contacted the parties involved and notified forensics. The subsequent analysis performed on the email chain confirmed that it was a CEO fraud attempt, leading to Heimdal® blackmailing the domains. Apart from the dubious sender’s address, the email chain also contained two attached PDF documents. Sandboxing and blasting efforts disclosed no information on the attacker’s identity, intentions, or motivations. Both PDF documents were clean – no .vbs scripting, macros, and redirect links.
How to Prevent CEO Fraud Attempts
Such incidents are not uncommon and, according to the statistics, they are continuing to grow both in strength and in number. Per a Statista study, between 2017 and 2020, there have been over 50,000 CEO fraud attempts. More than that, according to an InfoSecurity article, the odds of success in the case of this type of attack are close to 90%.
The first line of defense against CEO fraud attacks is security training. Teaching your employees how to recognize the tell-tale signs of this attack and how they should act upon them can significantly decrease risk. More than that, email security solutions can also help you identify and respond to these types of incidents before they reach your employees. Email Fraud Prevention by Heimdal® is specifically engineered to address email-delivered fraud attempts by employing a combination of human specialists and technology.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security