Contents:
A famous hacking forum and marketplace is selling the personal information of about 7 million Robinhood users who were exposed in a recent data breach.
Last week, Robinhood announced a data breach after one of its employees was compromised, and the attacker utilized their account to gain access to the personal data of around 7 million customers via customer support systems.
Late in the evening of November 3, we experienced a data security incident. An unauthorized third party obtained access to a limited amount of personal information for a portion of our customers. Based on our investigation, the attack has been contained and we believe that no Social Security numbers, bank account numbers, or debit card numbers were exposed and that there has been no financial loss to any customers as a result of the incident.
The unauthorized party socially engineered a customer support employee by phone and obtained access to certain customer support systems. At this time, we understand that the unauthorized party obtained a list of email addresses for approximately five million people, and full names for a different group of approximately two million people.
We also believe that for a more limited number of people—approximately 310 in total—additional personal information, including name, date of birth, and zip code, was exposed, with a subset of approximately 10 customers having more extensive account details revealed. We are in the process of making appropriate disclosures to affected people.
Robinhood is an American financial services firm based in Menlo Park, California. It is best known for offering commission-free stock, ETF, and cryptocurrency trading via a mobile app launched in March 2015.
Private Data Belonging to Robinhood Sold Online
Following the Robinhood data breach disclosure, a cybercriminal known as pompompurin’ posted on a hacking forum that the stolen information is available for sale.
The threat actor declared that he was selling stolen data belonging to Robinhood customers for at least five figures, which is $10,000 or more.
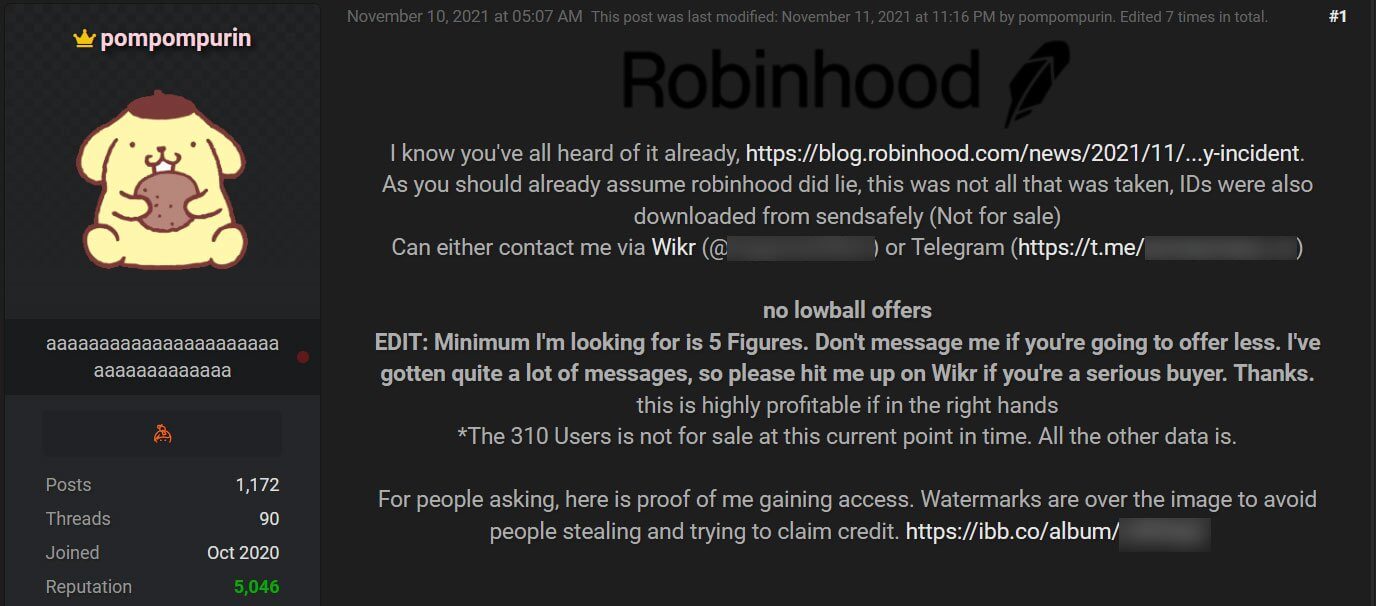
The company did not reveal the theft of ID cards at first, and the attacker declares to have downloaded them from SendSafely, a service designed to provide a more secure way to exchange confidential files.
As we disclosed on November 8, we experienced a data security incident and a subset of approximately 10 customers had more extensive personal information and account details revealed.
These more extensive account details included identification images for some of those 10 people. Like other financial services companies, we collect and retain identification images for some customers as part of our regulatory-required Know Your Customer checks.
According to BleepingComputer, the attacker managed to obtain access to the Robinhood customer support systems by deceiving a worker into installing remote access software on their workstation. When installed, the hacker is able to:
- keep track of the victim’s activities,
- take screenshots,
- remotely access the computer,
- use the employee’s saved login credentials to log in to internal Robinhood systems that they had access to.
I was able to see all account information on people. I saw a few people while the support agent did work.
In order to demonstrate that they carried out the attack, pompompurin shared screenshots of the cybercriminals gaining access to internal Robinhood systems.
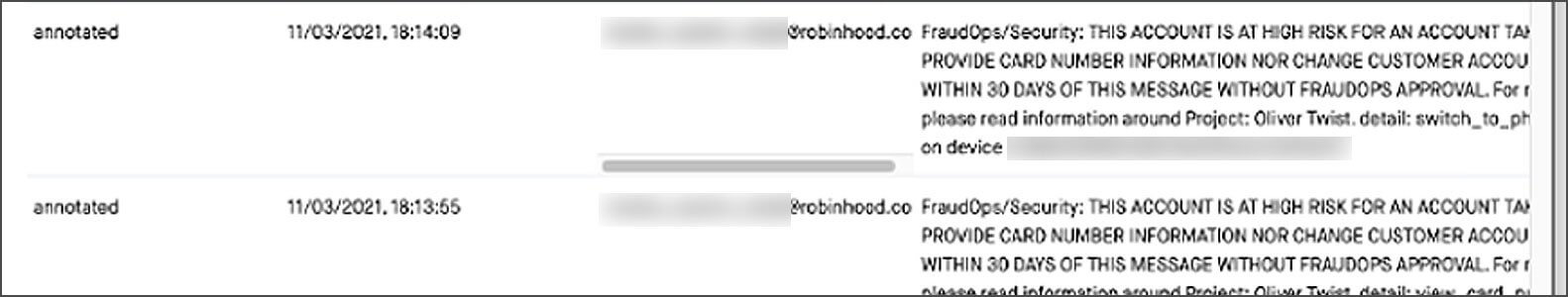
When contacted by BleepingComputer, Robinhood did not explicitly confirm the screenshots originated from their systems.
How Can Heimdal™ Help?
Heimdal™ Threat Prevention – Network provides unique threat hunting and ultimate visibility over an entire network, therefore offering A to Z protection, regardless of device or operating system.
If you liked this article follow us on LinkedIn, Twitter, YouTube, Facebook, and Instagram to keep up to date with everything cybersecurity.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










