Contents:
As my colleague Miriam reported, the REvil ransomware gang, also known as Sodinokibi, targeted MSPs with thousands of customers, through what appears to be a Kaseya ransomware attack.
Kaseya’s VSA product has unfortunately been the victim of a sophisticated cyberattack. Due to our teams’ fast response, we believe that this has been localized to a very small number of on-premises customers only.
Our security, support, R&D, communications, and customer teams continue to work around the clock in all geographies to resolve the issue and restore our customers to service.
Kaseya was in the process of validating a patch for the exploited vulnerability before rolling it out to its customers.
This seems to be a case of poor timing since the REvil ransomware gang beat Kaseya to the fix and managed to use the same zero-day to conduct the attack against managed service providers worldwide and their customers.
After this crisis, there will be the question of who is to blame. From our side, we would like to mention Kaseya has been very cooperative. Once Kaseya was aware of our reported vulnerabilities, we have been in constant contact and cooperation with them. When items in our report were unclear, they asked the right questions.
Also, partial patches were shared with us to validate their effectiveness. During the entire process, Kaseya has shown that they were willing to put in the maximum effort and initiative into this case both to get this issue fixed and their customers patched.
They showed a genuine commitment to do the right thing. Unfortunately, we were beaten by REvil in the final sprint, as they could exploit the vulnerabilities before customers could even patch.
The zero-day vulnerability exploited by REvil has been discovered by the DIVD researcher Wietse Boonstra and was assigned the CVE-2021-30116.
How Did REvil Manage to Exploit the Vulnerability?
It looks like REvil learned about the vulnerability as it was being fixed and used it as the CVE was quite simple to exploit.
The question is how REvil got their hands on it (or, perhaps more accurately, how the affiliate did). https://t.co/5kWkkqSTu3
— Brett Callow (@BrettCallow) July 4, 2021
The researcher Wietse Boonstra declared for the news publication BleepingComputer that the vulnerability disclosure was “within the industry-standard time for coordinated vulnerability disclosure,” and they would provide more information in a future advisory.
In an update, Kaseya is recommending that all VSA on-premise servers remain offline until a patch is released as Kaseya is also in the process of bringing their SaaS servers farms online and coming up with a plan for hosted VSA servers.
REvil Is Increasing Its Ransom Demands
We are witnessing an increase in the ransom demanded regarding the victims that got encrypted in the Kaseya ransomware attack.
Typically, the malicious actors from REvil are researching a victim by analyzing stolen and public data for financial information, cybersecurity insurance policies, and other information in order to come up with a high-ball ransom demand that the victim should be able to pay.
The novelty in this new situation is that REvil targeted the managed service providers and not their customers, therefore being unable to determine how much of a ransom they should demand from the encrypted MSP customers.
It looks like the ransomware gang has made a base ransom demand of $5 million for MSPs and a much smaller ransom of $44,999 for the MSP’s customers who were encrypted.
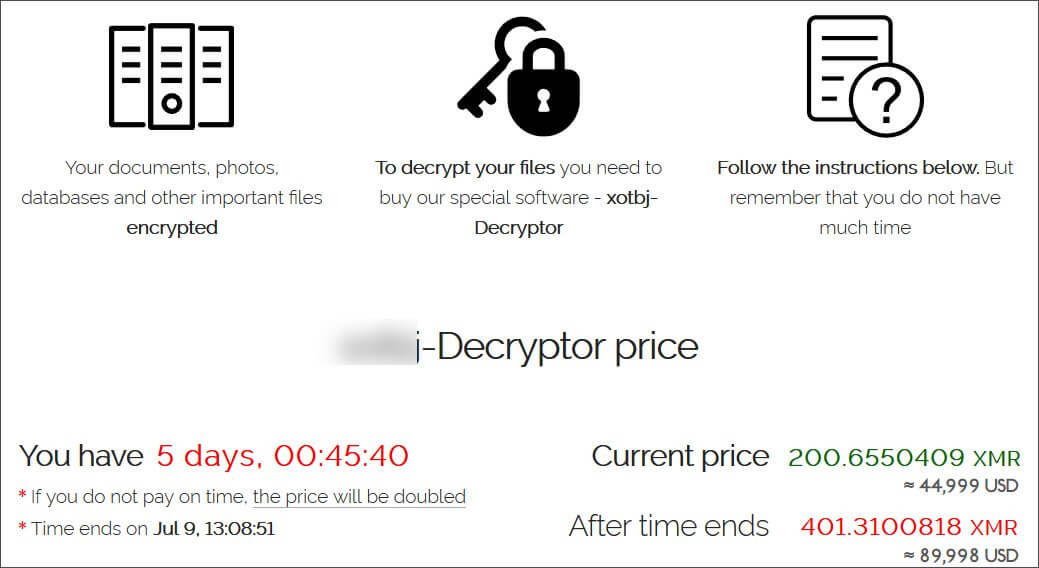
Usually, REvil can use multiple encrypted file extensions during the attack and then provide the victim with a decryptor able to release all extensions on the network after a ransom is paid, but for the Kaseya ransomware incident, the attackers are using a different M.O. as they are asking between $40,000 and $45,000 per individual encrypted file extension found on a victim’s network.
Fortunately, REvil representatives said to only had encrypted networks, and nothing more, therefore it looks like they did not steal any of the victims’ data.
A Change in REvil M.O.
The attackers seem to be also using a more holistic approach as they have set a fixed price for decrypting all the systems that got locked during the Kaseya ransomware attack.
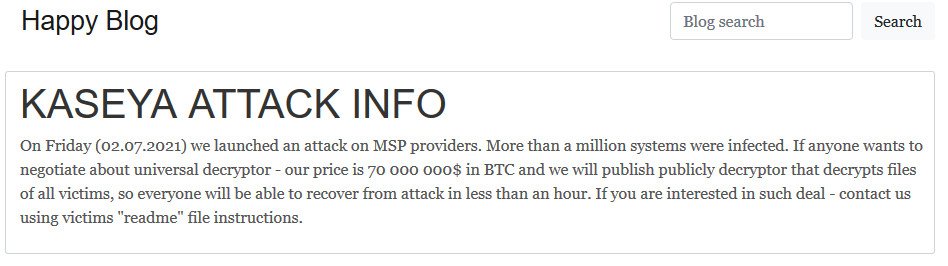
REvil decided that the price for decrypting all systems would be $70 million in Bitcoin in exchange for the tool that allows all affected businesses to recover their files.
It’s important to note that this is the highest ransom demand to date, the previous record also being held by REvil after the attack on the Taiwanese electronic and computer maker Acer.
Unfortunately, the full extent of this ransomware attack is unclear at the moment but it’s safe to say that the incident triggered some strong reactions from law enforcement, with the FBI announcing that they are working with CISA during their investigation.
President Biden also addressed the Kaseya supply-chain attack and directed intelligence agencies to investigate this large-scale attack that managed to affect hundreds of U.S. businesses.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








