Contents:
Checkmarx security researchers David Sopas, Paulo Silva, and Ricardo Gonçalves have recently discovered multiple API security flaws in the Coursera online learning platform, which caters to over 75 million learners, 100+ Fortune 500 companies, and more than 6,400 campuses, businesses, and governments.
Coursera collaborates with over 200 world-class universities and companies including Yale, the University of Michigan, the University of London, Google, IBM, and more.
As reported by ZD Net, the researchers decided to investigate the platform’s security posture due to the increased popularity of remote and on-demand learning prompted by the COVID-19 pandemic, in line with the organization’s Vulnerability Disclosure Program. The program specifically notes that access control issues are a major concern:
We [Coursera] consider security issues to be issues when you can perform:
Access data that you are otherwise not authorized to access normally as a learner (…)
Affects another learner outside of normal interactions on the platform (…)
Accessing Coursera’s internal administrative control systems.
Several API problems were found, including a user/account enumeration via the reset password feature, lack of resources limiting on both a GraphQL and REST API, and a GraphQL misconfiguration.
Nevertheless, the main issue of note was a Broken Object Level Authorization (BOLA) security flaw, considered by OWASP to be the most severe and most common API vulnerability today.
Broken Object Level Authorization happens when an application does not correctly confirm that the user performing the request has the required privileges to access a resource of another user. Almost every company has APIs that are vulnerable to BOLA.
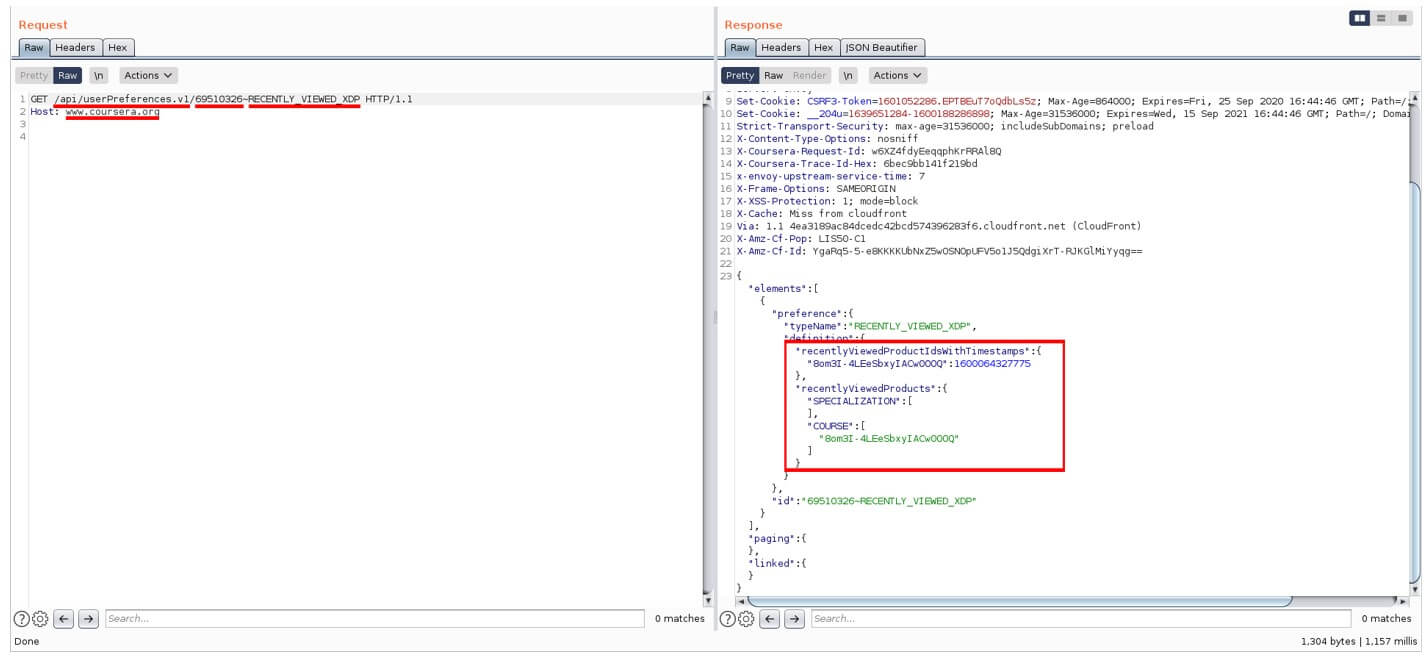
Anonymous request to retrieve arbitrary user recently viewed courses
Image Source: Checkmarx
The BOLA API vulnerability our team discovered affected the users’ preferences. Even anonymous users were not only able to retrieve their preferences, but also change them. Some of these preferences, such as recently viewed courses and certifications, also leaked some metadata (e.g. activity date/time).
This vulnerability could have been abused to understand general users’ courses preferences at a large scale, but also to somehow bias users’ choices, since manipulating their recent activity affected the content rendered on Coursera’s homepage for a specific user.
According to the researchers, unauthorized users’ data access is a critical issue and is, unfortunately, quite common with APIs. Authorization flaws directly impact data privacy, data integrity, user trust, and business reputation. “It is important to centralize access control validations in a single, well and continuously tested and actively maintained component”, the specialists added.
The vulnerabilities were reported to Coursera on October 5th, 2020, and the company acknowledged receiving the report on October 26th. By December 18th, a partial patch was issued, but a new issue required re-tests, delaying the confirmation of fixes until May 24th, 2021.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










