Contents:
In analyzing the threatscape, regardless of the chosen timeframe, the unequivocal conclusion we face is that the reactionary dynamic between defender and threat actor compels each other to transform, evolve, and, ultimately, face one another on a different type of battlefield. Defenders now have to oppose and repel increasingly complex malware, imbued with malicious code which is more viral, easy to produce (and reproduce), and capable of inflicting crippling damage all across the grid.
This clash between the defender and the attacker becomes increasingly visible when scrutinizing the public sector An assessment by UK Council’s study on the cyber threat status suggests that city councils all across the United Kingdom have witnessed a steep increase in cyber-attacks, with some regions, such as Sefton, combating up to 30,000 cyber-threats each month.
Based on the indicators, we are looking at a 50% YoY increase in attacks, the bulk of which abuse outdated, unsecured, or legacy software. Denmark is also facing its own cybersecurity crisis; although being deemed one of the most cyber-secure countries in the world, it’s still confronted with numerous challenges, some of which are not necessarily related to the public sector. Denmark’s Centre for Cybersecurity endeavored to create a taxonomy of all (cyber) threats that can potentially endanger the country. Among the threats that received the “Very High” were cyber-espionage and “well-organized” APTs acting from without and within the country to target and undermine various societal levels.
Taking into consideration the characteristics and nuances of how the threatscape has evolved in both geographical regions, Heimdal® has begun a private investigation to determine whether or not municipalities have gone up the hitlist or if this is conjectural or based on seasonality.
Investigative Methodology & Findings
Our investigation’s starting point revolved around the following claim – third-party software is, in general, much more prone to exploitation and, implicitly, more vulnerable compared to OS-centric software. However, in spite of severity and volume, our data (i.e., correlated with open-source threat intelligence) has revealed that vulnerabilities endemic to third-party applications have a less severe impact across all five security areas (i.e., confidentiality, integrity, availability, authenticity, and non-repudiation) compared to OS-associated vulnerabilities.
Operating under this assumption, Heimdal®’s SOC team has proceeded to probe the extracted data.
Insofar, Heimdal®’s investigation has uncovered the following facts – although there is significant percentile difference between identified Operating System-related vulnerabilities and those associated with Heimdal®-monitored third-party application, our data suggests that the OS flaws rated the 8 to 10 CVSS scale (i.e. High to Critical) have a more powerful impact on business operations (compared to 3rd-party app vulnerabilities), potentially jeopardizing continuity. Subsequently, we can surmise that OS vulnerabilities carry a higher computed risk score.
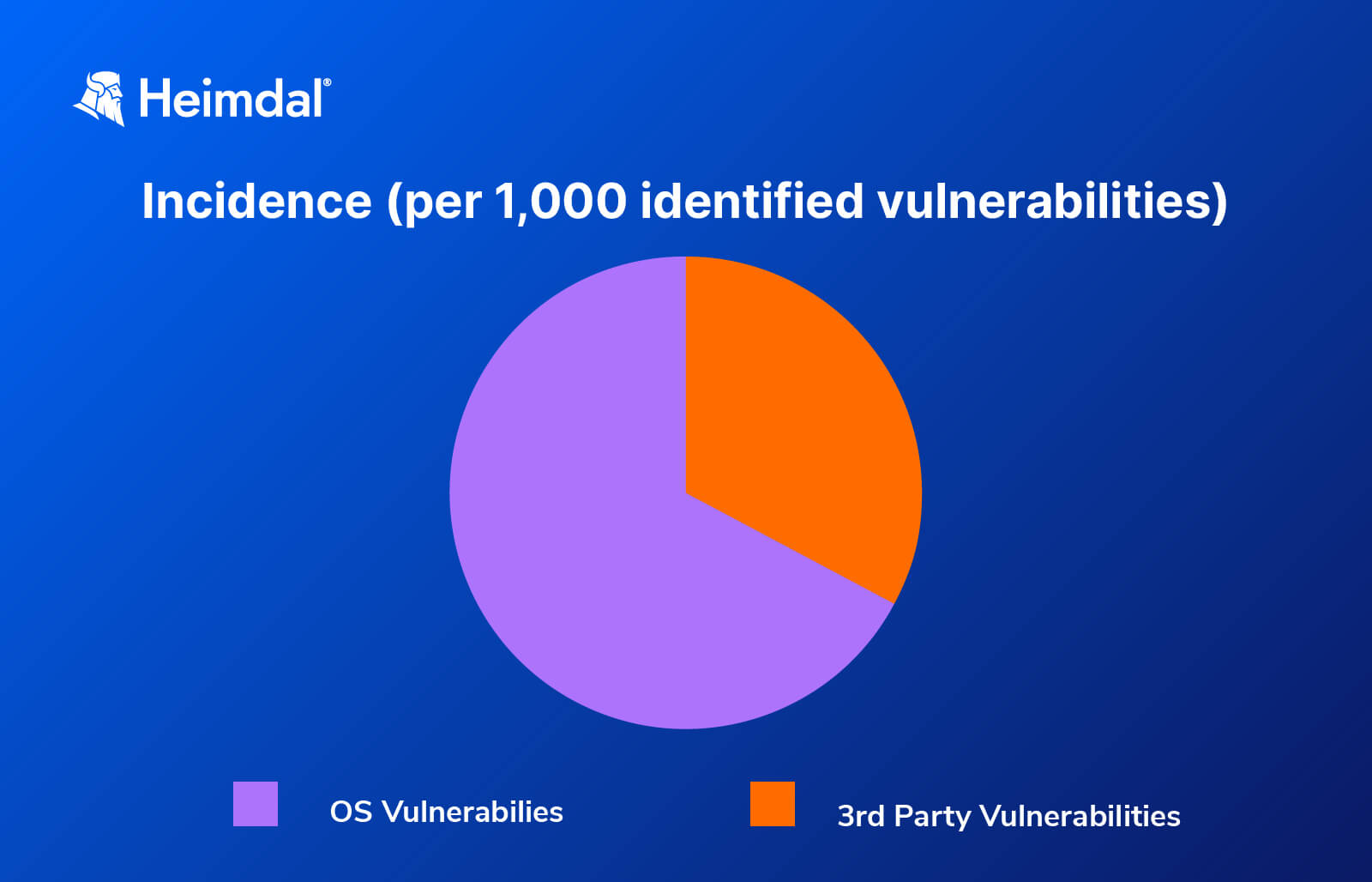
Furthermore, the same dataset has revealed that throughout the queried time-frame, the incidence rate for OS vulnerabilities is 670 per 1000 (i.e., for every 1,000 discovered vulnerabilities, 670 of them are Operating System related) and 329.35 per 100 for 3rd-party-related flaws (i.e., for every 1,000 discovered flaws, 329.35 of them are related to third-party applications). The results have been represented in the graph below.
We’ve also computed trend distribution of 3rd party and OS vulnerabilities based on CVSS scores. Our findings are enclosed in the graph below.
Risk assessment scores* (i.e., computed by factoring in attack vectors used for each vulnerability bracket, average detection time, average remediation time, costs vs benefits vs business impact) when comparing OS vulnerabilities to third-party vulnerabilities are as follows.
| CVSS score | Risk Score |
|---|---|
| 10 | 1.977843 |
| 9 – 9.8 | 0.133054 |
| 8 – 8.8 | 0.354871 |
| 7 – 7.8 | 1.400114 |
*Risk score metric ∈ [0,2] interval, where 0 signifies negligible impact across all business environment and 2 signifies critical impact, scoring associated with high infiltration potential, data breach, data loss and/or destruction.
Vulnerability Management
Another dimension we’ve inspected was CVSS distribution per unit (i.e. both OS-centric and 3rd party patches shall be considered statistical units.
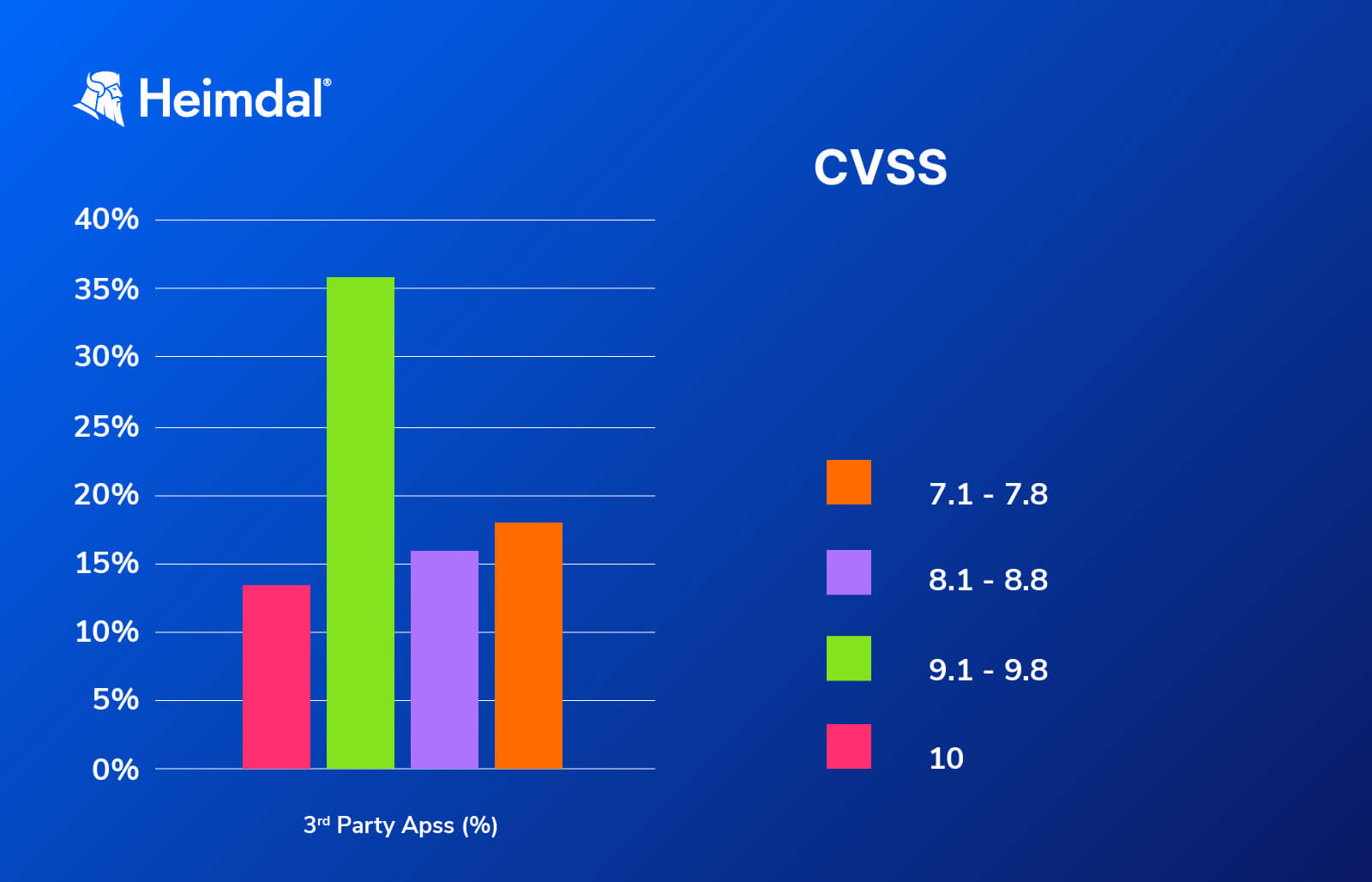
Our statistical analysis performed on the third-party patching workflow has revealed that a staggering 1.5% of all third-party vulnerabilities patched within the last 3 months carried a CVSS score between 7 (i.e., High) and 10 (i.e. Critical). All vulnerabilities were related to (third-party) drivers, definitions, and security updates. A drill-down of the high-scoring defects reveals the following facts.
- 5% of vulnerable 3rd party apps carried a CVSS 8.1 – 8.8 (i.e. High)
- 17% of vulnerable 3rd party apps carried a CVSS 7.1 – 7.8 (i.e. High)
- 50% of all detected third-party vulnerabilities were Critical (i.e. CVSS between 9.1 and 10).
The 3rd party vulnerability distribution can be reviewed in the graph below.
Technical Analysis of 3rd Party and OS Vulnerabilities
Heimdal®’s SOC team has performed a technical analysis on the identified vulnerabilities over the reference period, but also factoring in historical data. Our findings have been summarized below.
3rd Party Vulnerabilities
Our methodology involves extracting and analyzing data vulnerabilities with a CVSS score higher than 7 (i.e., High).
Vulnerabilities with a CVSS of 10
| Application Name | CVE | CVSS |
|---|---|---|
| Adobe Acrobat Reader (French) | CVE-2014-0566 | 10 |
| Adobe Acrobat Reader (Norsk) | CVE-2014-0566 | 10 |
| Adobe Acrobat Reader (Svenska) | CVE-2014-0566 | 10 |
| Adobe Acrobat Reader MUI | CVE-2018-4872 | 10 |
| Adobe Acrobat XI Pro (Update only) | CVE-2020-3742 | 10 |
| Adobe Flash Player ActiveX | CVE-2019-8069 | 10 |
| Adobe Flash Player NPAPI | CVE-2019-8069 | 10 |
| Adobe Flash Player PPAPI | CVE-2020-9633 | 10 |
| Adobe Reader | CVE-2016-1038 | 10 |
| Adobe Reader XI MUI | CVE-2016-1038 | 10 |
| Firefox | CVE-2021-38503 | 10 |
| Firefox DA x64 | CVE-2021-38503 | 10 |
| Firefox x64 | CVE-2021-38503 | 10 |
| Mozilla Firefox DA x64 | CVE-2021-38503 | 10 |
| Mozilla Firefox DA x86 | CVE-2018-18505 | 10 |
| Mozilla Firefox DE x86 | CVE-2021-38503 | 10 |
| Mozilla Firefox EN x86 | CVE-2018-18505 | 10 |
| Mozilla Firefox ES x64 | CVE-2020-12395 | 10 |
| Mozilla Firefox ES x86 | CVE-2021-38503 | 10 |
| Mozilla Firefox ESR x64 | CVE-2021-38503 | 10 |
| Mozilla Firefox ESR x86 | CVE-2018-18505 | 10 |
| Mozilla Firefox x64 | CVE-2021-38503 | 10 |
| Mozilla Firefox x86 | CVE-2021-38503 | 10 |
| Mozilla Thunderbird x86 | CVE-2018-18505 | 10 |
| Thunderbird | CVE-2021-38503 | 10 |
CVE-2014-0566 – Adobe Acrobat Reader (French, Norsk, and Svenska)
Classified as a denial of service, RCE (i.e., Remote Code Execution), overflow, and memory corruption vulnerability, CVE-2014-0566 would potentially allow threat actors to use an idiopathic attack vector in order to cause a denial of service (i.e., memory corruption) or execute arbitrary code on the victim’s machine. The vulnerability affects machines running Adobe Reader and Acrobat 10.x before 10.1.12 and 11.x before 11.0.09 on Windows and OS X.
Additional information (via CVE Details)
- Confidentiality Impact: Complete
- Integrity Impact: Complete
- Availability Impact: Complete
- Access Complexity: Low
- Authentication: Not required
- Gained Access: None
Adobe Acrobat Reader MUI – CVE-2018-4872
Classified as a security bypass vulnerability, CVE-2018-4872 could potentially allow an attacker to bypass safeguards (e.g. sandbox environments) via a defect pertaining to a cross call process. This vulnerability affects machines running Adobe Acrobat Reader 2018.009.20050 and earlier versions, 2017.011.30070 and earlier versions, 2015.006.30394 and earlier versions.
Additional information (via CVE Details)
- Confidentiality Impact: Complete
- Integrity Impact: Complete
- Availability Impact: Complete
- Access Complexity: Low
- Authentication: Not required
- Gained Access: None
Adobe Acrobat XI Pro (Update only) – CVE-2020-3742
Classified as a execute code vulnerability, CVE-2020-3742 allows an attacker to execute arbitrary code on the victim’s machine by leveraging a heap overflow bug. CVE-2020-3742 affects machines running Adobe Acrobat and Reader versions, 2019.021.20061 and earlier, 2017.011.30156 and earlier, 2017.011.30156 and earlier, and 2015.006.30508 and earlier.
Additional information (via CVE Details)
- Confidentiality Impact: Complete
- Integrity Impact: Complete
- Availability Impact: Complete
- Access Complexity: Low
- Authentication: Not required
- Gained Access: None
CVE-2019-8069 – Adobe Flash Player ActiveX & Adobe Flash Player NPAPI
Classified as code execution vulnerability, CVE-2019-8069 may be leveraged by a threat actor to run arbitrary code on the victim’s machine by exploiting a Same Origin Method Execution Vulnerability. Furthermore, the defect potentially allows the attacker to execute malicious code in the context of the current user. CVE-2019-8069 affects machines running Adobe Flash Player 32.0.0.238 and earlier versions, 32.0.0.207 and earlier.
Additional information (via CVE Details)
- Confidentiality Impact: Complete
- Integrity Impact: Complete
- Availability Impact: Complete
- Access Complexity: Low
- Authentication: Not required
- Gained Access: None
Adobe Flash Player PPAPI – CVE-2020-9633
A code execution vulnerability that allows an attacker to run arbitrary code on the victim’s machine. CVE-2020-9633 affects clients running Adobe Flash Player Desktop Runtime 32.0.0.371 and earlier, Adobe Flash Player for Google Chrome 32.0.0.371 and earlier, and Adobe Flash Player for Microsoft Edge and Internet Explorer 32.0.0.330 (i.e. usually abused with the use-after-free defect).
Additional information (via CVE Details)
- Confidentiality Impact: Complete
- Integrity Impact : Complete
- Availability Impact: Complete
- Access Complexity: Low
- Authentication: Not required
CVE-2016-1038 – Adobe Reader & Adobe Reader XI MUI
Classified as a restriction bypass vulnerability, CVE-2016-1038 allows a threat actor to circumvent restrictions associated with JavaScript API execution(s). This vulnerability affects Adobe Reader and Acrobat before 11.0.16, Acrobat and Acrobat Reader DC Classic before 15.006.30172, and Acrobat and Acrobat Reader DC Continuous before 15.016.20039 (i.e., Windows and Mac OSX).
Additional information (via CVE Details)
- Confidentiality Impact: Complete
- Integrity Impact : Complete
- Availability Impact: Complete
- Access Complexity: Low
- Authentication: Not required
- Gained Access: None
CVE-2021-38503 – Mozilla Firefox DE x86, Mozilla Firefox ES x86, Mozilla Firefox ESR x64, Mozilla Firefox x64, Mozilla Firefox x86, Thunderbird
Catalogued as restriction bypass vulnerability, CVE-2021-38503 allows the threat actor to circumvent restrictions (i.e., navigating top-level frames or script execution) by leveraging a subpar iframe sandbox ruling implement in the XSLT stylesheets.
Additional Information (via CVE Details)
- Confidentiality Impact: Partial
- Availability Impact: Partial
- Access Complexity: Low
- Authentication: Not required
- Gained Access: None
Prevalent vulnerabilities with a CVSS between 9.6 and 9.8
| Application Name | CVE | CVSS |
|---|---|---|
| Google Chrome x64 | CVE-2022-3890 | 9.6 |
| Google Chrome x86 | CVE-2022-3890 | 9.6 |
| Adobe Shockwave | CVE-2019-7104 | 9.8 |
| Chrome x64 | CVE-2022-2587 | 9.8 |
| Everything x64 | CVE-2016-10917 | 9.8 |
| Everything x86 | CVE-2016-10917 | 9.8 |
| Foxit PDF Reader | CVE-2020-26534 | 9.8 |
| Mozilla Thunderbird x64 | CVE-2022-46882 | 9.8 |
| Paint.Net x64 | CVE-2018-18446 | 9.8 |
| Paint.Net x86 | CVE-2018-18446 | 9.8 |
| Pidgin | CVE-2017-2640 | 9.8 |
| TeamViewer 10 | CVE-2018-16550 | 9.8 |
| TeamViewer 10 Host | CVE-2018-16550 | 9.8 |
| TeamViewer 11 | CVE-2018-16550 | 9.8 |
| TeamViewer 11 Host | CVE-2018-16550 | 9.8 |
| TeamViewer 12 | CVE-2018-16550 | 9.8 |
| TeamViewer 12 Host | CVE-2018-16550 | 9.8 |
| TeamViewer 13 | CVE-2018-16550 | 9.8 |
| VLC x64 | CVE-2019-12874 | 9.8 |
| VLC x86 | CVE-2019-12874 | 9.8 |
| WinSCP | CVE-2020-28864 | 9.8 |
CVE-2016-10917 – Everything x86 & Everything x64
Classified as an SQL injection vulnerability, CVE-2016-10917 affects the Everything WordPress plugin, potentially allowing a threat actor to read, write or commit any changes to the SQL database.
Additional information (via Mitre)
- Confidentiality: Read Application Data
- Access Control: Bypass Protection Mechanism
- Access Control: Bypass Protection Mechanism
- Integrity: Modify Application Data
CVE-2017-2640 – Pidgin
Classified as a code execution vulnerability, CVE-2017-2640 would potentially allow a threat actor to execute arbitrary code in Pidgin or trigger a Denial of Service by leveraging an out-of-bounds write flaw for XML content.
CVE-2018-16550 – TeamViewer 10 Host,TeamViewer 11, TeamViewer 12, TeamViewer 13, TeamViewer 12 Host, TeamViewer 11 Host, TeamViewer 10
A vulnerable TeamViewer component allows the threat actor to circumvent the app’s brute-force authentication safeguard. With cancelling the final auth step, the threat actor could extract the user’s 4-digit PIN.
Additional information (via Mitre)
Integrity & Availability: Modify Memory; DoS: Crash, Exit, or Restart; Execute Unauthorized Code or Commands
CVE-2018-18446 – Paint.Net x64 & Paint.Net x86
Catalogued as a deserialization vulnerability, CVE-2018-18446 allows the threat actor to validate untrusted data.
Additional Information (via Mitre)
- Integrity: Modify Application Data; Unexpected State
- Availability DoS: Resource Consumption (CPU)
CVE-2019-12874 – VLC x86 & VLC x64
An explotaitable flaw in the zlib_decompress_extra (i.e.m modules/demux/mkv/util.cpp in VLC media player 3.x through 3.0.7 leading to a double-free vulnerability.
Additional information (via MITRE)
Integrity & Confidentiality & Availability: Modify Memory; Execute Unauthorized Code or Commands
Prevalent Vulnerabilities with a CVSS between 7.1 and 8.8
| Application Name | CVE | CVSS |
|---|---|---|
| Zoom Outlook Plugin | CVE-2022-36928 | 7.1 |
| Adobe Acrobat Reader 2020 MUI | CVE-2020-9723 | 7.5 |
| Calibre x64 | CVE-2021-44686 | 7.5 |
| Calibre x86 | CVE-2021-44686 | 7.5 |
| TortoiseSVN x64 | CVE-2021-21698 | 7.5 |
| TortoiseSVN x86 | CVE-2021-21698 | 7.5 |
| Wireshark x32 | CVE-2022-3725 | 7.5 |
| Wireshark x64 | CVE-2022-3725 | 7.5 |
| 7-zip x64 | CVE-2022-29072 | 7.8 |
| 7-zip x86 | CVE-2022-29072 | 7.8 |
| Adobe Acrobat PRO 2017 | CVE-2020-24429 | 7.8 |
| Adobe Acrobat Reader | CVE-2022-38450 | 7.8 |
| Adobe Acrobat Reader - Dansk | CVE-2022-35665 | 7.8 |
| Adobe Acrobat Reader 2017 | CVE-2020-24429 | 7.8 |
| Adobe Acrobat Reader DC | CVE-2022-38450 | 7.8 |
| Adobe Acrobat Reader DC DA | CVE-2022-38450 | 7.8 |
| Adobe Acrobat Reader DC MUI | CVE-2022-38450 | 7.8 |
| Adobe Acrobat Reader DC SE | CVE-2022-35665 | 7.8 |
| Audacity | CVE-2017-1000010 | 7.8 |
| Gimp | CVE-2021-45463 | 7.8 |
| IrfanView x64 | CVE-2019-16887 | 7.8 |
| IrfanView x86 | CVE-2019-13242 | 7.8 |
| Lenovo System Update | CVE-2019-6175 | 7.8 |
| Mozilla Firefox SE x64 | CVE-2022-45415 | 7.8 |
| TeamViewer 15 | CVE-2021-34858 | 7.8 |
| TeamViewer 15 Host | CVE-2021-34858 | 7.8 |
| VNC Server | CVE-2022-41975 | 7.8 |
| WinRar x64 | CVE-2018-20250 | 7.8 |
| WinRar x86 | CVE-2018-20250 | 7.8 |
| PuTTY x64 | CVE-2021-36367 | 8.1 |
| PuTTY x86 | CVE-2021-36367 | 8.1 |
| Docker Desktop | CVE-2019-5736 | 8.6 |
| Git x64 | CVE-2022-36882 | 8.8 |
| Git x86 | CVE-2022-36882 | 8.8 |
| iTunes x64 | CVE-2020-9947 | 8.8 |
| iTunes x86 | CVE-2020-9947 | 8.8 |
| Libre Office | CVE-2021-25631 | 8.8 |
| Mozilla Firefox DE x64 | CVE-2021-43537 | 8.8 |
| Mozilla Firefox EN x64 | CVE-2021-30547 | 8.8 |
| Oracle VM VirtualBox | CVE-2022-39427 | 8.8 |
| TeamViewer 13 Host | CVE-2020-13699 | 8.8 |
| TeamViewer 14 | CVE-2020-13699 | 8.8 |
| TeamViewer 14 Host | CVE-2020-13699 | 8.8 |
| TeamViewer 15 x86 | CVE-2020-13699 | 8.8 |
CVE-2022-29072 – 7-zip x64 & 7-zip x86
A misconfiguration in 7zip’s DLLs can potentially be leveraged by a threat actor to achieve privilege escalation and/or execute arbitrary code on the victim’s machine. The vulnerability occurs each time a file with the .7z extension is dragged to the app’s Contents area, under the Help menu.
Additional information (via MITRE)
Integrity & Availability: Modify Memory; DoS: Crash, Exit, or Restart; Execute Unauthorized Code or Commands.
CVE-2021-44686 – Calibre x64 & Calibre x86
A faulty regular expression bug in Calibre allows the attacker to trigger a Regular Expression Denial of Service.
Additional information (via MITRE)
- Availability: DoS: Crash, Exit, or Restart; DoS: Resource Consumption (CPU); DoS: Resource Consumption (Memory); DoS: Resource Consumption (Other)
- Access Control: Protection Mechanism; Other
CVE-2019-6175 – Lenovo System Update
A Denial of Service (i.e., DoS) vulnerability allows the attacker to write configuration files in non-standard places.
CVE-2021-25631 – Libre Office
Classified as an Incomplete lists of disallowed inputs vulnerability, CVE-2021-25631 can potentially allow the threat actor to bypass Libra Office’s denylist via link manipulation.
Additional information (via MITRE)
Access Control: Bypass Protection Mechanism
CVE-2022-3725 – Wireshark x32 & Wireshark x64
A defect in Wireshark’s OPUS protocol dissector can permit an attacker to stage a Denial of Service attack on the victim’s machine via crafted files and/or packet injection.
Additional information (via MITRE)
Integrity &Availability: Modify Memory; DoS: Crash, Exit, or Restart; Execute Unauthorized Code or Commands
OS Vulnerabilities
Our methodology involves extracting and analyzing data vulnerabilities with a CVSS score higher than 7.
Vulnerabilities with a CVSS of 10
CVE-2013-1330 – MAC disabled vulnerability in Microsoft SharePoint and Microsoft Exchange Server. For additional information, click on the enclosed link. A threat actor can potentially leverage the unassigned Mac disabled vulnerability in order to execute arbitrary code on the victim’s machine.
Prevalent vulnerabilities with a CVSS between 9 and 9.8
| CVE | CVSS |
|---|---|
| CVE-2008-5416 | 9 |
| CVE-2014-0251 | 9 |
| CVE-2014-0251 | 9 |
| CVE-2022-38045 | 9.1 |
| CVE-2006-1311 | 9.3 |
| CVE-2007-0099 | 9.3 |
| CVE-2007-0216 | 9.3 |
| CVE-2007-0940 | 9.3 |
| CVE-2007-1747 | 9.3 |
| CVE-2007-1756 | 9.3 |
| CVE-2007-2223 | 9.3 |
| CVE-2008-0120 | 9.3 |
| CVE-2008-1091 | 9.3 |
| CVE-2008-3704 | 9.3 |
| CVE-2009-0102 | 9.3 |
| CVE-2009-0220 | 9.3 |
| CVE-2009-0562 | 9.3 |
| CVE-2009-0901 | 9.3 |
| CVE-2009-2500 | 9.3 |
| CVE-2009-2506 | 9.3 |
| CVE-2009-3127 | 9.3 |
| CVE-2010-0266 | 9.3 |
| CVE-2010-0814 | 9.3 |
| CVE-2010-0815 | 9.3 |
| CVE-2010-2569 | 9.3 |
| CVE-2010-2738 | 9.3 |
| CVE-2010-2747 | 9.3 |
| CVE-2010-3190 | 9.3 |
| CVE-2011-0655 | 9.3 |
| CVE-2011-1269 | 9.3 |
| CVE-2011-1980 | 9.3 |
| CVE-2011-1986 | 9.3 |
| CVE-2011-3402 | 9.3 |
| CVE-2011-3417 | 9.3 |
| CVE-2012-0002 | 9.3 |
| CVE-2012-0177 | 9.3 |
| CVE-2012-2550 | 9.3 |
| CVE-2013-0006 | 9.3 |
| CVE-2013-1302 | 9.3 |
| CVE-2013-1315 | 9.3 |
| CVE-2013-3155 | 9.3 |
| CVE-2014-0325 | 9.3 |
| CVE-2014-1757 | 9.3 |
| CVE-2014-1759 | 9.3 |
| CVE-2014-6364 | 9.3 |
| CVE-2015-0085 | 9.3 |
| CVE-2015-1671 | 9.3 |
| CVE-2015-2503 | 9.3 |
| CVE-2020-1208 | 9.3 |
| CVE-2020-1449 | 9.3 |
| CVE-2022-22012 | |
| CVE-2022-41080 | 9.8 |
| CVE-2023-21689 | 9.8 |
| CVE-2023-21708 | 9.8 |
| CVE-2023-21803 | 9.8 |
| CVE-2023-23397 | 9.8 |
| CVE-2021-28476 | 9.9 |
Prevalent vulnerabilities with a CVSS between 8 and 8.8
| CVE | CVSS |
|---|---|
| CVE-2022-21980 | 8 |
| CVE-2015-1763 | 8.5 |
| CVE-2016-7249 | 8.8 |
| CVE-2017-0283 | 8.8 |
| CVE-2018-0804 | 8.8 |
| CVE-2018-0852 | 8.8 |
| CVE-2018-8311 | 8.8 |
| CVE-2018-8501 | 8.8 |
| CVE-2019-0585 | 8.8 |
| CVE-2019-0888 | 8.8 |
| CVE-2019-1068 | 8.8 |
| CVE-2020-0760 | 8.8 |
| CVE-2021-1636 | 8.8 |
| CVE-2021-1707 | 8.8 |
| CVE-2021-28455 | 8.8 |
| CVE-2022-35777 | 8.8 |
| CVE-2022-41036 | 8.8 |
| CVE-2022-41062 | 8.8 |
| CVE-2022-41089 | 8.8 |
| CVE-2022-41128 | 8.8 |
| CVE-2023-21705 | 8.8 |
Prevalent Vulnerabilities with a CVSS between 7 and 7.8
| CVE | CVSS |
|---|---|
| CVE-2012-0178 | 7.2 |
| CVE-2022-33631 | 7.3 |
| CVE-2022-33631 | 7.3 |
| CVE-2022-33631 | 7.3 |
| CVE-2022-33631 | 7.3 |
| CVE-2016-3378 | 7.4 |
| CVE-2017-8516 | 7.5 |
| CVE-2017-8516 | 7.5 |
| CVE-2022-23267 | 7.5 |
| CVE-2022-29143 | 7.5 |
| CVE-2022-38013 | 7.5 |
| CVE-2023-21538 | 7.5 |
| CVE-2006-6133 | 7.6 |
| CVE-2013-0005 | 7.8 |
| CVE-2016-0021 | 7.8 |
| CVE-2016-3235 | 7.8 |
| CVE-2016-3313 | 7.8 |
| CVE-2017-8725 | 7.8 |
| CVE-2017-8742 | 7.8 |
| CVE-2018-0748 | 7.8 |
| CVE-2018-1027 | 7.8 |
| CVE-2018-1029 | 7.8 |
| CVE-2018-8172 | 7.8 |
| CVE-2020-1582 | 7.8 |
| CVE-2020-16856 | 7.8 |
| CVE-2020-17019 | 7.8 |
| CVE-2021-26857 | 7.8 |
| CVE-2021-27056 | 7.8 |
| CVE-2021-27056 | 7.8 |
| CVE-2021-28449 | 7.8 |
| CVE-2021-28452 | 7.8 |
| CVE-2021-28453 | 7.8 |
| CVE-2021-31941 | 7.8 |
| CVE-2021-31949 | 7.8 |
| CVE-2021-40486 | 7.8 |
| CVE-2022-26929 | 7.8 |
| CVE-2022-35820 | 7.8 |
| CVE-2022-38010 | 7.8 |
| CVE-2022-38048 | 7.8 |
| CVE-2022-41032 | 7.8 |
| CVE-2022-41061 | 7.8 |
| CVE-2023-21808 | 7.8 |
Results
- 4% of OS vulnerabilities had a CVSS of 10.
- 26% of OS vulnerabilities had a CVSS between 9 and 9.9.
- 32% of OS vulnerabilities had a CVSS rating between 7.2 and 8.8.
How can Heimdal® Help?
Organizations tend to rely on manual patching in order to deploy all relevant improvement-carrying packages. However, things tend to change a bit when you’re in the shoes of an IT admin catering to the needs of hundreds of users. The best way around this issue is, of course, automated patching.
If configured correctly, an automatic patching solution can ensure timely (and correct) deployment and a low risk of incompatibility. Heimdal®’s Patch & Asset Management can aid you in quickly distributing your patches, regardless if they are OS-specific, 3rd party, proprietary, or UX/UI-oriented.
Conclusion
To surmise, Heimdal®’s investigation into patching workflows, behaviors, and distribution has discovered the following facts:
- 5% of vulnerable 3rd party apps carried a CVSS 8.1 – 8.8 (i.e. High)
- 17% of vulnerable 3rd party apps carried a CVSS 7.1 – 7.8 (i.e. High)
- 50% of all detected third-party vulnerabilities were Critical (i.e. CVSS between 9.1 and 10).
- 4% of OS vulnerabilities had a CVSS of 10.
- 26% of OS vulnerabilities had a CVSS between 9 and 9.9.
- 32% of OS vulnerabilities had a CVSS rating between 7.2 and 8.8.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security