Contents:
RisePro, a new information-stealing malware, was recently observed on a dark web forum run by Russian cybercriminals. Since December 13, the virus has been offered for sale as a log credential stealer on underground forums, leading many to believe it is a clone of the Vidar Stealer.
RisePro’s appearance on the Russian market is evidence of the stealer’s growing popularity within the threat community, according to researchers at Flashpoint.
The security experts outlined a few key takeaways:
Samples that Flashpoint analysts identified indicate that RisePro may have been dropped or downloaded by the pay-per-install malware downloader service ‘PrivateLoader’ in the past year.
The appearance of the stealer as a payload for a pay-per-install service may indicate a threat actor’s confidence in the stealer’s abilities.
RisePro appears to be a clone of the stealer malware ‘Vidar’.
RisePro, a New Version of Vidar Stealer
Many of the new RisePro’s characteristics are comparable to those of Vidar Stealer. Researchers have highlighted one specific feature they have in common: they both use the same dynamic link library (DLL) dependencies, according to a Cyware alert.
“At the time of writing, Russian Market has featured over 2,000 logs allegedly sourced from RisePro”, noted the researchers.
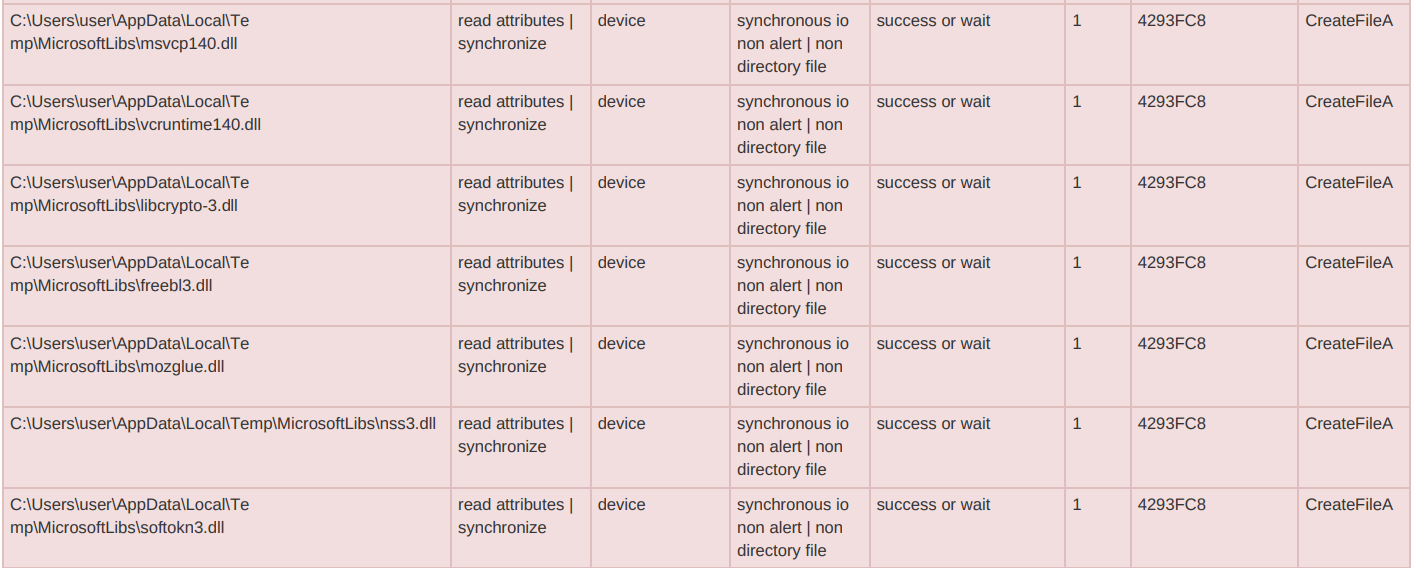
Indicators Of Compromise (IOCs)
The identified hash samples of RisePro are the following:
- E0579dc3a1e48845194d9cd9415ae492d375fd59cea0e1adf21866afde152f89
- C633d7549fb4a77e02fa1e48f8fb3e3b41d8a998778d2e2c024949673dad0ba5
- d9445561cef089271565e3fe54b8da7aff3ecfe73506762ffcdaedc3615180ba
- 8259fed869da390d33cbdb7e2e174ce58a8ebd7f1f99f104b70753eb8679b246
- 867254ba74add6d8e7484dbdd6d45a4c12acd9e31870d84d9efe202945191286
- 5ee280016fc53c27bbc6d049820cb6dfd33bc4e9e5c618027677793f070eefee
Command and control (C2) domains:
- neo-files[.]com
- gamefilescript[.]com
RisePro command and control URI structure:
- /set_file.php
- /get_loaders.php
- /freezeStats.php
- /get_grabbers.php
- /get_marks.php
- /get_settings.php
- /pingmap.php
There has been an increase of Vidar clones, which experts attribute to the malware having been fully cracked and examined. Therefore, it is essential for companies to stay aware of the IoCs linked to RisePro and to take all measures to safeguard their data and other digital assets.
The complete report published by researchers at Flashpoint is available here.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










