Contents:
ALPHV BlackCat is a RaaS, therefore the ALPHV BlackCat operators recruit affiliates to perform corporate breaches and encrypt devices. ALPHV ransomware executable is written in Rust, a programming language that, while not often used by malware creators, is gaining popularity because of its high efficiency and memory safety.
Ransomware-as-a-Service is an illicit ‘parent-affiliate(s)’ business infrastructure, in which operators (i.e., malicious software owner and/or developer) provision tools to affiliates (i.e., customers) for the purpose of carrying out ransomware attacks.
What Happened?
The ALPHV ransomware gang, also known as BlackCat has created a dedicated website that allows the customers and employees of their victims to check if their data was stolen in an attack.
As you might know, when ransomware gangs carry out attacks, they steal confidential business information, and once the threat actor has collected everything of value, they will begin to encrypt the devices.
After being stolen, the information is then used in double-extortion schemes, in which the hackers demand a ransom payment in order to give a decryptor and prevent the public release of company data.
Ransomware gangs will construct data leak sites on which they will gradually expose pieces of the stolen material or will contact customers and workers telling them that their information was stolen in order to put pressure on victims into paying the ransom.
ALPHV/BlackCat ransomware operation started distributing data that they claim was obtained from a hotel and spa in Oregon. As part of this assault, the ransomware group claimed to have stolen 112 gigabytes of data, some of which included employee information for 1,500 workers, such as their Social Security Numbers.
However, the ransomware group went one step farther than just releasing the data on their typical Tor data leak site. Instead, they developed a unique website that allows staff and customers of the hotel to check to see whether their data was taken during the assault on the hotel.
Through the use of this website, workers, customers, or anybody else for that matter may see information on hotel visitors and their stays as well as the personal data of 1,534 staff.
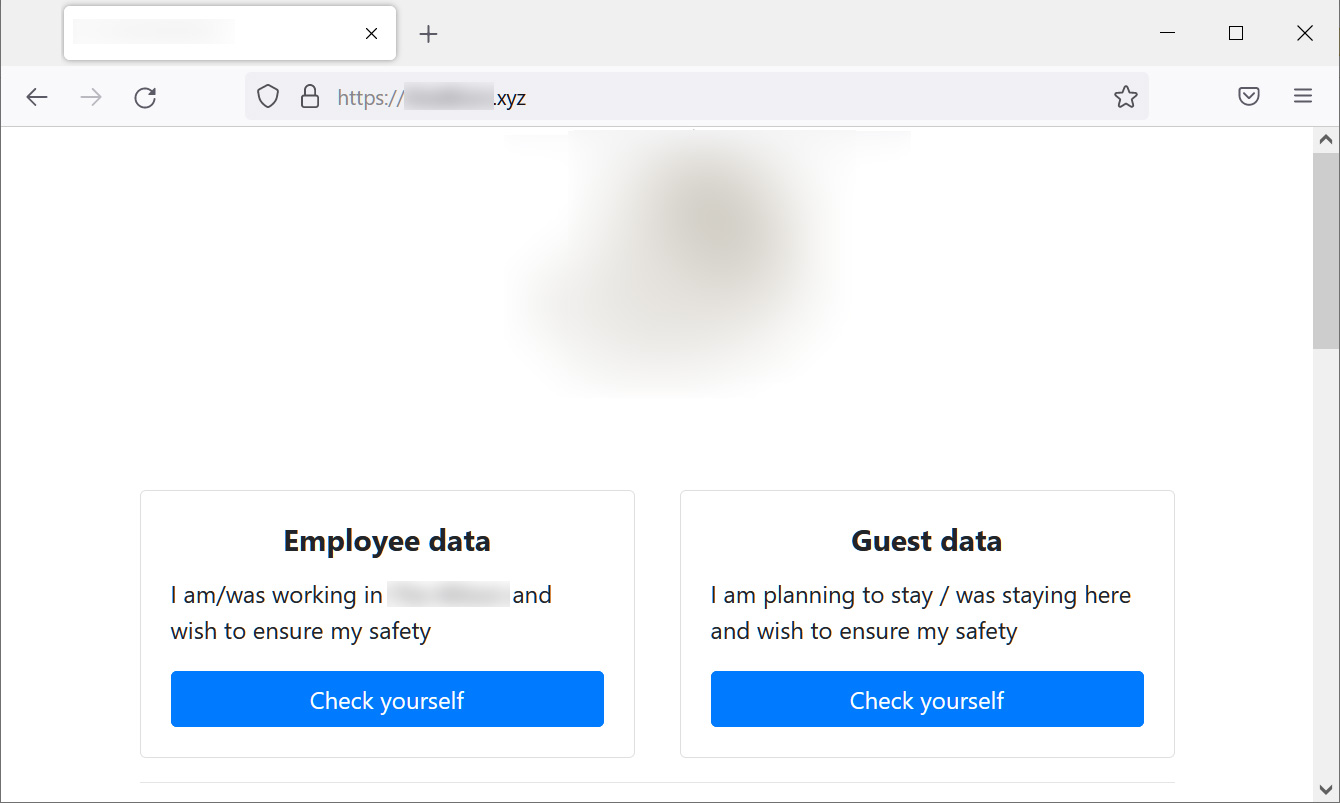
As BleepingComputer reports, the employee data comprises very sensitive information, such as names, Social Security Numbers, dates of birth, phone numbers, and email addresses, but the consumer visitor data just contains names, arrival dates, and stay fees.
Because this website is located on the open web, often known as the public internet, search engines are able to index it. This means that the disclosed information is likely to be included to search results, which might make the situation even more precarious for those affected.
If Ransomware Is a Concern for You
Join us on Tuesday, June 21st, 1pm BST/2pm CEST for our next webinar, when Cyber-Security & Heimdal Product Expert Andrei Hinodache and Pre-Sales Engineering Manager Robertino Matausch will explain why ransomware is on the rise, and how should executives evaluate their company’s ability to prevent and recover from ransomware attacks.
What’s more, we will be showing you how to do this LIVE! Our experts will walk you through ransomware incident preparedness, technical testing through live simulations, detection, and suggestions for thwarting attackers by hardening systems and infrastructure.
Make sure you register here!
Did you enjoy this article? Follow us on LinkedIn, Twitter, Facebook, Youtube, or Instagram to keep up to date with everything we post!


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










