Contents:
The Python Package Index (PyPI), a repository of software for the Python programming language that helps you find and install software developed and shared by the Python community is now getting deluged with spam packages.
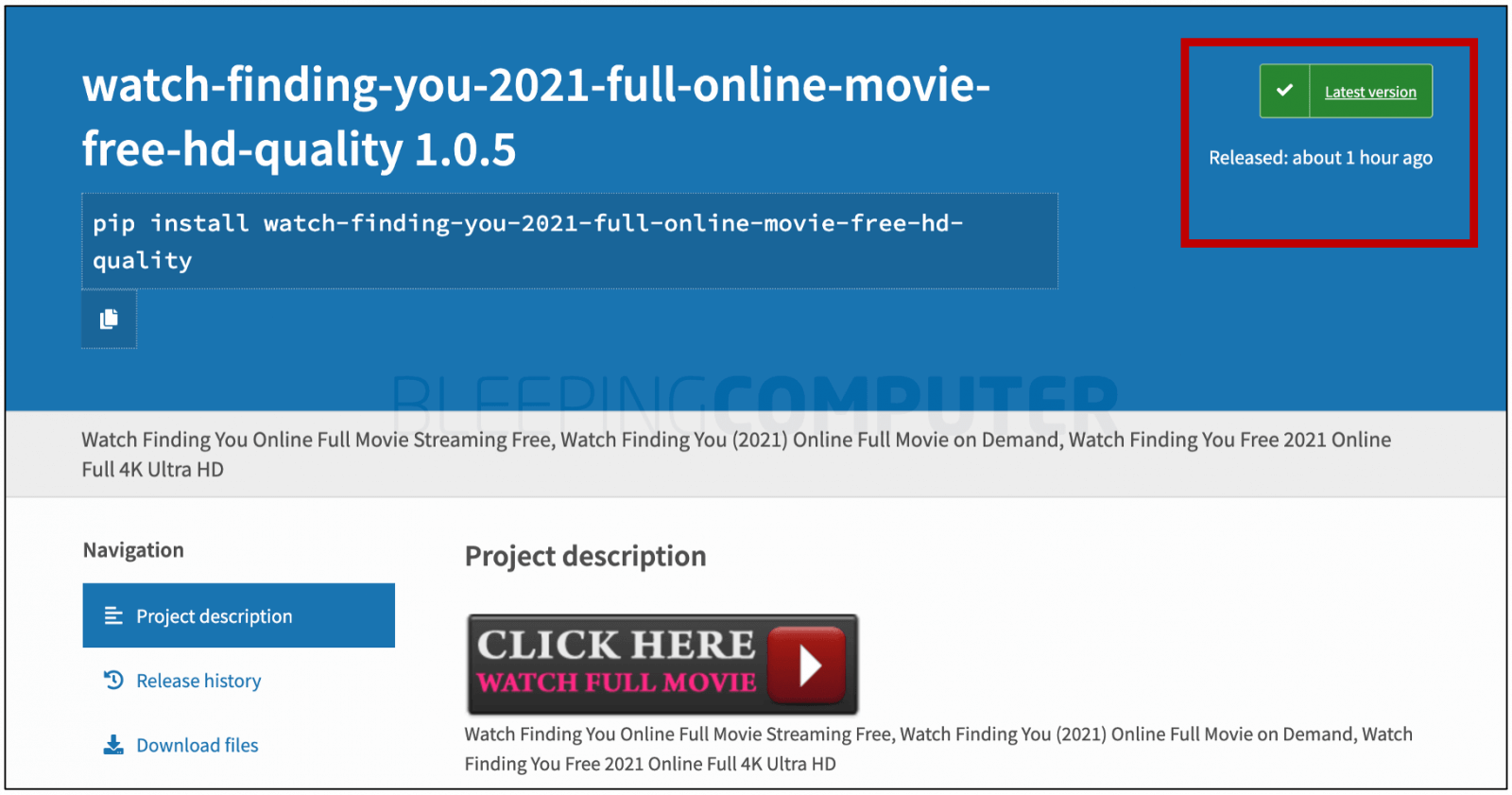
The fact that the names of the packages are similar to various popular films reminds us of torrents and pirated content that is distributed via the Internet: watch-(movie-name)-2021-full-online-movie-free-hd-…
Every single package is published by a distinctive fictitious maintainer account, making it difficult for the Python Package Index to get rid of the packages and the spam accounts at the same time.
Adam Boesch, senior software engineer at Sonatype detected it while he was auditing a dataset and distinguished a PyPI component named after a popular TV sitcom that sounded bizarre.
I was looking through the dataset and noticed ‘wandavision‘ which is a bit strange for a package name.
Looking closer I found that package and looked it up on PyPI because I didn’t believe it.
According to BleepingComputer, spammers keep adding newer packages to PyPI even if some of these packages are a few weeks old.
The search result count of “10,000+” could be inaccurate, as they noticed the real number of spam packages being displayed on PyPI repository was much less.
Below is one example of the many packages posted yesterday:
According to ZDNet, in February, fake “Discord”, “Google”, and “Roblox” flooded PyPI in a huge spam attack. Ewa Jodlowska, Executive Director of the Python Software Foundation had told the technology news website that the PyPI admins were working on addressing the spam assault, but because of the pypi.org characteristics, anyone could post to the repository, and such incidents were usual.
These packages include not only links to quasi-video streaming sites and spam keywords but also files with working code and author information restricted from valid PyPI packages.
Bleeping Computer noticed that the spam package “watch-army-of-the-dead-2021-full-online-movie-free-hd-quality,” contained author information and some code from the legitimate PyPI package, “jedi-language-server.”
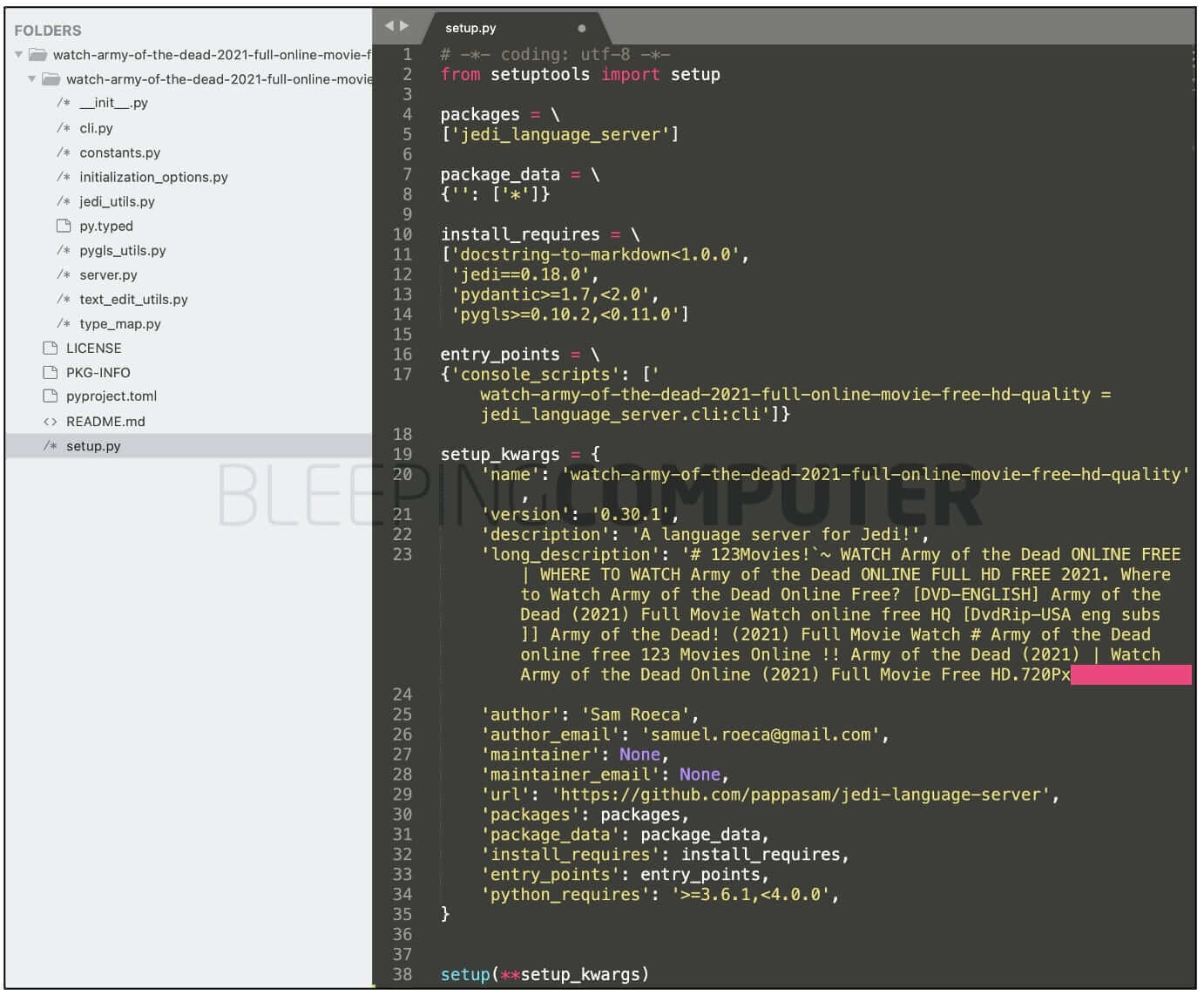
In order to stop these packages from being easily noticed, malicious hackers have combined code from valid packages with fake or malicious packages to hide their traces.
Adam Boesch said:
It’s not uncommon in other ecosystems like npm, where you have millions of packages. Packages like these luckily are fairly easy to spot and avoid.”
Always a good idea to investigate a package before using it. If something seems off, there’s a reason for that.
Lately, attacks on open-source ecosystems like npm, RubyGems, and PyPI have rapidly increased. We saw cybercriminals flooding with malware, malicious copycats, or just vigilante packages to spread their message.
Protecting these repositories has become similar to a game where players use a mallet to hit toy moles that appear at random back into their holes between cybercriminals and repository maintainers.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








