Contents:
Brands use push notifications on browsers, websites, and apps as a form of marketing. While push notifications per se are not a bad idea (when used sparingly), I think we can all agree that they tend to overdo it.
If you could confidently click on a link a few years ago, open a page, and read or watch what you came there to see, nowadays you can’t. First, you need to click to accept cookies or a GDPR agreement, then click a few more times for closing all the other pop-ups and ads which stream forth.
Usually, this is enough to get rid of them. Just go through the 5-6 clicks routine, and the view clears up. But lately, push notifications emerged and started being more and more widely used. These notifications are delivered to users through apps installed on their mobile devices, making them harder to get rid of once they start pouring through.
Even more troubling, push notifications are not just annoying and intrusive when unrequested. They can also carry dangerous malware. The purpose of malware hidden in push notifications is either to deliver a flood of more ads (malvertising, such as the recent SundownEK campaign) or to actually help hackers break into your accounts and steal your money, data, or identity.
Additionally, push notification data has become a growing concern as law enforcement agencies increasingly seek access to this information from major tech companies.
Serious Concerns about Malware and Privacy Risks in Push Notifications
As recently as last month, a new strain of Android Trojan malware was putting serious pressure on mobile phone users by delivering malvertising campaigns. The malware, dubbed Android.FakeApp.174, was delivered by multiple fake apps imitating legit apps. Those were taken down from the Google App Store once the malware was discovered, but the infection already spread by then.
The push notifications that just kept coming and coming were so aggressive that they eventually took over users’ phones. So much of the system’s resources were used for displaying these ads, that no bandwidth remained for using the device for its intended purposes. Additionally, notification data can be misused by malicious actors to track and apprehend criminal suspects, illustrating the potential misuse of such information as a powerful surveillance tool. This is particularly concerning for users of various messaging apps, where sensitive communications can be intercepted.
This type of advertising deluge is typical for malvertising campaigns. This refers to the type of malware that keeps pushing advertising onto users, regardless of the fact that users will not be persuaded by the ads since they are so annoying. The purpose is not for you to be convinced by the ads, but for the hackers to exploit a pay-per-view advertising program. They earn money just by having their ads displayed, and they created the malvertising hack just to cheat the system and make more money with their unstoppable spam. If they can also steal some data while they’re at it, all the better.
In the case of the Android.FakeApp.174 malware I mentioned above, the purpose of the campaign was not to just flood users with malvertising, but also to direct them towards scam websites. This way, some users even fell for scams and entered sensitive info on phishing forms which were mimicking legit email and banking service sites. Entering sensitive data on such forms poses significant risks, as it can be exposed to unauthorized parties. This raises significant privacy concerns, especially with the increasing interoperability among services like WhatsApp and other messaging apps.
Classic PCs were also targeted by similar campaigns in the past. A notorious malware was redirecting users when browsing to the Push-notification.tools site (link sanitized for your safety). This is what the Push-notification virus redirect looked like:
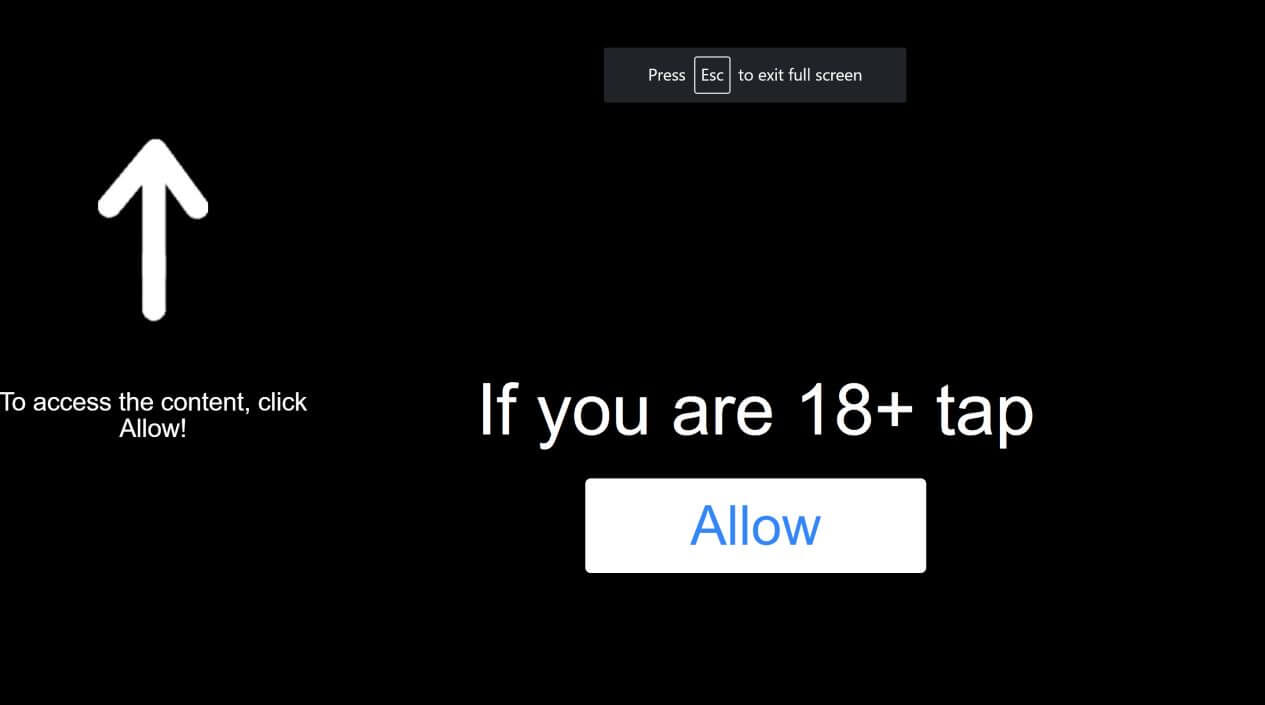
Basically, the malware was blocking all the content you wanted to browse with this pop-up asking you to click ‘Allow’. If you succumbed to it, you were giving the malware a free pass to deliver all kinds of spam to your desktop, even when the browser was closed.
Usually, this type of malware first enters your computer when you download ‘free’ software (pirated or cracked) from torrents and other sources of pirated content. You’ll get a malware ‘bonus’ especially in packages containing multiple pieces of software. One more reason to stay away from illegitimate content.
How to Review Push Notifications in Browsers and Remove Them
Are you getting suspicious push notifications and you’re unsure of whether they are malware or not? Or, even if you’re sure they’re not malware, you’d like to take back the permissions and you don’t know how?
Don’t worry, removing legit push notifications is very easy. You can also configure settings to allow or block sites from sending notifications. Malicious push notifications, on the other hand, are more complicated to get rid of.
For Google Chrome, just go to Settings / content / notifications, or directly copy-paste this link into the browser address: chrome://settings/content/notifications?search=notifications
This will reveal the list of websites you allowed to send you push notifications, as well as the list of websites you blocked push notifications from. If you see one you don’t remember approving or wish to take back permission from, just click the vertical dots bar for that domain and select ‘Remove’.
For Mozilla Firefox, the process is almost identical. Go to Settings / content / notifications and you can see all the websites you allowed such pop-ups from. You can also select a No Notifications default option in Mozilla, if you want.
For Safari / Opera / other browsers, you can also easily find the path to reviewing push notifications in your browser settings. Just look around or drop me a question if you can’t find it.
What about Ad Blockers?
Some users opt for ad blockers in an attempt to simplify their digital life. They just install a browser extension and stop seeing ads, for good. This is legit and safe, so if that’s what you want to do, go ahead and install the Ad Block Plus extension, for example.
However, in my opinion, this is not the way to go. First of all, push notifications can be useful, when you’re actually getting those you are interested in. You just need to review permissions from your browser and restrict the list to stuff you really want to find out about.
Second of all, adblockers are also not displaying any on-page ads, some of which can have value for you as well. I know that some ads can be annoying, especially when persistent. But some can also remind you of some item you’ve seen and postponed buying etc. Personally, I do enjoy ads sometimes for their reminder value, or for helping me discover new things I might be interested in. Still, this is a matter of preference so it’s entirely up to you.
How to Get Rid of Malicious Push Notifications on a Mobile Device
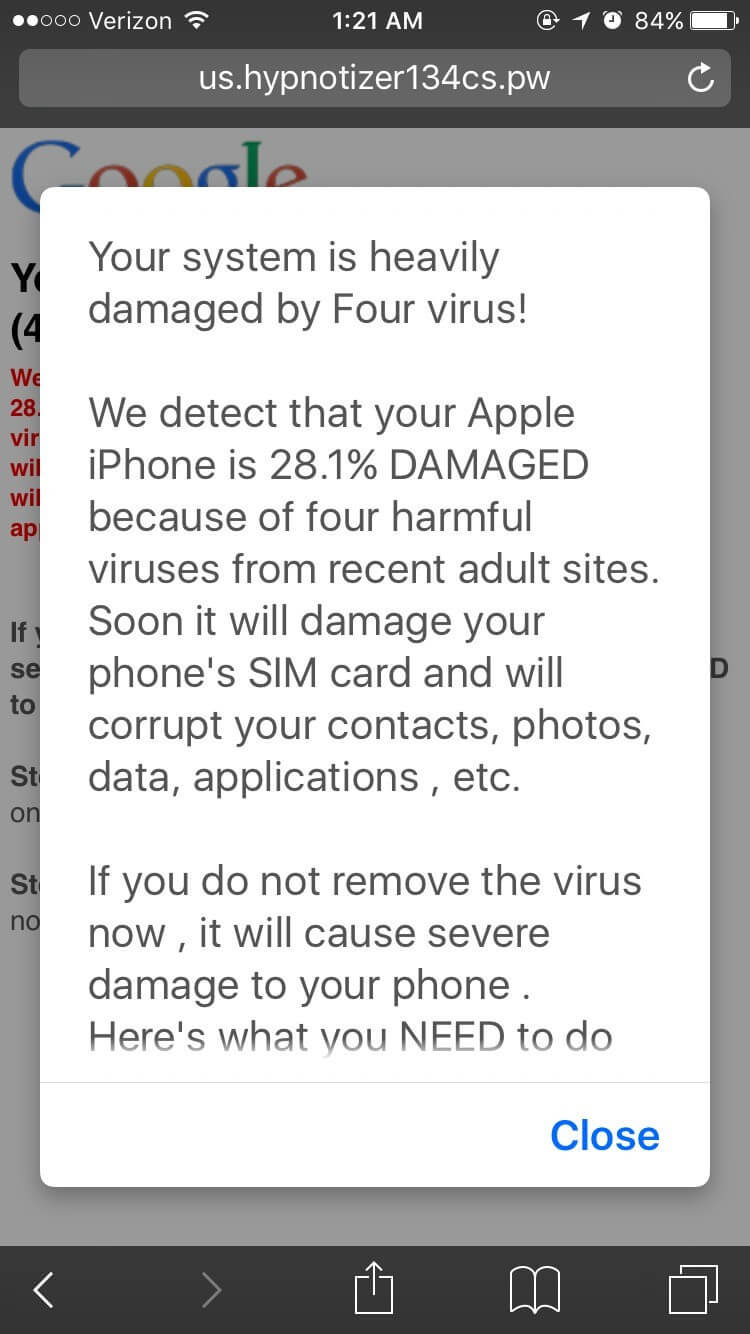
A typical malicious pop-up meant to scare you into downloading yet more malware.
Here are the typical signs that the ads (push notifications) you are getting are malicious (caused by a malware infection):
- Ads appear even in places where they shouldn’t (like your desktop, even when the browser is closed)
- The browser home page changes without your permission
- The websites you used to visit without issues are now not displaying properly, or you get redirected to another address
- You get pop-ups which are advertising fake software or updates, or warnings that you are infected, followed by prompts to install a specific clean-up tool (DON’T!)
- You see apps and programs installed on your device (with shortcuts and everything) that you don’t remember installing
If you experience any from this list above, there’s a high chance that you were infected with malicious push notifications. It is crucial to secure the user’s device to prevent such infections.
Unfortunately, there isn’t a quick one-size-fits-all fix, since there are different types of malware out there. Your best bet is to check your browser’s list of allowed push notifications and disable everything that doesn’t look familiar. All of them, if need be.
Then, scan your PC and clean it up with professional anti-malware software. Ensure that client requests are validated to guarantee that only authorized parties can send notifications.
If you’d like to try our complete cybersecurity suite for home use (containing both reactive and proactive layers of security), here’s a month on the house:

Final Advice
To prevent infections with malicious push notifications and to keep your browsing experience as clean as possible, it’s best to be cautious.
Keep the list of websites from which you accept push notifications short. A few of your favorites are enough; if you’re interested to see updates from the other portals, you can always enter them at your own pace, right? (Of course, I hope that if you enjoy this blog and our content, you will accept push notifications from us.) 🙂 Be aware of the privacy risks associated with push notifications, as mishandling user data can lead to security vulnerabilities.
Also, don’t venture online unprotected. Keep your devices secured with a reputable cybersecurity product so you don’t get infected even if you do come across an infected link or file. Tech companies play a significant role in storing user data, and this poses potential risks for privacy, especially concerning sensitive investigations and user surveillance.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








