Contents:
A group of Italian cybersecurity researchers has put together a set of three attacks known as ‘Printjack,’ alerting people of the serious risks of trusting their printer too much.
According to BleepingComputer, the attacks include recruiting the printers in DDoS swarms, imposing a paper DoS state, and executing privacy breaches.
According to experts, modern printers are still exposed to rudimentary weaknesses and fail to keep up with other IoT and digital devices that began complying with cybersecurity and data confidentiality regulations.
Following an evaluation of the attack, the experts discovered non-compliance with GDPR requirements and the ISO/IEC 27005:2018 (framework for managing cyber-risks).
This absence of built-in protection is especially concerning given the widespread use of printers in critical environments, businesses, and companies of all sorts.
The Operation
In ‘You Overtrust Your Printer’, a paper written by Giampaolo Bella and Pietro Biondi is explained how the search engine Shodan was used to search for devices with a publicly accessible TCP port 9100, usually used for raw TCP/IP printing jobs. The devices were located in European countries.
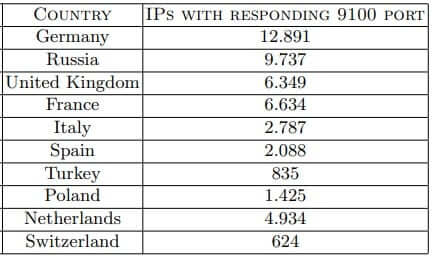
Following the scan, tens of thousands of IPs reacted to the port inquiry, with the most vulnerable devices being in Germany, Russia, France, the Netherlands, and the United Kingdom.
While port 9100 can be used for a variety of tasks other than printing, it is the default port for that service, hence the majority of these responses are probably related to printing.
The First Attack
According to BleepingComputer, the first type of Printjack attack is to recruit the printer in a DDoS swarm, and hackers are able to do this by using a known RCE weakness with a publicly available PoC.
The experts use CVE-2014-3741 as an example, but they point out that the MITRE database has at least a few dozen other issues.
Given that there are 50,000 vulnerable machines in the top 10 EU countries alone, recruiting them for DDoS attacks isn’t out of the question.
Printers that have been impacted are more likely to be unresponsive, consume more energy, and generate more heat, while their electronics will experience accelerated deterioration.
The Second Attack
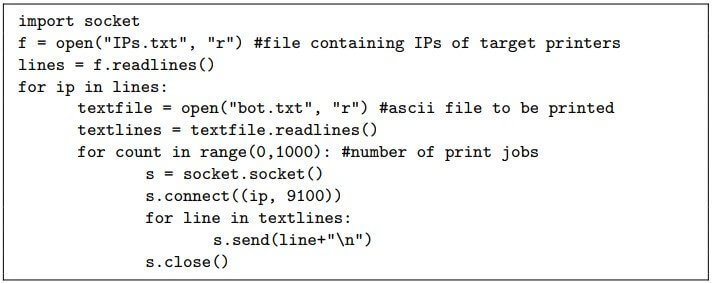
The second attack is a ‘paper DoS attack,’ which is carried out by sending multiple print jobs until the target’s trays have no more paper left. In this scenario, the organization might experience serious disruption.
According to researchers, this form of attack is easy to perform by developing a basic Python script that runs inside the victim system and creates a thousand-times-repeating printing job loop.
The Third Attack
In the most severe type of Printjack attacks, there’s the possibility of a “man in the middle” cyberattack and monitoring the printed documents.
Since no printing information is encrypted, a malicious actor could potentially retrieve data in plaintext format if they abused a weakness in the printer’s network.
Printers Need More Attention
The lack of adequate security measures on printers has been brought up several times in recent years, particularly after printers became internet-connected.
Printer vendors must improve the security and data handling operations of their devices on both hardware and software levels.
Furthermore, users and companies are advised to avoid treating printers as a minor component of their daily computing, erroneously presuming that these devices pose no significant danger to them or their data.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










