Contents:
A new ransomware called “Prestige”, is targeting Ukrainian and Polish transportation and logistics organizations. The first cyber incident involving Prestige Ransomware was on October 11th, in attacks detected within an hour of each other.
Attackers were observed distributing the ransomware payloads across the corporate networks of their targets, a strategy that was incredibly uncommon in operations against Ukrainian enterprises.
Microsoft Threat Intelligente Center (MSTIC) experts found that Prestige Ransomware shares victimology with another recent Russian state-aligned malware, specifically on affected geographies and countries, and it overlaps with previous victims of the FoxBlade malware, also known as HermeticWiper.
At the moment of writing this article, the Prestige ransomware attacks are yet to be linked to a specific threat actor. Redmond is working on notifying all customers who have been compromised and had their systems encrypted with this ransomware.
Ransomware Deployment Methods
The hackers are using multiple methods to deploy the ransomware payload across the victims’ networks. MSTIC highlights in its report the following methods so far:
- Method 1: The ransomware payload is copied to the ADMIN$ share of a remote system, and Impacket is used to remotely create a Windows Scheduled Task on target systems to execute the payload
- Method 2: The ransomware payload is copied to the ADMIN$ share of a remote system, and Impacket remotely invokes an encoded PowerShell command to target the systems and execute the payload
- Method 3: The ransomware payload is copied to an Active Directory Domain Controller and deployed to systems using the Default Domain Group Policy Object
Once the deployment of the ransomware is successful, Prestige payloads will drop ransom notes named “README.txt” in the root directory of the encrypted drives.
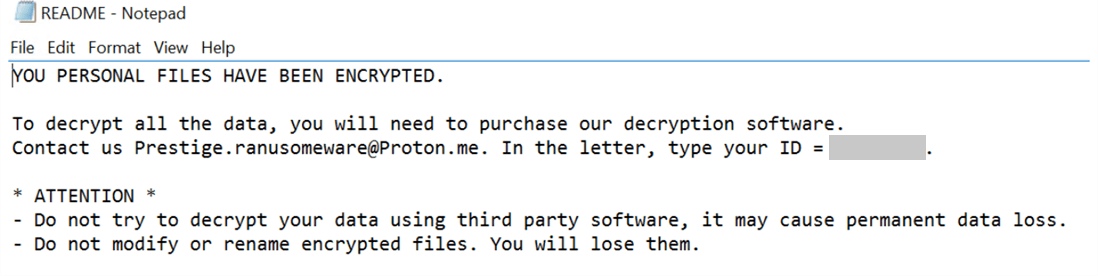
Prestige ransom note (Source)
According to BleepingComputer, the ransomware encrypts files based on extensions matching a list predefined by the threat actor, and adds the .enc extension at the end of the files after encryption. Prestige makes use of the CryptoPP C++ library to AES-encrypt each matching file found on the compromised systems. To hinder recovery efforts, the ransomware will delete the backup catalogue and shadow copies available.
To help defenders detect and mitigate Prestige ransomware attacks, Microsoft shared a list of indicators of compromise (IOCs) and advanced hunting queries.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










