Contents:
Phishing scams have become more complex over time, and scammers are finding new ways to obtain information about their victims.
This new phishing campaign is no different. The crook hides text in the Facebook posts to trick potential victims into giving up their account credentials and personally identifiable information.
A malicious email impersonating Facebook’s copyright infringement policy is targeting recipients and threatening to delete their accounts if they don’t respond.
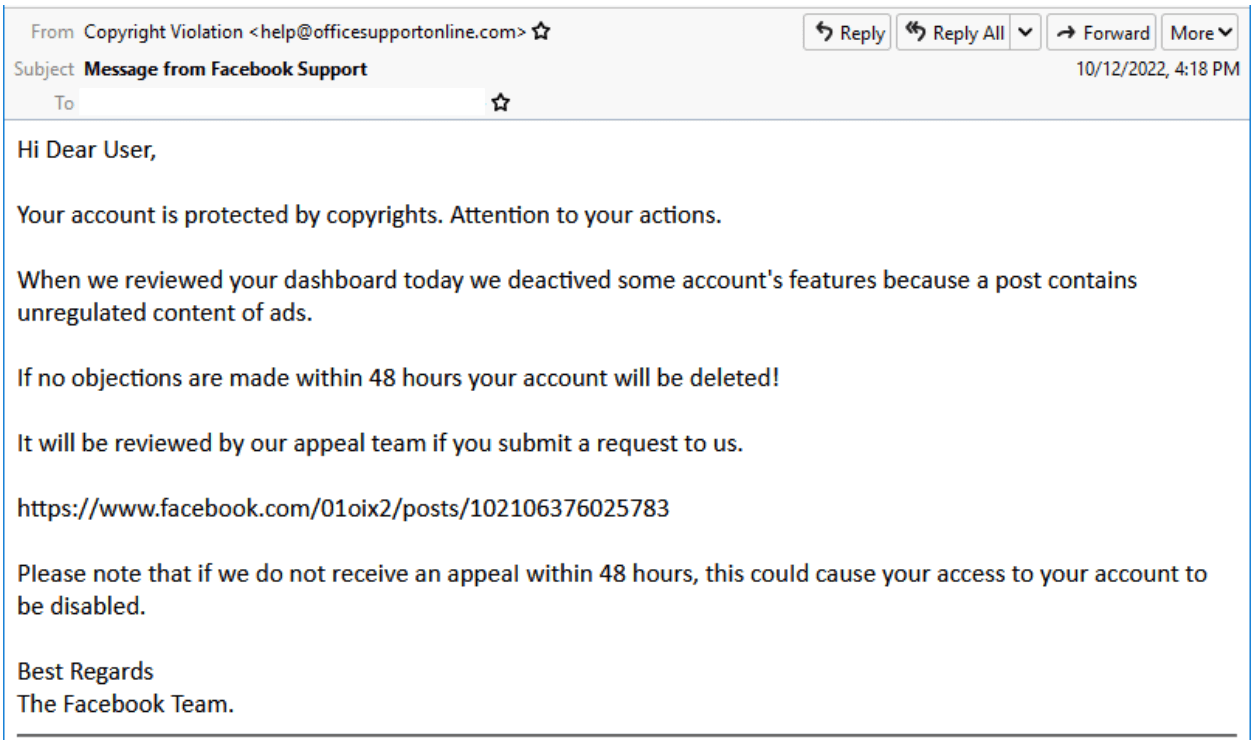
The link mentioned to appeal an account deletion is actually on Facebook. It will help threat actors bypass email security solutions and ensure their phishing messages land in the target’s inbox.
This Facebook post pretends to be “Page Support,” using a Facebook logo to appear as if the company manages it.
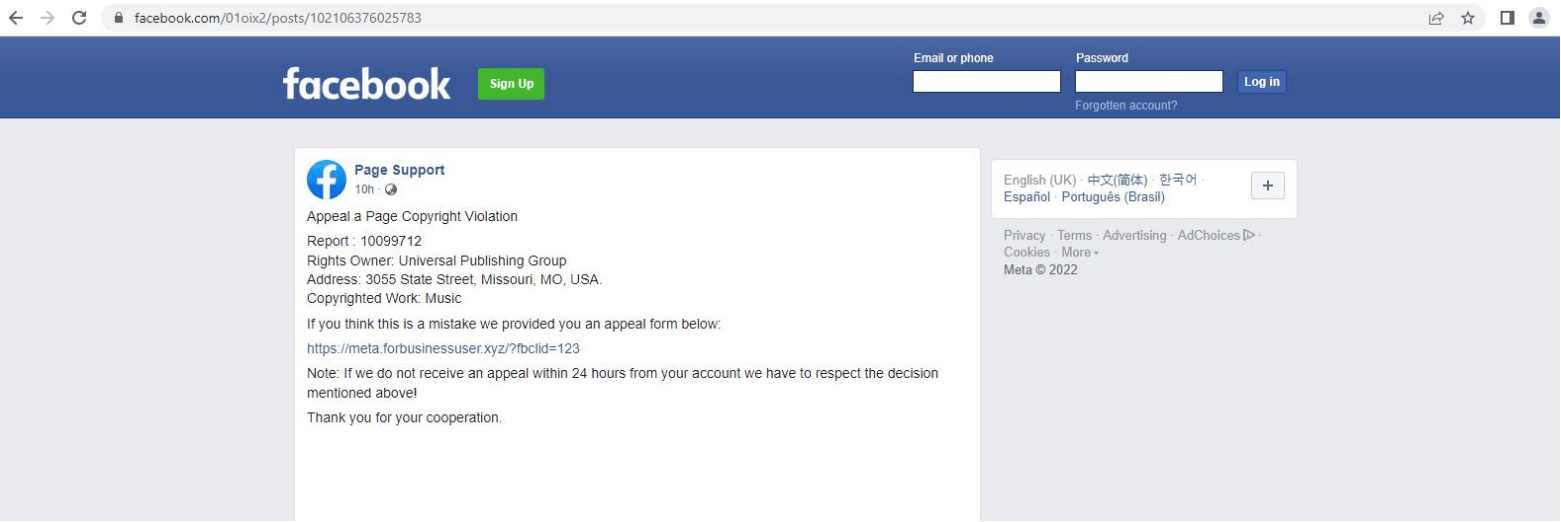
However, this post contains a link to a phishing website that closely resembles the company personally owned by Facebook’s founder. This slight change helps prevent inexperienced users from becoming victims of the scam.
The fake websites created by the phishing campaign had URLs such as the following:
- meta[.]forbusinessuser[.]xyz/?fbclid=123
- meta[.]forbusinessuser[.]xyz/main[.]php
- meta[.]forbusinessuser[.]xyz/checkpoint[.]php
These sites are crafted with care to make them appear legitimate. They contain a form where victims are requested to enter personal data such as their full name, email address, and phone number to file a copyright appeal.
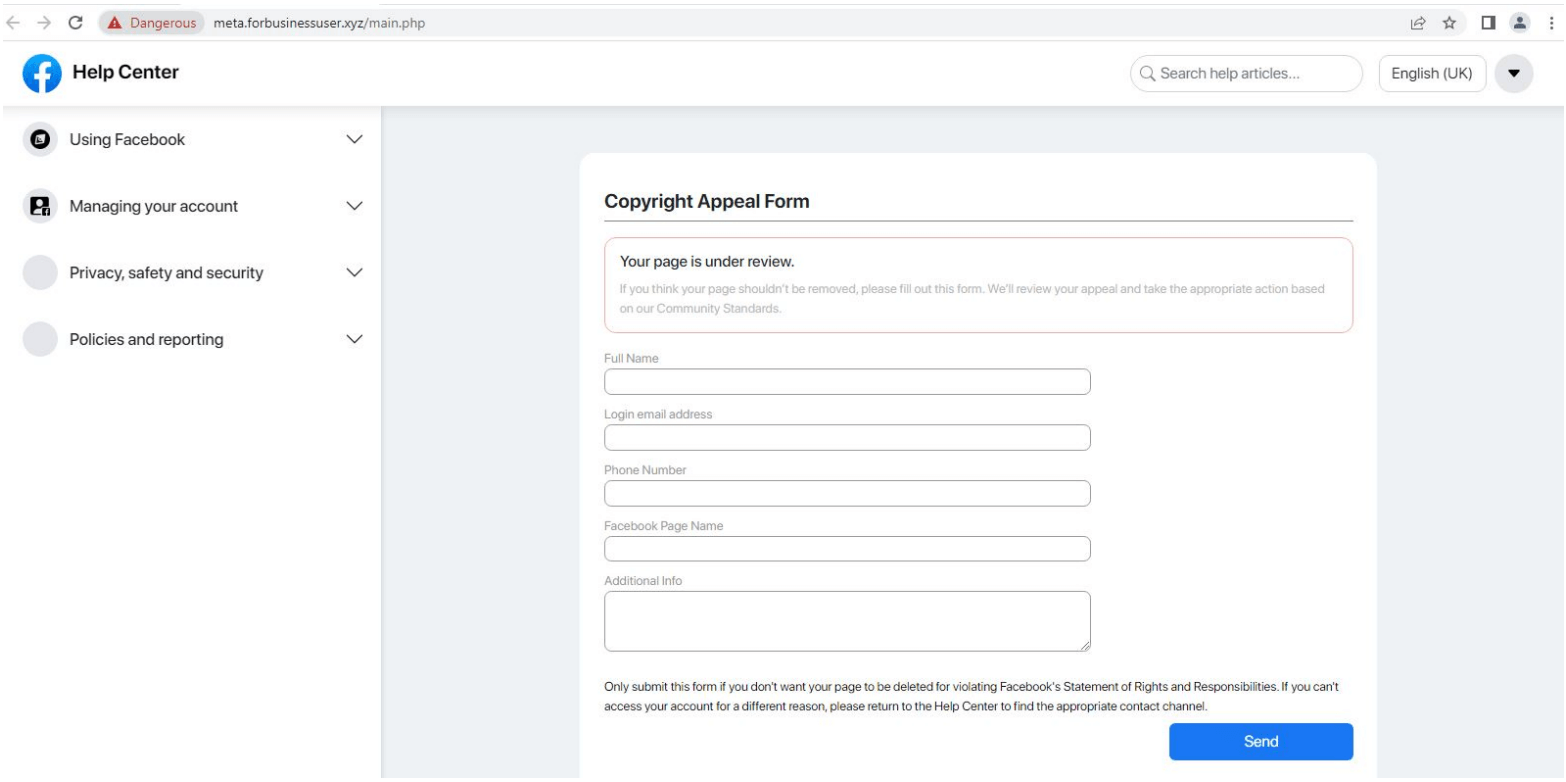
When a victim submits this data, the Telegram bot can collect their IP address and geolocation information before exfiltrating everything to a Telegram account under the threat actor’s control.
Suppose a malicious social engineer uploads a profile. In that case, they might try to collect additional information to bypass fingerprinting protections and security questions so they can take over the victim’s Facebook profile.
While the victim remains on the page, a redirect takes them to a fake 6-digit one-time password (OTP) request with a timer.
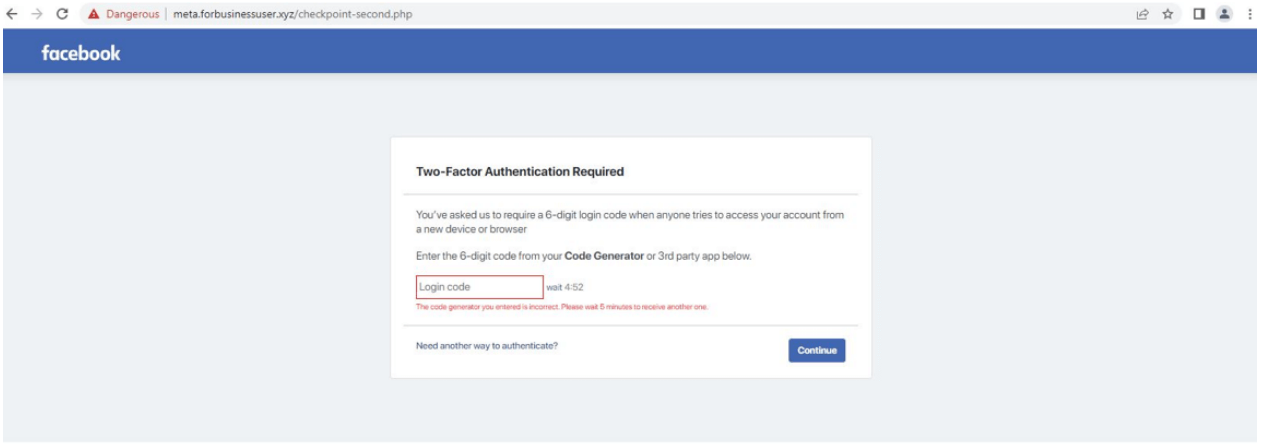
Any code entered by the victim will result in an error, and if the ‘Need another way to authenticate? ‘, the site redirects to the official Facebook site.
Trustwave’s analysts discovered that threat actors use Google Analytics on phishing pages to track their campaigns’ efficiency.
Widespread Technique
Trustwave has found various Facebook accounts making posts look like support pages that lead people to click a link to a phishing website.
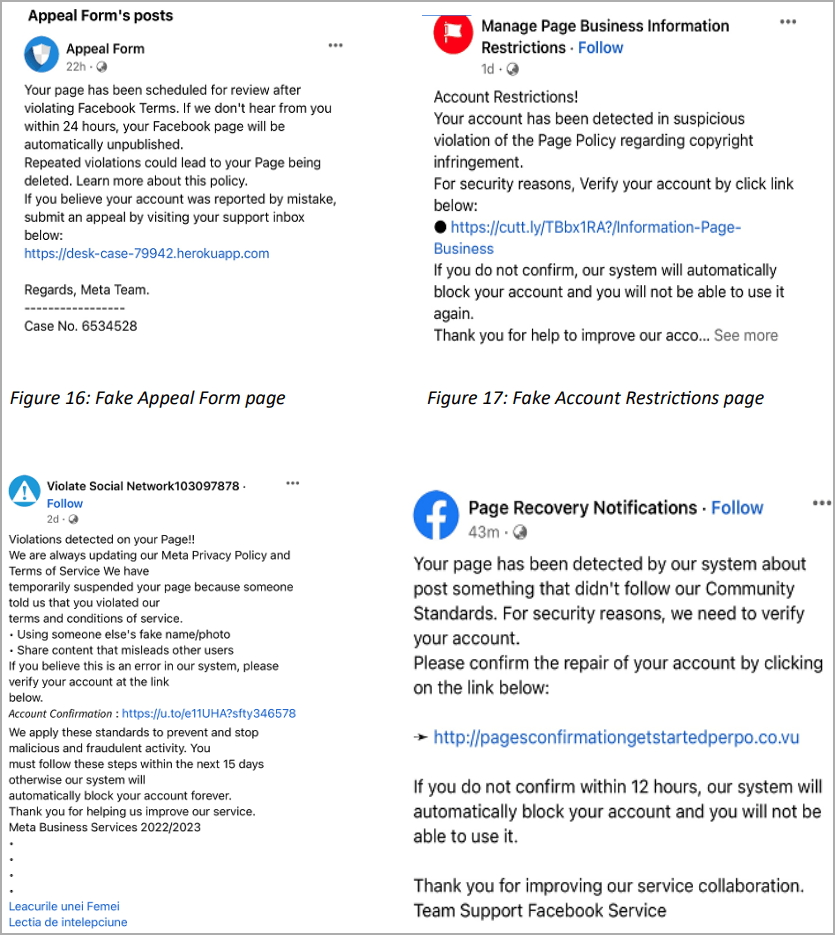
Unfortunately, some posts use URL shorteners when linking to questionable or phishing sites to avoid getting flagged and removed by the social media platform.
Phishing emails and instant messages on Facebook are some ways scammers target their victims with fake advertising posts.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








