Contents:
The Russian Advanced Persistent Threat (APT) group FIN7 is trying to break into the lucrative ransomware market by creating bogus cybersecurity organizations that perform network attacks under the pretense of pentesting (penetration testing), also known as ethical hacking.
What Is FIN7?
FIN7, also known as Carbanak, is a Russia-based APT that has been around since 2015, targeting American industries such as retail, restaurant, and hospitality. According to Wikipedia, FIN7 has been called one of the most successful criminal hacking groups worldwide.
Considering the fact that ransomware is more and more appealing for hackers and having prior experience with bogus front companies such as “Combi Security,” the FIN7 hacking group created a brand new organization to attract legitimate IT security professionals.
Security experts at Gemini Advisory found out that FIN7 is now running a new bogus business called “Bastion Secure”, replacing the previously reported “Combi Security”.
They also discovered that the newly created company’s website was made up of content belonging to other websites that was stolen and reorganized.
Following an examination of the fake company’s site, the experts discovered that its developers were Russia-based as most of the submenus of the website “return a Russian-language HTTP 404 error”. However, the company stated it is based out of England.
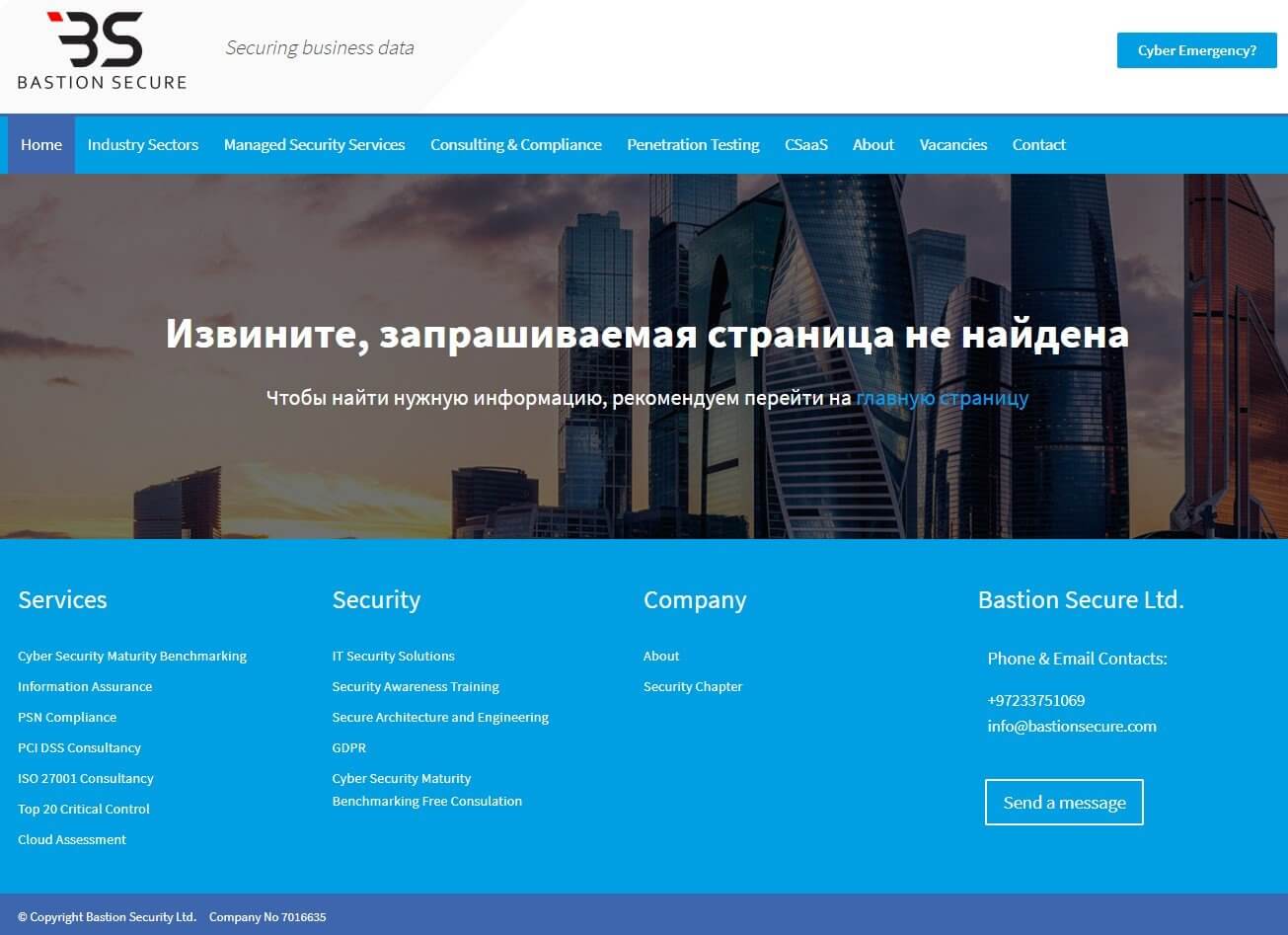
According to BleepingComputer, the fake company’s ‘About’ section asserts to be a spinoff of Convergent Network Solutions Ltd., a company that provides industry-leading cyber security through managed security services, penetration testing, and consulting.
We don’t know what Convergent Network Solutions Ltd. has to say about this as they didn’t make any comments yet.
Gemini researchers discovered that FIN7 was paying between $800 and $1,200 per month to hire IT professionals.
In the past several months, Bastion Secure has posted job offerings for system administrators on job search sites and added new vacancies for PHP, Python, and C++ programmers and reverse engineers on their website.
According to the researchers, the hacking group was looking for pentesters, as sysadmins would be able to map out affected corporate networks, carry out network reconnaissance, and detect backup servers and files.
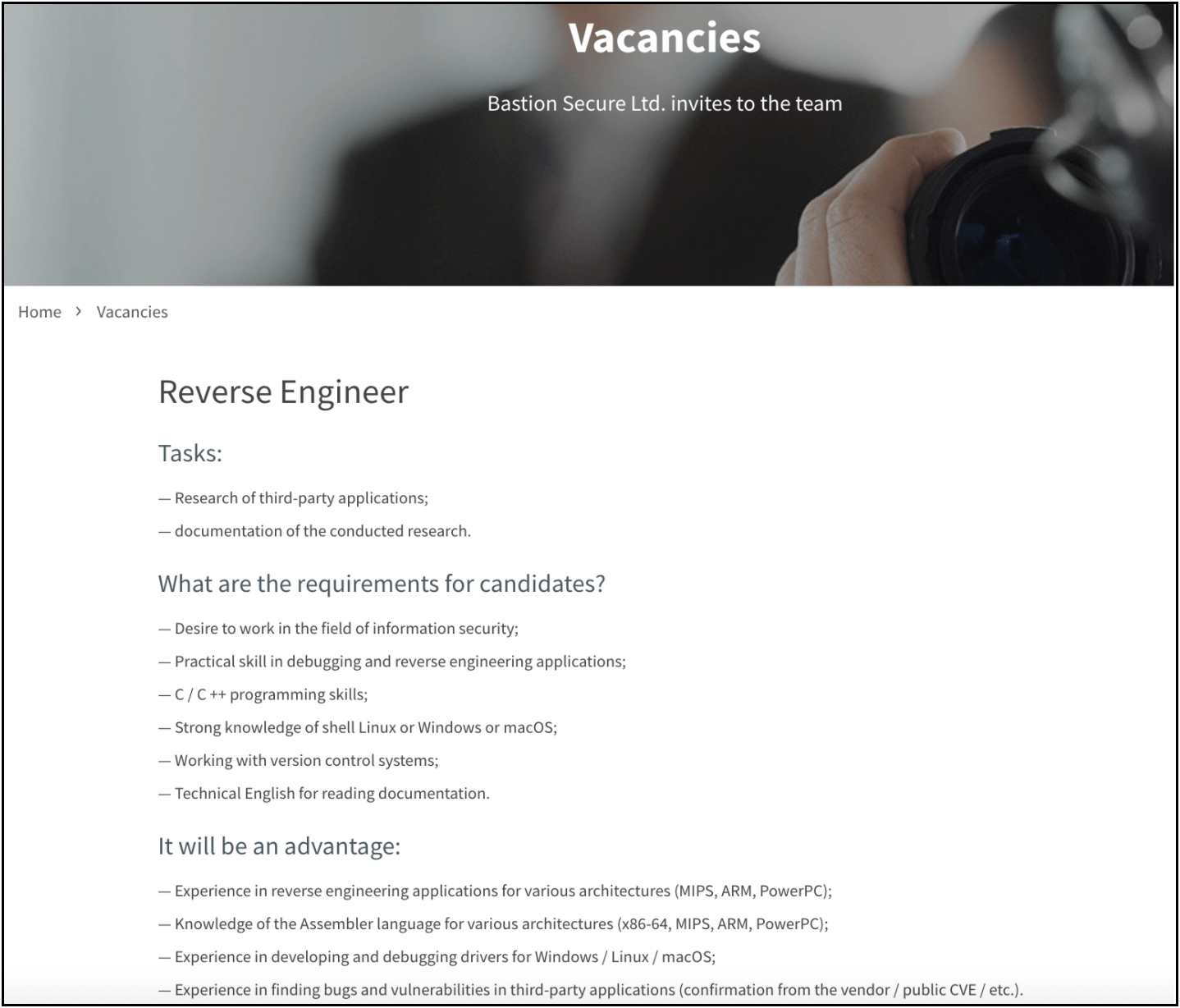
All these abilities are necessary for the pre-encryption phases of ransomware attacks, so it seems that this is what FIN7 hacking gang is searching for in the recruitment process.
To see what would happen, Gemini applied for a job at Bastion Secure and was employed, eventually gaining access to internal tools.
Bastion Secure provided the source with files for a software component named “Command Manager,” which was actually a camouflaged version of Carbanak’s client component.
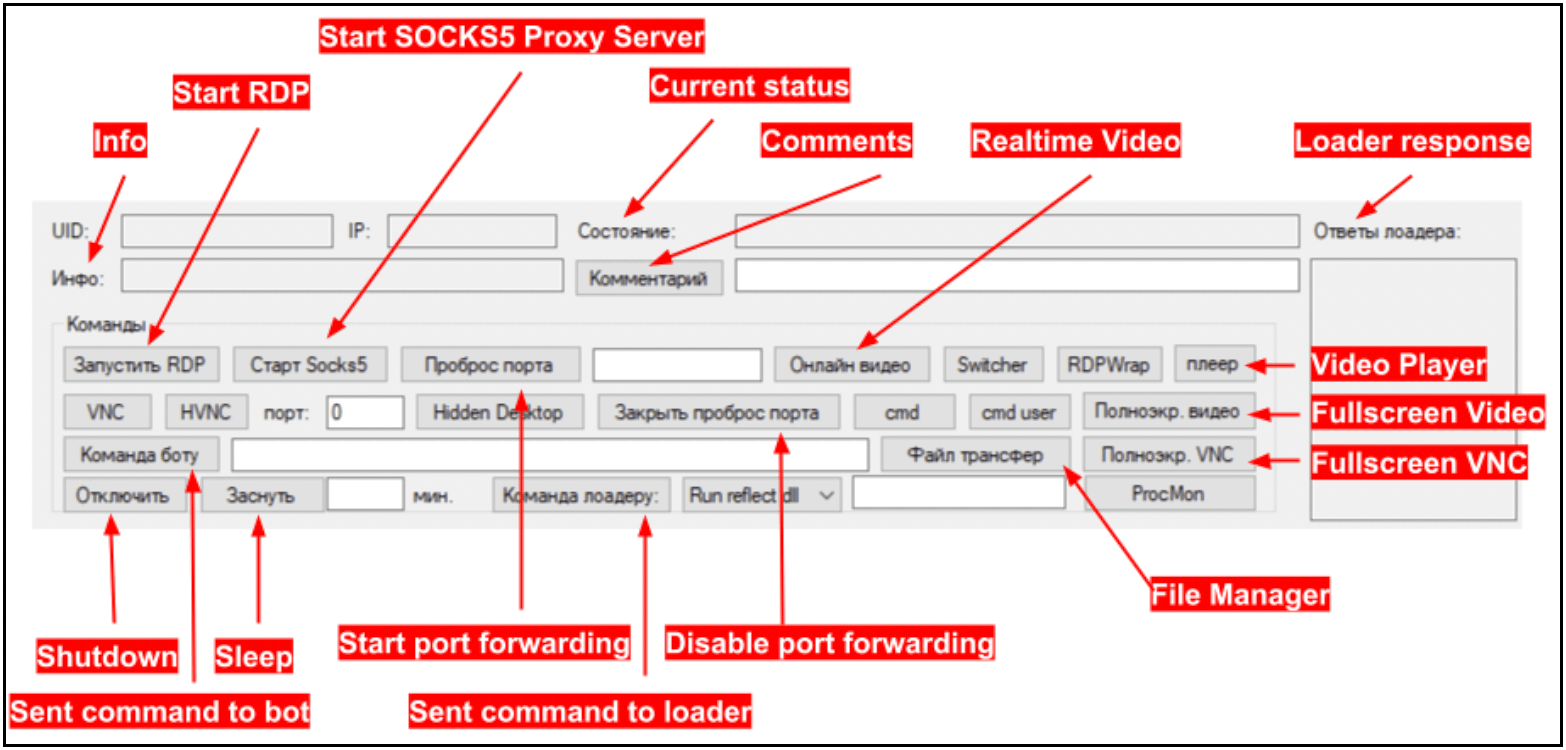
The Hiring Process
The hiring procedure was fairly standard, consisting of an interview, contract and non-disclosure agreement signing, and rudimentary training. Nevertheless, it became clear that Bastion Secure was searching for someone to conduct cybercriminal activity.
During the assignment, the new employee was instructed to gather, among others, data relevant to admin accounts, and backups from a company presented as a client who wanted pentesting services.
FIN7 cybercrime gang decided to create a bogus cybersecurity firm to recruit IT experts for its illegal activity being motivated by the company’s desire for a relatively inexpensive, skilled workforce.
Bastion Secure’s job offers for IT specialist positions ranged between $800 and $1,200 USD a month, which is a viable starting salary for this type of position in post-Soviet states.
However, this “salary” would be a small fraction of a cybercriminal’s portion of the criminal profits from a successful ransomware extortion or large-scale payment card-stealing operation.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








