Contents:
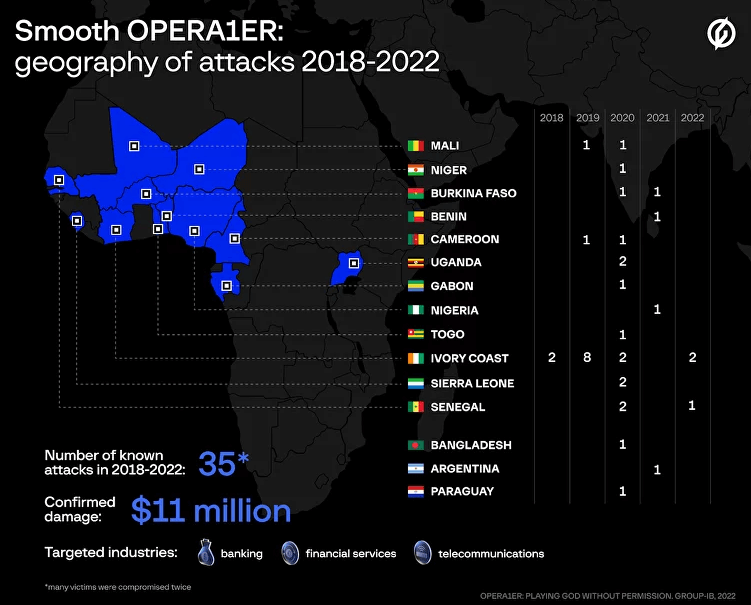
A new technical report published by Group-IB reveals that OPERA1ER, a French-speaking hacking group has stolen at least $11 million and successfully carried out over 30 attacks against banks, financial services, and telecommunications companies in Africa.
The attackers have set up a large network to withdraw stolen cash. One operation, for example, used a network of 400 mule accounts to execute fraudulent withdrawals.
Smooth OPERA1ER
The researchers revealed that OPERA1ER’s attacks began in 2018 and lasted until 2022. Ivory Coast, Mali, Burkina Faso, Benin, Cameroon, Bangladesh, Gabon, Niger, Nigeria, Paraguay, Senegal, Sierra Leone, Uganda, Togo, and Argentina are among the countries affected.
Group-IB researchers also added that many of the identified victims were successfully attacked twice, and their infrastructure was then exploited to target other companies.
Hackers Performed Extensive Research On their Victims
According to Cybernews, the operation’s threat actors used malware and hacking tools obtained from the dark web in combination with red teaming software such as Cobalt Strike and Metasploit.
Because the gang relies solely on public tools, they have to think outside the box: in one incident (…) OPERA1ER used an antivirus update server deployed in the infrastructure as a pivoting point.
The OPERA1ER hackers were also not in a hurry. The report shows that they infiltrated the victim’s system for three months to a year before attempting theft.
The time spent in their infrastructure was used for gathering internal documentation for future phishing attacks. Threat actors also examined how banks transit money in order to cash out stolen amounts without raising suspicions.
And interestingly enough, the operators thoroughly investigated their victims because the majority of them used a complex three-tiered digital money platform. To breach those systems, the operators needed to acquire significant knowledge about the operations and the key people.
The complete technical report on OPERA1ER is available here.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








