Contents:
Security experts in South Korea have discovered a new wave of activity from the Kimsuky threat actors, which includes the use of commodity open-source remote access tools delivered with their tailored malware, Gold Dragon.
What Is Kimsuky?
Kimsuky (also known as Velvet Chollima, Thallium, or TA406) is a state-sponsored cybercrime organization based in North Korea that has been active in cyber-espionage operations since 2017. However, the group has been around since 2012.
This hacking organization conducts espionage campaigns against South Korean think tanks, nuclear power companies, and the Ministry of Unification, an executive department of the South Korean government responsible for working towards the reunification of Korea.
The group has shown remarkable operational adaptability and threat activity diversity, partaking in:
- malware distribution,
- phishing operations,
- data gathering,
- cryptocurrency theft.
According to experts at ASEC (AhnLab), in the latest operation, Kimsuky employs xRAT in cyberattacks against South Korean organizations. The campaign began on January 24, 2022, and is still in progress.
What Is xRAT?
xRAT is a free open-source remote access and administration tool that can be found for free on GitHub. Keylogging, remote shell, file manager actions, reverse HTTPS proxy, AES-128 communication, and automated social engineering are among the features of the malware.
A more experienced cybercriminal may opt for commodity RATs because they are perfectly adequate for basic reconnaissance processes and don’t necessitate many configurations.
As explained by BleepingComputer, this allows attackers to concentrate their efforts on developing later-stage malware that necessitates more specialized functionality depending on the defense tools/practices available on the target.
Furthermore, commodity RATs merge with activity from a wide range of hacking organizations, making it difficult for security experts to attribute malicious activity to a specific group.
Now, More on the Gold Dragon Malware
According to malpedia,
GoldDragon is a second-stage backdoor which establishes a permanent presence on the victim’s system once the first-stage, file-less, PowerShell-based attack leveraging steganography is executed.
Gold Dragon is not a new malware, as it has been documented before; however, according to the ASEC report, the version they discovered in this recent campaign includes additional features such as the exfiltration of basic system data.
As per BleepingComputer, the backdoor does not use system processes for this function anymore but instead installs the xRAT tool to manually steal the needed data.
The RAT disguises itself as an executable called cp1093.exe, which replicates a regular PowerShell process (powershell ise.exe) to the “C:ProgramData”path, and performs via process hollowing.
In terms of operation, Gold Dragon keeps using the same process hollowing technique on iexplore.exe and svchost.exe, and it continues to try disabling real-time detection features in AhnLab AV products.
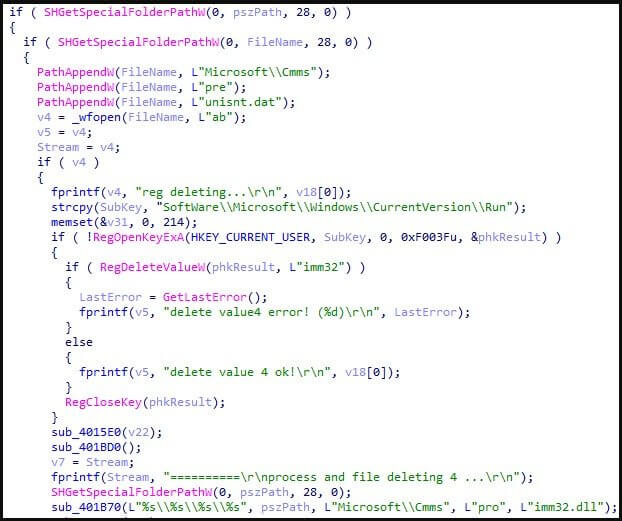
The attacker installed Gold Dragon through the exclusive installer (installer_sk5621.com.co.exe). The installer downloads Gold Dragon compressed in the form of a Gzip file from the attacker’s server, decompresses it as “in[random 4 numbers].tmp” in the %temp% path, then executes it via rundll32.exe.
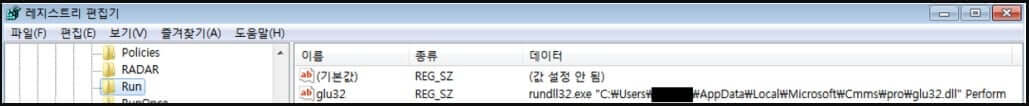
The installer then creates a new registry key to ensure the malware payload’s startup persistence (glu32.dll).
Kimsuky APT drops an uninstaller (UnInstall kr5829.co.in.exe) that can be used to remove the evidence of a compromise if necessary.
ASEC advises users to avoid opening attachments in emails from senders they don’t know, as this is still the most common way for Kimsuky to spread.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










