Contents:
In reply to EO (Executive Order) 14028 promulgated on the 12th of May 2021, the National Institute of Standards and Technology (NIST) has released a comprehensive guide on how institutions can protect themselves against supply chain attacks & compromise. The 326-paged document contains guidelines on software security evaluation, and best security practices for suppliers and developers, and highlights the latest methods and tools used to prove or improve security-related compliance.
NIST on Supply Chain Attacks – Key Takeaway(s)
As mentioned in the introduction, NIST’s guide on supply chain attacks is quite extensive, covering all functional areas of C-SCRM (Cybersecurity Supply Chain Risk Management). To help you navigate the document with efficiency, we’ve synthesized the key takeaways(s) of NIST’s guidelines. Of course, we do encourage you to go through the entire document (if time permits). Enjoy!
The paper is divided into three major sections: an introduction on the target audience, purpose, document use guidance, background, and audience profile, a second one on C-SCRM integration into enterprise-wide risk management, and the third one on critical success factors. Let’s jump in!
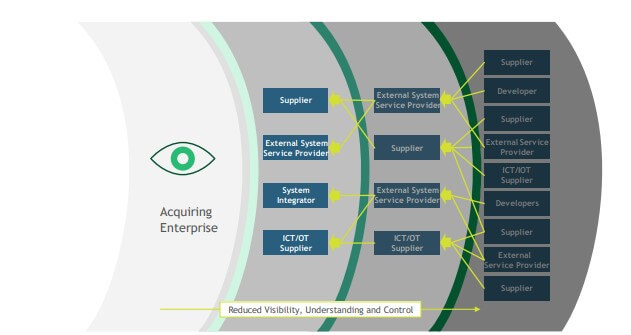
As far as section one’s concerned, the key takeaway here is the ability to understand the constitution and inherent dynamics of your company’s supply chain. You may find this information in sub-section 1.5.2 which is dedicated to the suppliers’ relationships within enterprises. Here’s also a visual representation of that statement.
Photo courtesy of NIST
For the second section, you need only concern yourself with the Risk Management process framework. NIST has identified four pillars to building a robust RMP. They are as follows:
- Frame risk. Establish the context for risk-based decisions and the current state of the enterprise’s information and communications technology and services and the associated supply chain.
- Assess risk. Review and interpret criticality, threat, vulnerability, likelihood, impact, and related information.
- Respond to risk. Select, tailor, and implement mitigation controls based on risk assessment findings.
- Monitor risk. Monitor risk exposure and the effectiveness of mitigating risk on an ongoing basis, including tracking changes to an information system or supply chain using effective enterprise communications and a feedback loop for continuous improvement.
In regards to the reasoning behind defining and implementing C-SCRM plans for supply chain attack prevention and mitigation, the paper goes on to say that:
Organizations should ensure that tailored C-SCRM plans are designed to:
- Manage rather than eliminate risk as risk is integral to the pursuit of value;
- Ensure that operations are able to adapt to constantly emerging or evolving threats;
- Be responsive to changes within their own organization, programs, and the supporting information systems; and adjust to the rapidly evolving practices of the private sector’s global ICT supply chain.
And now for part 3 which is the quintessence, if you will, of the entire NIST document. In section 3.5, the institution outlines the most important measures and strategies a company must enforce in order to operationalize the anti-supply chain attack framework. As a result, NIST has defined three levels of implementation called Foundational, Sustaining, and Enhancing.
To name just a couple of these best C-SCRM practices, on the Foundational tier we have policy enforcement across all the enterprise’s levels, defining roles, working out control baselines, transparency in disclosing vulnerabilities, and others. On the Sustaining tier, we have C-SCRM training programs, information-sharing workflows, risk tolerances & “appetite”, disaster recovery, contingency planning, and more. Last, but not least, on the Enhancing side we have adaptative C-SCRM strategies, process automation, and community feedback.
The entire document can be reviewed here.
Conclusion
NIST’s document might prove to be the tipping point of what is considered to be a silent war against supply chain attacks and compromise. One thing worth mentioning here – the document and its contents are descriptive, not prescriptive. Following NIST recommendations might help your company obtain missing compliance standards, but they are certainly not mandatory.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security