Contents:
Phishing scams are no longer just poorly written emails full of typos. The era of messages from long-lost, wealthy relatives leaving fortunes to unknown heirs has passed its peak.
Today’s sophisticated back-end technologies take phishing and social engineering to the next level. Hackers are now able to create not only better messages but also more convincing, harder-to-detect phishing websites.
Malicious sites look like almost perfect replicas of trusted, legitimate platforms. Advanced coding techniques, automated tools, and even AI usage give them better chances to steal sensitive information.
As cybersecurity measures evolved, so did the cybercriminals’ tactics.
In some cases, the danger lies in just how far hackers can push the back-end design of a phishing website to maximize deception. Here’s how this digital cat-and-mouse game progressed.
Why did mobile phishing get into the hackers’ focus?
Phishing messages initially arrived via email. Lots of them are now designed for mobile devices, from smishing to vishing and other specific techniques.
Hackers target mobile devices with phishing attacks because they’re most likely to succeed. Here are some of their strategic reasons:
Smaller screens, less scrutiny
Mobile screens limit the amount of visible information. They make it harder for users to spot suspicious URLs, missing security certificates, or design flaws that are obvious on a desktop.
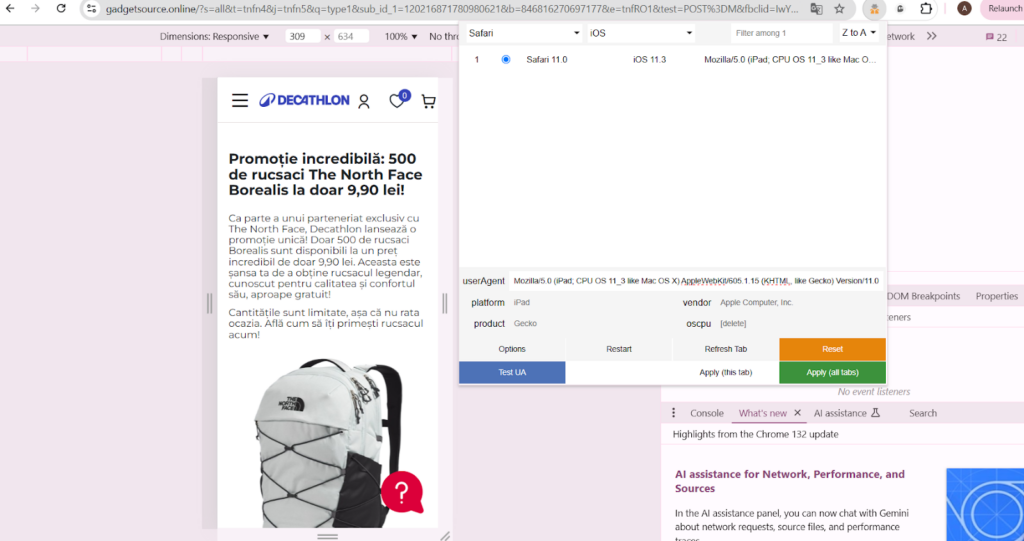
Desktop version:
Mobile version using a User Agent spoofer extension:
Mobile-specific features
Phishing sites can exploit mobile-specific features like SMS-based two-factor authentication (2FA), which is more vulnerable to interception or social engineering on mobile devices.
App imitation
Phishing attacks for mobiles can mimic legitimate apps or use fake login screens that look nearly identical to popular mobile apps, tricking users into entering sensitive information.
Faster, casual interaction
People often check emails, texts, and social media on the go, leading to quicker, less cautious responses. This impulsive behavior increases the likelihood of falling for a phishing scam.
Read more about how to identify a phishing email.
Limited security tools
Mobile devices often have fewer or less robust security tools compared to desktops, and many users don’t install additional security apps, leaving them more exposed.
Access to valuable data
Mobile devices store a wealth of personal information, from banking apps to contact lists. This data can be easily exploited or sold once the device is compromised.
So, by focusing on mobiles, hackers can increase the success rate of their phishing campaigns.
Beyond targeting mobile vulnerabilities, hackers have also refined the psychological tricks behind phishing scams.
Next-gen phishing techniques
Crafting the perfect phishing attack got more challenging as people grew aware of online scams. To stay in business, phishers became more creative and craftier, while still relying on psychological tricks to lure victims.
One common tactic is to simulate a game or contest to create a false sense of excitement or luck. Here’s how it goes:
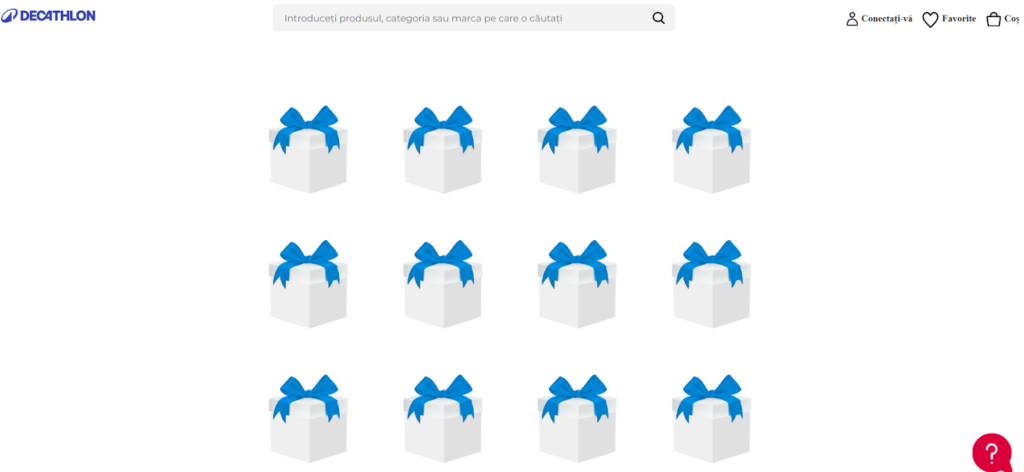
Step 1 – The bait
Hackers present an interactive game where you should choose between a number of boxes, believing only one contains a prize.
This playful approach aims to make you lower your guard. It’s more likely that you’ll engage and provide sensitive information, under the illusion of a harmless game or unexpected win.
Step 2 – The hook
You pick the first box and feel slight disappointment to see it’s empty. But on your final chance, you suddenly win. The thrill of winning lowers your guard, making you more likely to proceed. The malicious actors carefully craft this moment. Now your defense is at its lowest and the excitement of winning brings a false sense of trust.
Step 3 – The theft
Once that trust is established, the phishing site can seamlessly starts collecting your personal information. It will only feel like one more step in claiming your “prize.”
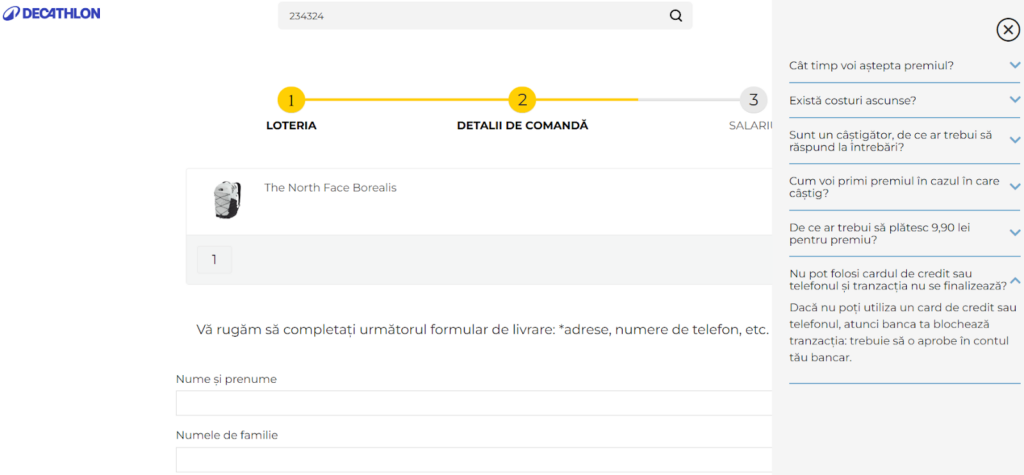
Stealing Data in Real Time
What makes these next-gen phishing attacks even more dangerous is how efficiently stolen data is harvested and processed.
As you begin entering your details: name, email, credit card information, or login credentials, the data is transmitted in real time to the attackers’ servers. There’s no need for any additional clicks or confirmations.
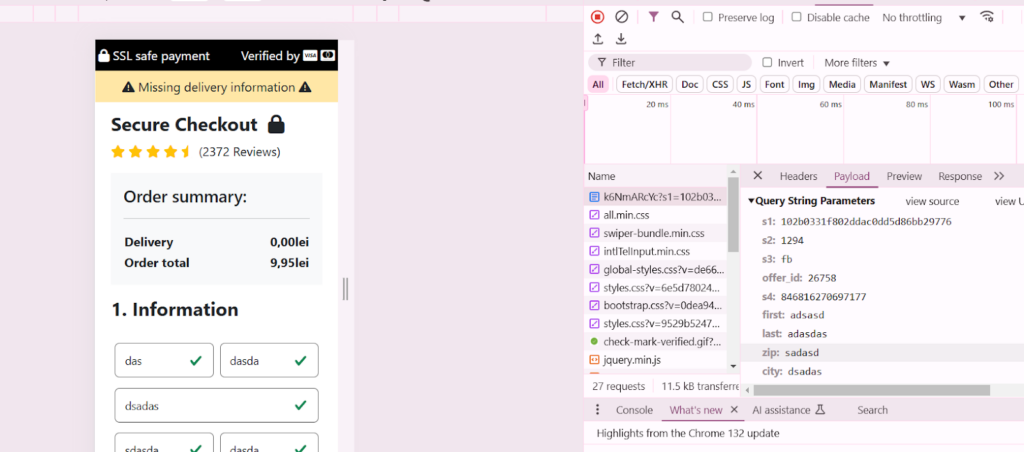
This live data transfer ensures that even if you start to second-guess the situation and abandon the process midway, the hackers already have whatever information you’ve entered up to that point. It doesn’t matter whether you’ve hit the “Submit” button or not.
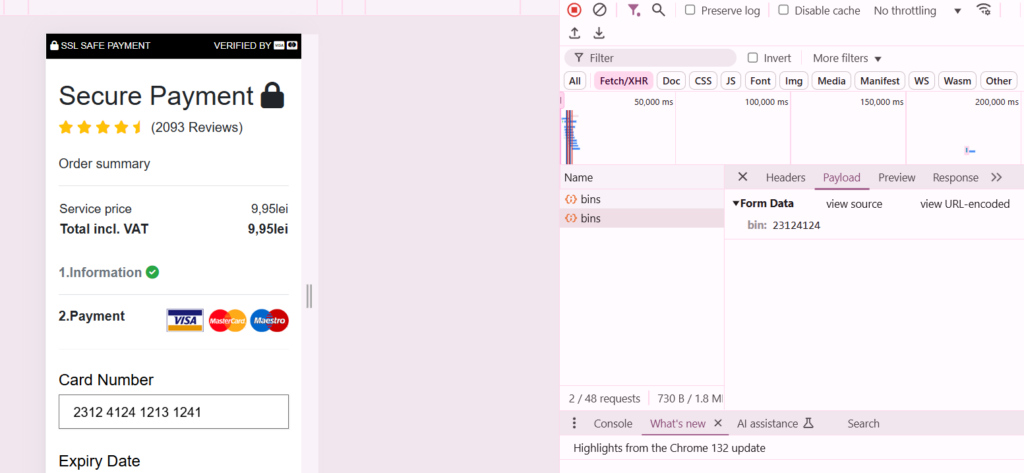
This is how threat actors minimize their risk of losing valuable data to a hesitant victim and get the most out of their scam. To sum it up, while you type in your credit card information to cash in the prize, phishers use JavaScript to capture the data as you type it. The method needs no additional clicks or confirmation from the user.
This technique leverages a potential browser vulnerability. Many mobile browsers will automatically complete requested information. So, it will be even easier for attackers to capture sensitive data without you being aware of the scam.
Final thoughts
Modern phishing websites are powered by advanced backend technologies that make them nearly indistinguishable from real platforms. Combined with psychological manipulation and real-time data capture, these scams are more effective than ever.
To stay safe, you must remain cautious, verify website authenticity, and be skeptical of any site requesting sensitive information—especially when an offer seems too good to be true.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security