Contents:
Recently a public exploit for the major zero-day vulnerability known as ‘Log4Shell’ in the Apache Log4j Java-based logging platform has been made available.
Log4j is a development platform that enables developers to include error and event logging into Java applications.
Threat actors can exploit the vulnerability by generating unique JNDI strings that, when read by Log4j, force the platform to connect to and execute code at the provided URL. This makes it simple for attackers to discover susceptible devices and execute code given by a remote site or via Base64 encoded messages.
What Happened?
Researchers have identified the first public incidence of the Log4j Log4Shell vulnerability being leveraged to download and install malware.
While this vulnerability was patched in Log4j 2.15.0 and even hardened further in Log4j 2.16.0, threat actors are still using it to install malware such as currency miners, botnets, and even Cobalt Strike beacons.
BitDefender researchers discovered the first ransomware family being installed directly using Log4Shell vulnerabilities.
While most of the attacks observed so far seem to be targeting Linux servers, we have also seen attacks against systems running the Windows operating system. For these attacks, we have detected the attempt to deploy a ransomware family called Khonsari.
This attempt to exploit the Log4j vulnerability uses the malicious hxxp://3.145.115[.]94/Main.class class to download an additional payload. On Sunday, 11th December, Bitdefender observed this payload as a malicious .NET binary file download from hxxp://3.145.115[.]94/zambo/groenhuyzen.exe. This is a new ransomware family, called Khonsari after the extension used on the encrypted files.
Once executed, the malicious file will list all the drives and encrypt them entirely, except the C:\ drive. On the C:\ drive, Khonsari will encrypt only the following folders:
- C:\Users\<user>\Documents
- C:\Users\<user>\Videos
- C:\Users\<user>\Pictures
- C:\Users\<user>\Downloads
- C:\Users\<user>\Desktop
Files with the extensions .ini and .lnk are ignored. The algorithm used for encryption is AES 128 CBC using PaddingMode.Zeros. After encryption, the extension .khonsari is added to each file.
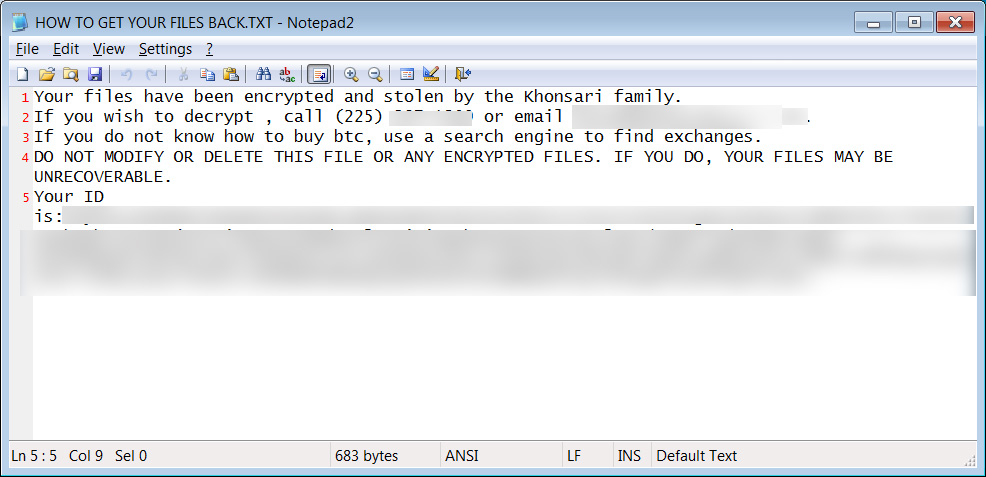
A ransom note is written in C:\Users\<user>\Desktop\HOW TO GET YOUR FILES BACK.TXT and opened with Notepad:
Your files have been encrypted and stolen by the Khonsari family.If you wish to decrypt , call (225) 287-1309 or email karenkhonsari@gmail.com.If you do not know how to buy btc, use a search engine to find exchanges.DO NOT MODIFY OR DELETE THIS FILE OR ANY ENCRYPTED FILES. IF YOU DO, YOUR FILES MAY BE UNRECOVERABLE.
There is also a GET request to hxxp://3.145.115[.]94/zambos_caldo_de_p.txt. The response is not used in the binary code, and our hypothesis is that the GET request is performed for logging and monitoring purposes.
In later attacks, BitDefender noticed that this threat actor used the same server to distribute the Orcus Remote Access Trojan.
According to BleepingComputer, the researcher Michael Gillespie stated that Khonsari employs legitimate encryption and is safe, implying that free file recovery is not feasible, but it’s important to note that the ransom note has one peculiarity: it does not appear to offer a mechanism to contact the threat actor in order to pay the ransom.
Because Microsoft has previously seen the exploits used to distribute Cobalt Strike beacons, it is probable that more sophisticated ransomware operations are already employing the exploits as part of their assaults.
How Can Heimdal™ Help?
In the fight against ransomware, Heimdal™ Security is offering its customers an outstanding integrated cybersecurity suite including the Ransomware Encryption Protection module, that is universally compatible with any antivirus solution, and is 100% signature-free, ensuring superior detection and remediation of any type of ransomware, whether fileless or file-based (including the most recent ones like LockFile).
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








