Contents:
A new financially motivated campaign is actively targeting vulnerable SSH servers to covertly ensnare them in a proxy network. According to researchers, the attackers leverage SSH for remote access, thus running malicious scripts that stealthily enlist victim servers into a peer-to-peer (P2P) proxy network.
Proxyjacking Explained: The Dangers Behind the Practice
Unlike cryptojacking, in which a compromised system’s resources are used to illicitly mine cryptocurrencies, proxyjacking gives threat actors the opportunity to use the victim’s spare bandwidth to secretly operate various services as a P2P node.
Proxyjacking offers attackers two advantages: it not only makes it possible for the attacker to make money off the extra bandwidth with a far lower resource burden than would be required to carry out cryptojacking, but it also lessens the likelihood of being discovered.
Even worse, threat actors may leverage proxyware services’ anonymity to hide the origin of their assaults by routing traffic through middle nodes, which is a double-edged sword that makes the situation worse.
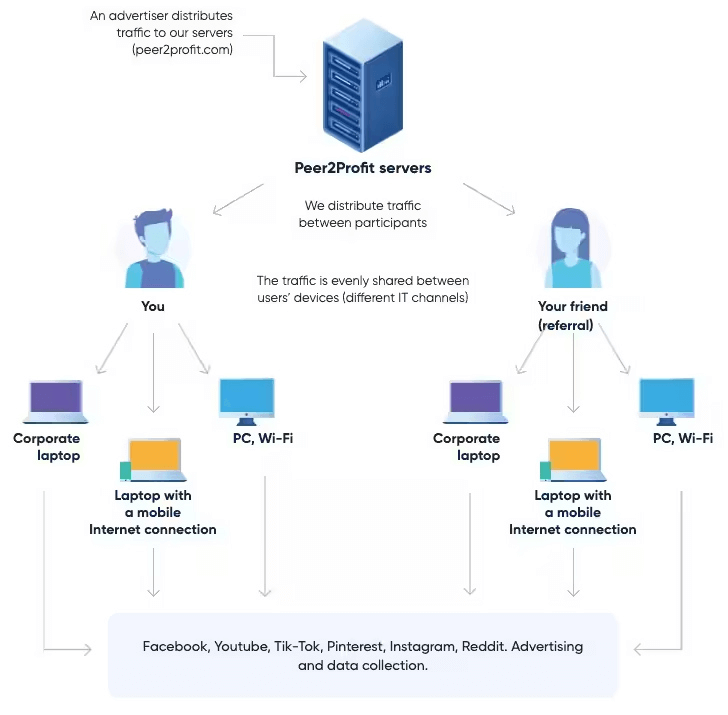
How a Proxyjacking Campaign Works (Source)
Akamai, which discovered the latest campaign on June 8, 2023, said the activity is designed to breach susceptible SSH servers and deploy an obfuscated Bash script that, in turn, is equipped to fetch necessary dependencies from a compromised web server, including the curl command-line tool by camouflaging it as a CSS file (“csdark.css”).
Before establishing Docker services that monetize the victim’s bandwidth sharing, the stealthy script first actively hunts for and kills competitor instances running bandwidth-sharing services.
The fact that the web server is also being used to run a cryptocurrency miner indicates that the threat actors are interested in both cryptojacking and proxyjacking attacks, according to further investigation of the machine.
Proxyware is not by nature malicious, but according to The Hacker News, researchers say that some of these companies do not properly verify the sourcing of the IPs in the network, and even occasionally suggest that people install the software on their work computers.
However, when the programs are installed without the users’ knowledge or consent, the operations go into the area of cybercrime. This enables the threat actor to take over multiple systems and make illegal profits.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and Youtube, for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








