Contents:
A new META malware, an info-stealer that seems to be more and more popular among hackers, has been discovered being leveraged by threat actors in a recent malspam campaign.
What Is Meta Malware?
META, along with Mars Stealer and BlackGuard, is one of the new info-stealers whose owners reportedly hope to profit from Raccoon Stealer‘s absence from the market.
Info about META came last month when KELA experts cautioned of its quick entry into the TwoEasy botnet marketplace.
The product is advertised as an upgraded version of RedLine and costs $125 per month for monthly users or $1,000 for unrestricted lifetime use.
More Details on the Recent Malspam Campaign
META is currently being utilized in cyberattacks in a recent malspam campaign, according to security researcher and ISC Handler Brad Duncan. It is being used for passwords stored in Chrome, Edge, and Firefox theft purposes, as well as to steal cryptocurrency wallets, the BleepingComputer publication reports.
The infection chain in this campaign uses the “conventional” approach of sending a macro-laced Excel spreadsheet as an email attachment to potential victims’ inboxes.
Since Wednesday 2022-03-30, at least 16 samples of a specific Excel file have been submitted to VirusTotal. These malicious Excel files are distributed as email attachments. Post-infection traffic triggers signatures for Win32/MetaStealer Related Activity from the EmergingThreats Pro (ETPRO) ruleset. This infection process uses data binaries to create the malicious EXE and DLL files used for the infection. The malware abuses legitimate services by Github and transfer.sh to host these data binaries. All URLs, domains, and IP addresses were still active for the infection approximately 3 hours before I posted this diary.
A representation of the META infection chain can be seen below:
ISC Diary: @malware_traffic reviews new #MetaStealer malware first seen on 2022-03-30 https://t.co/Zt9q6pmzHe pic.twitter.com/1561uSr7WK
— SANS ISC (@sans_isc) April 6, 2022
The communications make fictitious financial transfer promises that aren’t very persuasive or well-crafted, yet they can nonetheless convince some recipients.
A DocuSign bait is included in the spreadsheet files, urging the target to “allow content” in order to launch the malicious VBS macro in the background.
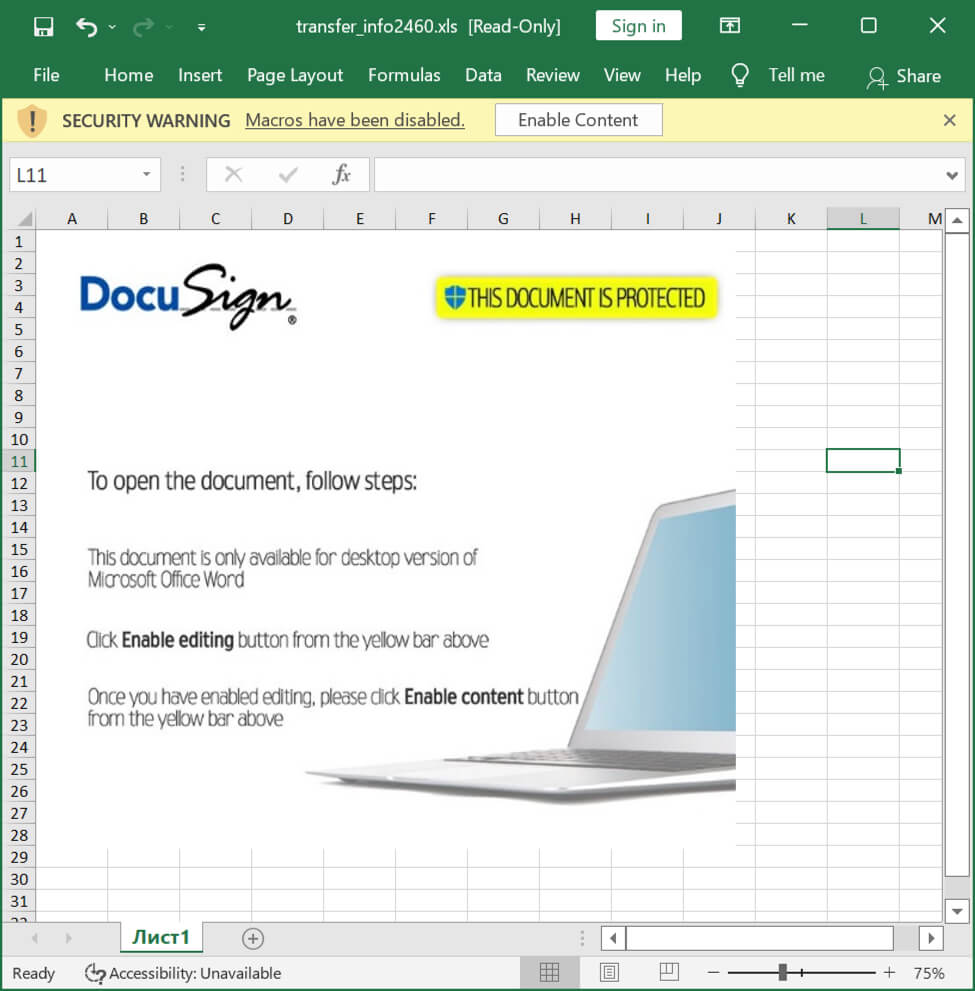
What happens if the malicious script is launched, is that it will download several payloads from various domains, including GitHub, DLLs, and executables.
To avoid detection by the security software, some of the downloaded files are base64 encoded or have their bytes inverted.
The full payload is eventually constructed on the machine under the name “qwveqwveqw.exe,” which is most likely random, and a new registry entry for persistence is created.
The EXE file generating communication to a command and control server at 193.106.191[.]162, even after the system reboots, represents obvious and persistent infection evidence, restarting the infection process on the compromised machine.
In his report, Brad Ducan also depicted the traffic generated by an infection filtered in Wireshark.
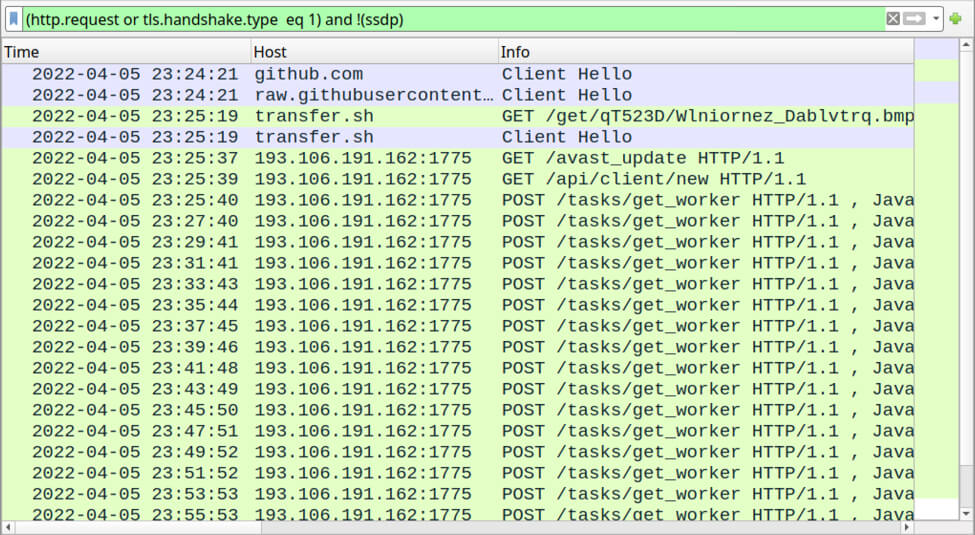
It’s also worth mentioning that META uses PowerShell to tell Windows Defender to ignore.exe files in order to protect its files from detection.
Duncan has made the PCAP of the infected traffic available here if you’d want to find more details on the particularities of the captured malicious traffic.
Brad Duncan also mentioned that
Each time I rebooted my infected Windows host, the persistent EXE generated traffic to the same transfer.sh URL and re-started the infection process without the Github traffic. Malware associated with this infection was first submitted to VT on Wednesday 2022-03-30. ETPRO signatures identifying HTTP traffic generated by this malware as MetaStealer were released on Friday 2022-04-01.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










