Contents:
After being sanctioned by the US Treasury Department’s Office of Foreign Assets Control (OFAC) for using Dridex to cause more than $100 million in financial losses, Evil Corp gang members began renaming their ransomware operations to different names such as WastedLocker, Hades, and Phoenix to avoid these sanctions.
Also known as the Dridex gang or INDRIK SPIDER, the Russian cybercriminal gang Evil Corp has been active since at least 2007 and is known for distributing the Dridex malware.
Recently, as discovered by BleepingComputer, Evil Corp launched a ransomware operation dubbed BitPaymer, which was delivered via the Dridex malware in compromised corporate networks.
After claiming responsibility for the attack on the Metropolitan Police Department, the Babuk gang said they were quitting ransomware encryption and instead focus on data theft and extortion.
On June 1st, MalwareHunterTeam took to Twitter that the Babuk data leak site had a design refresh where the ransomware gang rebranded as a new group called “payload bin”.
Babuk’s leak site / blog became “Payload.bin” as they announced some weeks ago (https://t.co/KG51KnG3lb).
The “about us” and “our rules” pages only says “Coming soon” for now… pic.twitter.com/zVlfxYiwFR— MalwareHunterTeam (@malwrhunterteam) June 1, 2021
Following the news, BleepingComputer found a new ransomware sample dubbed PayloadBIN which is related to the Babuk Locker rebranding.
When installed, the ransomware will append the .PAYLOADBIN extension to encrypted files, as shown below.
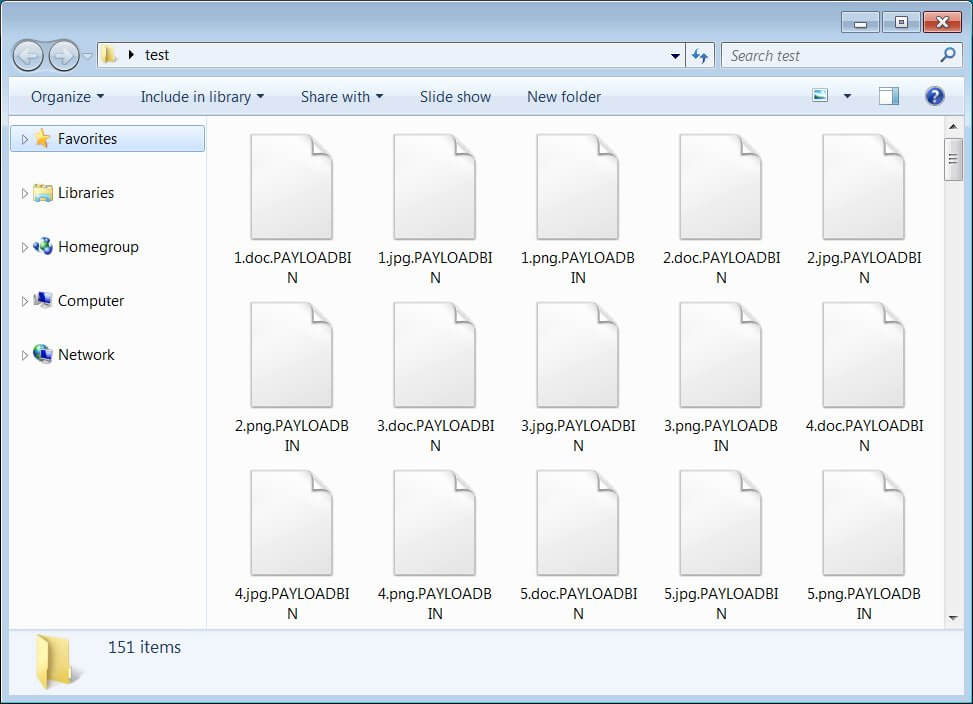
Image Source: BleepingComputer
The ransom note is named ‘PAYLOADBIN-README.txt’ and states that the victim’s “networks is LOCKED with PAYLOADBIN ransomware.
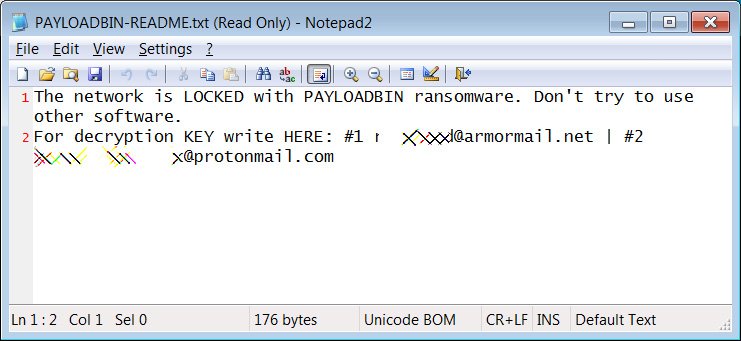
Image Source: BleepingComputer
Although all the evidence suggested Babuk was lying about their intentions to step down from ransomware, ID Ransomware and Emsisoft researchers Michael Gillespie and Fabian Wosar confirmed that the ransomware is in fact a rebranding of Evil Corp’s former ransomware operations.
Looks like EvilCorp is trying to pass off as Babuk this time. As Babuk releases their PayloadBin leak portal, EvilCorp rebrands WastedLocker once again as PayloadBin in an attempt to trick victims into violating OFAC regulations. Sample: https://t.co/k669bbaNyV
— Fabian Wosar (@fwosar) June 5, 2021
WastedLocker -> Hades -> Phoenix -> PayloadBin, all same malware/group behind it. Probably a few in-between don’t care to recall at the moment.
— Michael Gillespie (@demonslay335) June 5, 2021
Since the ransomware is now attributed to Evil Corp, most ransomware negotiation firms won’t help facilitate payments for victims affected by the PayloadBIN ransomware.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








