Contents:
New research conducted by a Dutch mobile security company recently discovered a network of phishing websites targeting Italian online-banking users to get a hold of their credentials.
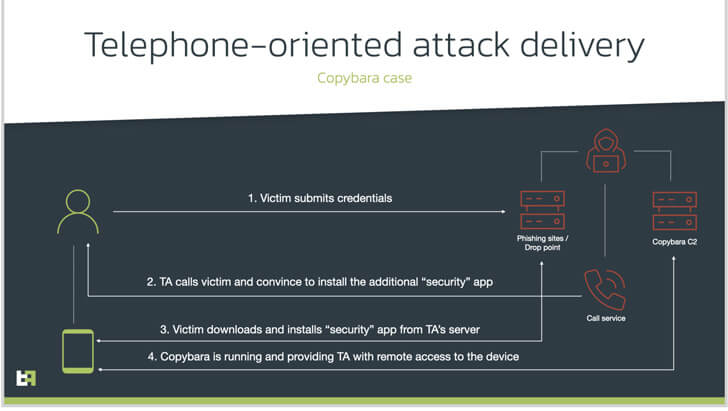
Hackers are using a social engineering approach called TOAD, also known as ‘telephone-oriented attack delivery’ that includes calling the victims and using information gathered from malicious websites.
How Did the Attacks Happen?
Like in any vishing, using the information they have on their subject, the fraudsters claim to be bank assistance agents who call with the purpose of helping the person on the other end of the line install a security app and convince them to grant it multiple permissions. Alas, the ‘security app’ is actually malware designed to get remote access or commit financial fraud.
The malware in question is called ‘Copybara’, an Android malware that was originally discovered in November 2021 and is mostly used to execute on-device fraud through overlay attacks against Italian users. ThreatFabric, the security company who discovered the malware, determined that the TOAD-based campaigns also began in November 2021, which means the activity has been ongoing for almost a year, according to Hacker News.
The user is asked to install a downloader application that will download the actual payload as an entrance point for fraudsters. The payload is then installed as an update for the downloader, replacing it.
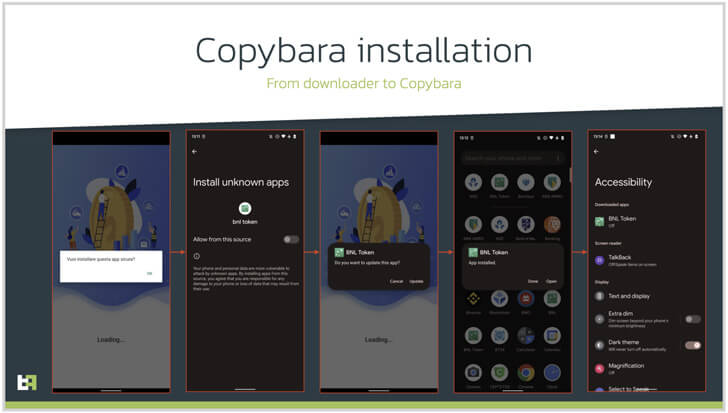
Copybara’s Capabilities
The Android malware’s capabilities are pretty much the same as any other malware, fueled by abusing the operating system’s accessibility services API to capture sensitive information and even remove the downloader app to minimize its forensic footprint.
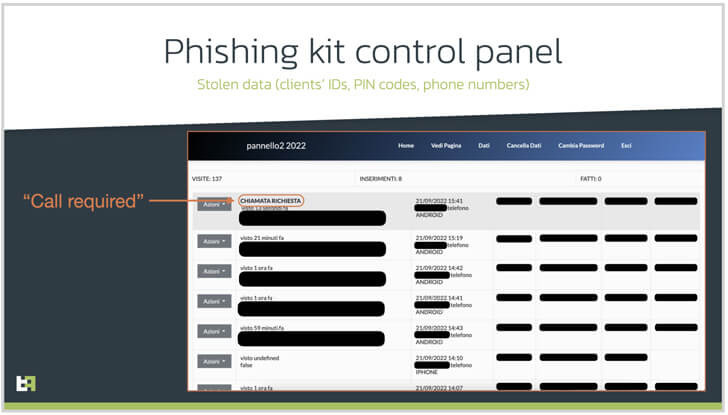
Furthermore, the threat actor’s infrastructure seems to be able to transmit a second malware called ‘SMS Spy’, which the hacker uses to obtain access to incoming SMS messages and intercept one-time passwords (OTPs) supplied by banks.
“Such attacks require more resources on [threat actors’] side and are more sophisticated to perform and maintain. Financial organizations should provide their customers with knowledge about ongoing campaigns and enhance the client apps with mechanisms to detect suspicious activity”, stated ThreatFabric’s Mobile Threat Intelligence (MTI).
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








