Contents:
A new type of malware rends the air in the cybersecurity world. A security flaw in Microsoft’s system allowed the distribution of a driver infected with Netfilter rootkit malware in the gaming environment. The matter was firstly reported last week by G Data Global analysts. Now, the threat has been confirmed and Microsoft admitted mistakenly signing the malicious driver.
What Is a Netfilter Rootkit Malware?
A rootkit is made up of two words: root and kit. The root stands for Windows Administrator. Kits are basically software programs that can take over a personal computer without previously noticing the user. These together Linux terms merge into a rootkit, which, once installed on the PC, can perform several actions such as traffic scanning, tracking every step of the user, or resource hijacking. In other words, using rootkit malware, cybercriminals can perform keylogging or remote control of the computer leading to confidential data collection. In this case, the malware-infected driver was named “Netfilter”.
Who Is Behind This Netfilter Rootkit Malware Attack?
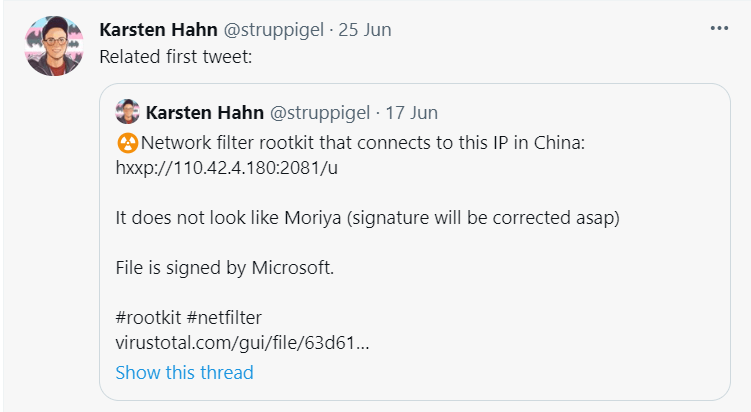
The first to notice this issue was Karsten Hahn, a malware analyst from G Data, the German software company. The Netfilter rootkit malware indicated communication with Chinese command-and-control (also known as C2) IPs. The lack of the rootkit’s dependable performance led to Mr. Hahn making his observation public and informing Microsoft. Then, a whole process of investigation from all sides has started.
WHOIS, the query protocol also indicated that the IP with which the Netfilter rootkit malware communicates is a C2 IP from Ningbo Zhuo Zhi Innovation Network Technology Co., Ltd.
How Does This Netfilter Rootkit Malware Action?
Takahiro Haruyama, Johann Aydinbas, Florian Roth, and the above-mentioned Karsten Hahn worked together in providing an analysis of the malware’s functionality on their report on the company’s blog website and also made up a list of samples shared publicly in a spreadsheet.
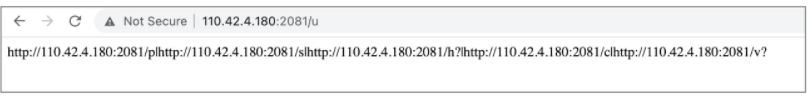
According to BleepingComputer, the behavior of the C2 URLs that communicate with the rootkit driver was observed by analyst Hahn and can be traced in the below steps:
- The “|” symbol separates several URLs returned by the C2 URL indicating more routes;
- Every URL has a different ending that points out to a different action: proxy settings and “/p” are related, the “/s” points out to IPs of encoded redirection, the “/h?” receives the CPU-ID, the “/c” furnishes a root-certificate and “/v?” leads to the rootkit itself.
The driver self-update functionality implies some stages: the server sends the URL to the latest sample, then the rootkit malware acts and replaces its files.
Microsoft declared:
The actor submitted drivers for certification through the Windows Hardware Compatibility Program. (..) The malware enables them to gain an advantage in games and possibly exploit other players by compromising their accounts through common tools like keyloggers.
What Measures Have Been Taken?
The appearance of the Netfilter rootkit malware under the seal of Microsoft was possible through the Windows Hardware Compatibility Program (WHCP), as Engadget mentions. Because of the reason that every code that runs in kernel mode should be signed before release with the new Windows Vista updates, it was easier for threat actors to action with a fake licensed-rootkit malware. Thus, Microsoft was tricked into signing this malicious driver. The distributed driver was sent by a third party, emphasizing the threat of supply chain attacks.
Microsoft took the necessary measures. They will provide better policies in terms of signing, access, and validation.
The company ensures to roll out a new update with fresh drivers to remove the existence of rootkit from the affected systems. Anyhow, a company’s signed software means that the update is verified and the software driver is safe to download but this mistake by Microsoft can cost the company, its trust with the customers.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








